In brief: Microsoft says Russia is the source for a majority of the nation-state cyberattacks observed in the past year, followed by North Korea, Iran, and China. In its latest Digital Defense Report, the company highlights trends in cybercriminal activity, which is growing in scale and sophistication with each passing month.
Cyberattacks are on the rise, and Microsoft says Russian state-sponsored hackers are responsible for more campaigns that all other nations combined.
The company's Digital Defense Report this year draws from a large data pool and brings into focus a number of trends in cybercrime, supply chain security, hybrid work, disinformation, and nation-state malicious activity such as data breaches and ransomware attacks.
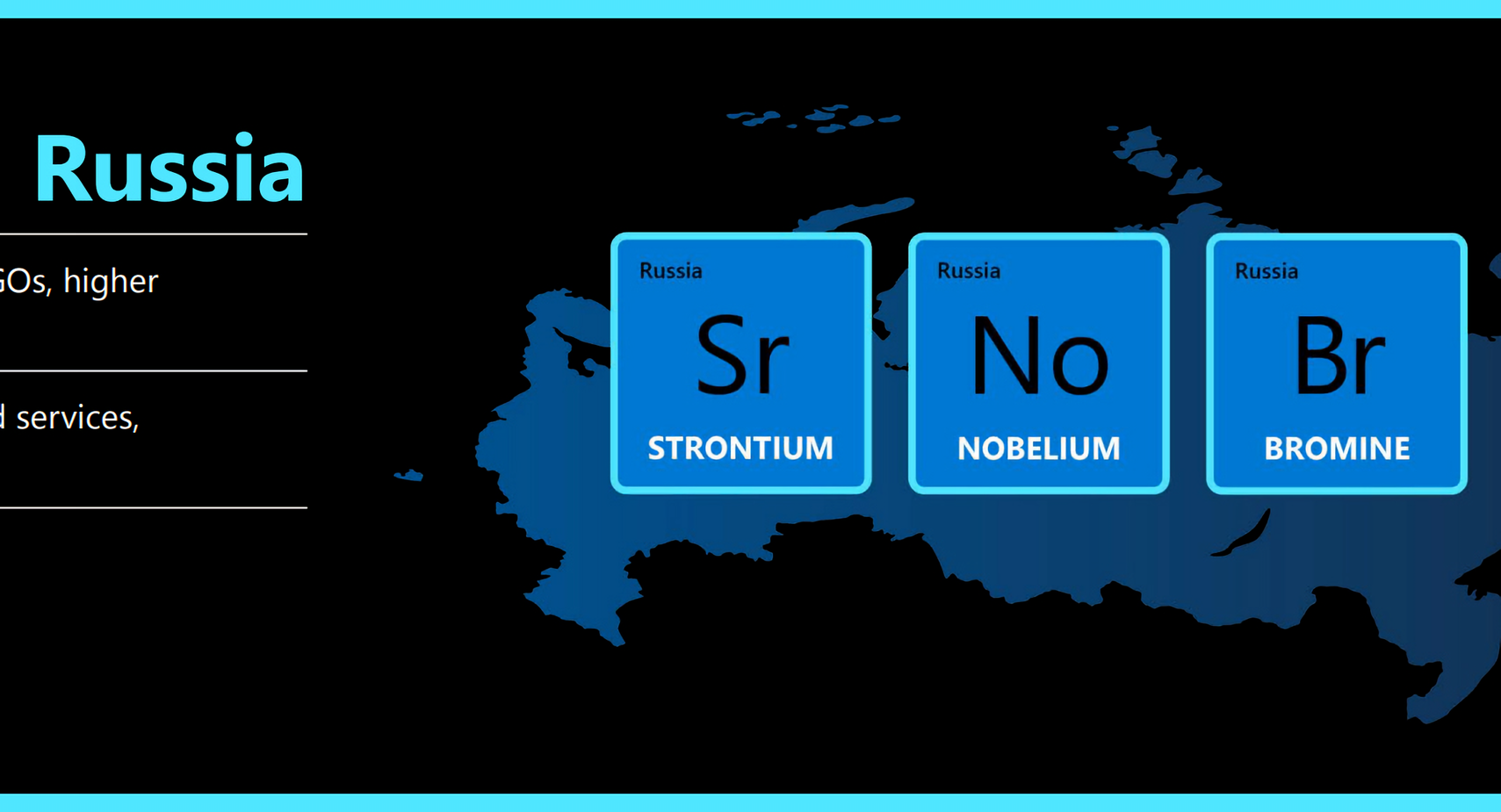
In the report, Microsoft corporate vice president of customer security and trust Tom Burt says no less than 58 percent of all cyberattacks observed by the company between July 2020 and June 2021 came from Russia alone. Not only that, but attacks coming from this region are increasingly effective – almost one in three are successful at compromising the security of the target organizations or population group.
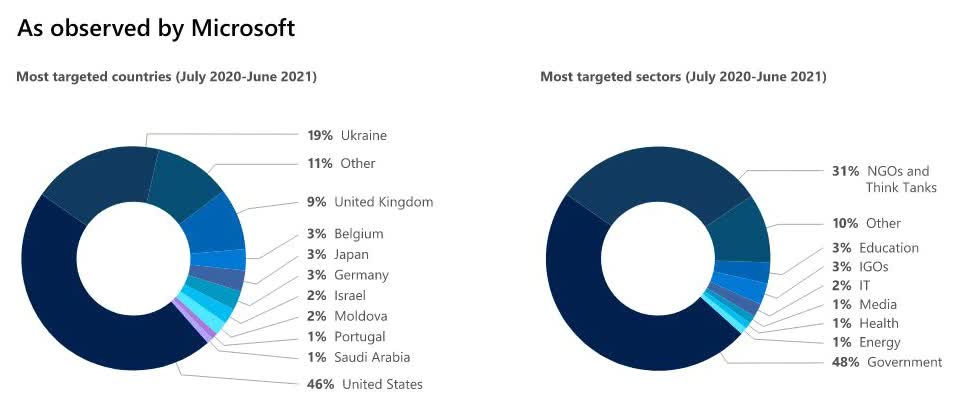
More than half of the attacks performed by Russian nation-state actors seem to be directed at government agencies and medical institutions for intelligence gathering in the areas of foreign policy and national security. The most targeted countries were the US, the UK, and Ukraine.
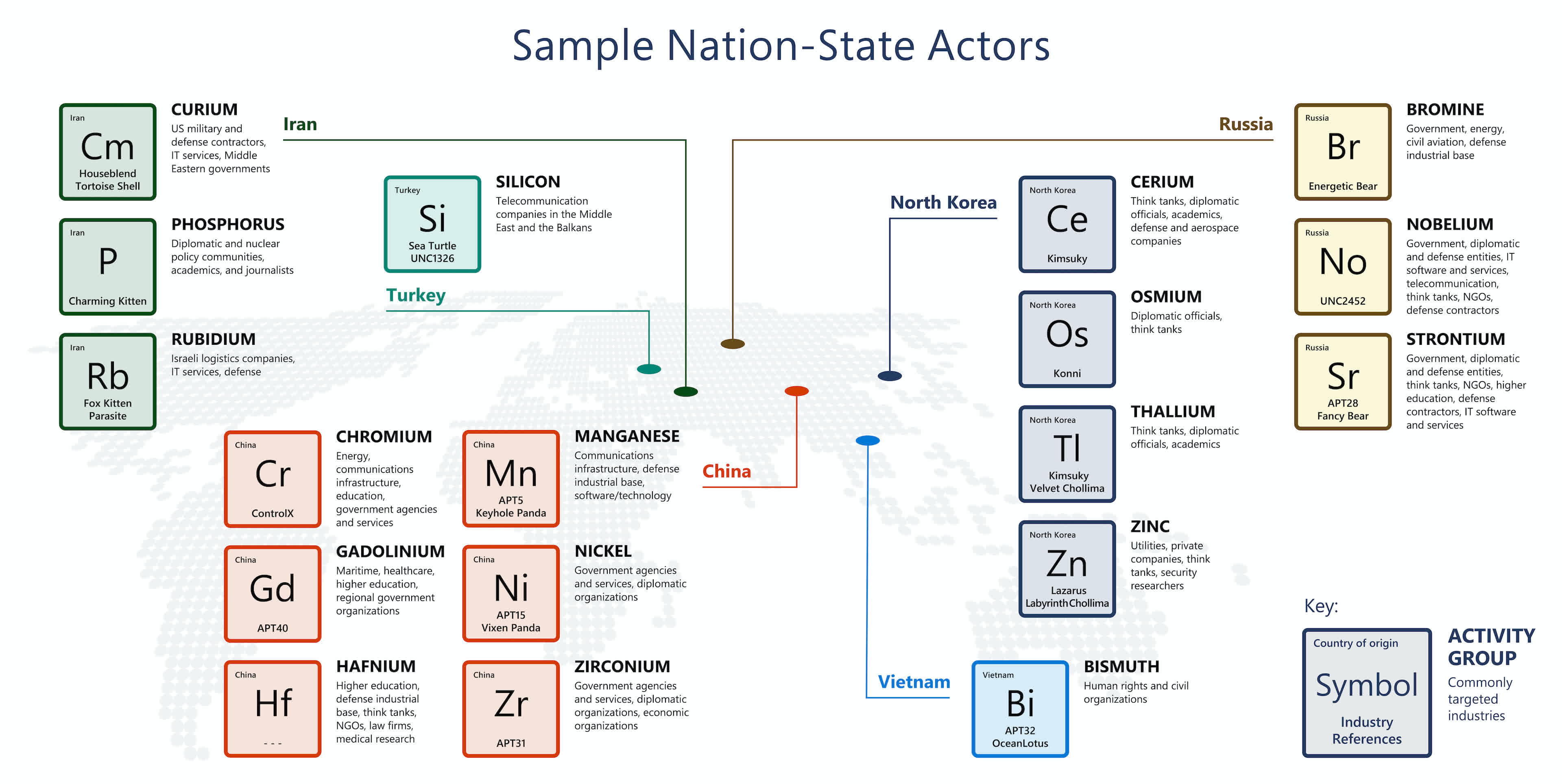
Almost all of the remaining volume of nation-state activity was observed as coming from China, Iran, and North Korea. China is widely blamed for the SolarWinds and Exchange Server attacks, but it also has some of the most talented white hat hackers in the world. Some Chinese actors such as CHROMIUM have been observed targeting neighboring countries for insights into their investments, negotiations, and economic resilience plans. Others like NICKEL have done the same with government agencies in Europe as well as Central and South America.
Iranian hacker groups worked with Russian hackers to undermine the US presidential elections last year. Microsoft's report notes that more recently, Iran has greatly intensified its cyberattacks on Israel amid heightened tensions between the two countries.

North Korea has a long history of attacking cryptocurrency exchanges and mining operations to extract funds for its weapons program. However, as the pandemic hit the country's already fragile economy, North Korean hackers from the notorious LAZARUS group turned to skimming card details from online shoppers and social engineering campaigns that target security researchers.
Overall, almost 80 percent of nation-state activity targeted enterprise and government organizations. Over the past three years, Microsoft has alerted its customers no less than 20,500 times about attempts from malicious actors to breach their systems. The Redmond company is only one of many companies in the broader security community, so its visibility is limited to a portion of all cyberattacks.
Also read: Scared of ransomware attacks? Here's how to protect yourself using Windows 10's built-in 'Ransomware protection' feature
Ransomware attacks have also been getting worse, as the operators of these campaigns have gotten bolder over the past year. Some of you may recall the Colonial Pipeline attack from earlier this year, which has triggered a strong governmental response. However, Microsoft notes the top five sectors targeted by ransomware campaigns are consumer retail (13 percent), financial services (12 percent), government (11 percent), manufacturing (12 percent) and health care (nine percent).
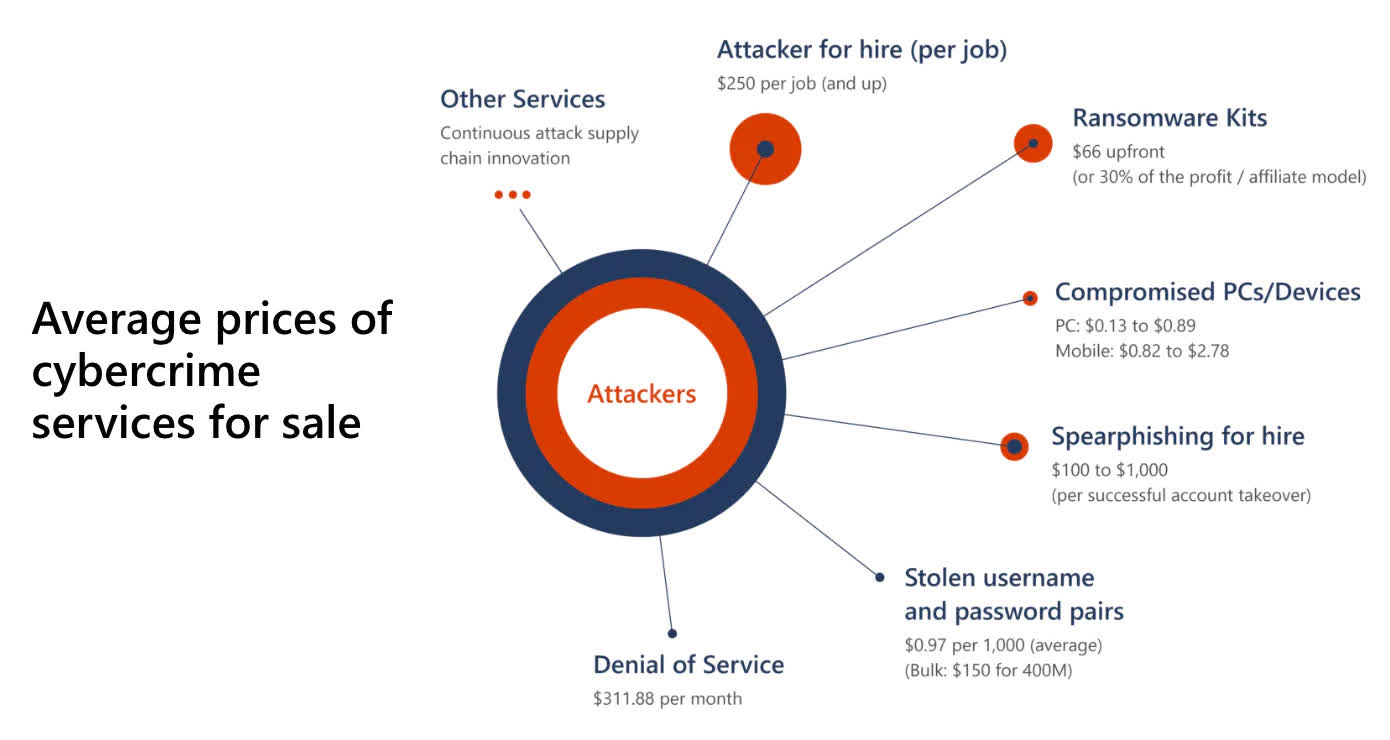
It also doesn't help that the "cybercrime-as-a-service" economy has rapidly evolved into a sprawling online marketplace where anyone – even the less technically inclined among us – can purchase ransomware kits for as little as $66. Then you have suppliers of compromised user credentials for a variety of services or organizations selling for anywhere between $1 and $50 per set, and sometimes much more depending on the perceived value of the victim.
This is all facilitated by a diverse ecosystem of cryptocurrency escrow services that act as brokers between buyers and sellers. That has led the US Justice Department to form a new cryptocurrency enforcement team that will deal with criminals who misuse digital tokens, which Microsoft says is a step in the right direction.
Another positive trend is that governments and companies are establishing a closer relationship when it comes to reporting and dealing with cybersecurity incidents. Some countries are introducing and passing new laws that treat these incidents as a threat on national security. A notable example is that of the Netherlands, who will use intelligence as well as armed forces to respond to ransomware attacks – a decision that will likely be mirrored by other countries in the coming years.
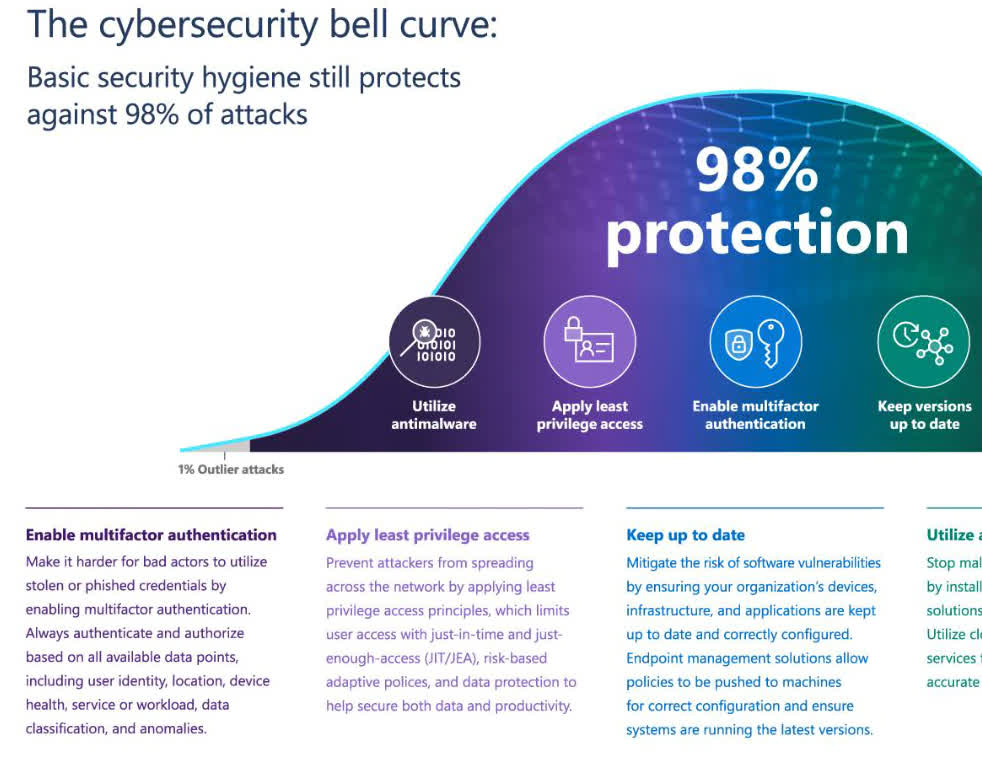
Finally, Microsoft weighed in on the challenges of developing better security for an increasingly hybrid workforce. Many businesses are currently navigating the relatively unexplored waters of hybrid and remote work after being forced to move in this direction by the coronavirus pandemic. This created a wider attack surface for cybercriminals, but the risks can be mitigated by practicing fundamental cybersecurity hygiene.
One of the recommended steps is to have everyone in your organization use multi-factor authentication, which is one of the cheapest layers of security you can add. Microsoft says this alone can prevent 98 percent of the attacks we see today, as someone who stole or bought credentials can't effectively use them to breach your network.
The good news is that Microsoft has seen a 220 percent increase in multi-factor authentication usage across partner and client companies. The company does, however, note that we have a long way to go before organizations reach full adoption of stronger authentication methods.