
In a growing digital world, the need for IT pros who are passionate about cybersecurity continues to grow. Jumping into a new IT career path is equally exciting and nerve-wracking, but as a novice IT pro, did you know that you may already have the baseline skills needed to begin a cybersecurity-specific IT career?
There are so many IT skills out there, how do IT pros weed through them all? A recent CompTIA cybersecurity research study revealed the cybersecurity skills IT pros need to build their knowledge base and ultimately, their careers.
Foundational Cybersecurity Skills
Many of the foundational skills needed for cybersecurity are found in entry-level IT jobs such as help desk technician, technical support specialist or network support specialist. Though the cybersecurity industry has evolved and there are ways to launch your IT career directly into the specialty, beginning in a general IT job is still a great way to build your cybersecurity skills.

Specifically, three foundational skills come early in a cybersecurity career:
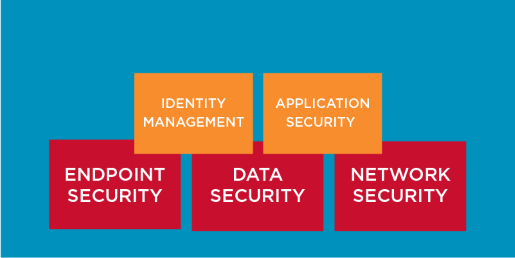
Endpoint Security
Endpoint devices are items like laptops, mobile devices, tablets and desktop computers, and these types of devices are operated by employees at your organization at all hours of the day. Ensuring that endpoint devices have a layer of protection and that employees have cybersecurity training is a common task for help desk professionals.
Data Security
Data security is a skill that IT pros need to protect their organization’s high-profile data. Taking care of vital data to keep it away from unauthorized users and cyberattacks is something that IT pros need to know how to do early in their careers.
Network Security
Networking is what keeps devices connected. Without networks, organizations can’t communicate relevant information and collaborate together. Large networks leave organizations susceptible to security risks and therefore need to operate with the highest level of security.
Mid-range Cybersecurity Skills
Moving up on the building blocks are mid-range skills that are necessary for intermediate cybersecurity jobs such as application security analyst, penetration tester or cybersecurity engineer.
Skills like the following can separate you from other IT pros who have less cybersecurity experience:
Identity Management
Identity management is a structured set of rules that ensure that the individuals in different departments, teams or levels of seniority at an organization have the appropriate and designated access to certain resources within the organization. In other words, this means making things available on a need-to-know basis. Only the people who need access have access.
Application Security
Application security aides in preventing hacks and cyberattacks to applications and programs throughout the software development lifecycle (SDLC). It combines development skills with cybersecurity and is crucial to an organization’s IT department. This is the primary skill used by application security analysts but can also be found in DevOps or general development roles.
Advanced Cybersecurity Skills
The top level of cybersecurity skills includes those that are most advanced since they address issues that arise as cybersecurity becomes more complex. These skills are important for senior cybersecurity jobs such as vulnerability assessment analyst, threat intelligence analyst and security architect.
Having these advanced cybersecurity skills will take your career to the next level:
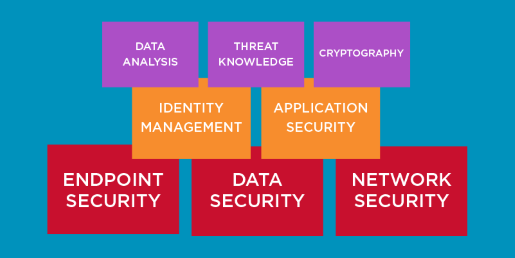
Data Analysis
Our recent cybersecurity report states that when it comes to data analysis, organizations are using more basic practices that have been in place for some time rather than more advanced practices that use massive data sets or machine-learning algorithms. This is where advanced cybersecurity pros come in and can recommend changes for their organizations to set new best practices company-wide.
Threat Knowledge
Threat intelligence is information that helps organizations prevent or diminish cyberattacks. After an organization gets attacked and is in the recovery process, they can share their solution and remediation plan to help other organizations avoid the same problems. Understanding the threat landscape, knowing where to find new information about cyberattacks and sharing that knowledge to help others inside and out of your organization is an advanced cybersecurity skill. Information Sharing and Analysis Organizations (ISAOs), like the CompTIA ISAO, and Information Sharing and Analysis Centers (ISACs) are member organizations that allow cybersecurity professionals to share information with a trusted group of peers in the industry.Cryptography
Cryptography is the science of securing communication using individualized codes so only the participating parties can read the messages. This skill is relevant for advanced IT pros because it helps keep high-stakes information more secure.
Build Your Cybersecurity Skills
To build your cybersecurity skills, we suggest following the CompTIA Cybersecurity Certification Pathway. The foundational skills mentioned most identify with CompTIA Security+, mid-range skills with CompTIA Cybersecurity Analyst (CySA+) and CompTIA PenTest+, and advanced skills with CompTIA Advanced Security Practitioner (CASP+).
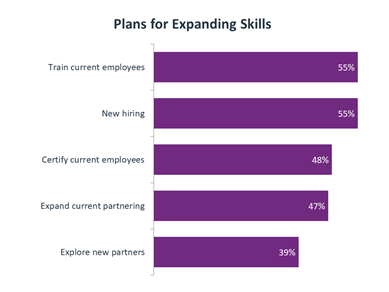
For IT pros wanting to achieve new knowledge and skills like those in CompTIA cybersecurity certifications, we have good news! Research shows that to expand their skill set, organizations are focusing cybersecurity efforts internally by training employees, bringing new specialists on board and certifying the current workforce.
Do you want to build your cyber skills? Download the exam objectives for the CompTIA cybersecurity certification that’s right for you and plot your pathway to cybersecurity success.

