Let’s learn about Intune Win32 App Deployment Detection Methods. Application deployment has rules, such as detection methods, and requirements. These rules specify when and how the client installs the software.
Detection methods allow the administrator to check software installs to ensure that the application is not already installed. Detection rules are used in SCCM application model deployments, and Intune win32 uses similar detection rules.
Here you can see the process for Intune Win32 App Deployment. Check the more details added by Vimal in the post Intune Win32 App Issues Troubleshooting Client-Side Process Flow.
- Once the app “Detection rule” evaluation is completed, the next step is “Check Applicability.” Checks were performed against the rules we configured before.
- After “Check applicability” completes, the next stage is to process Content Download.
To make things easier, some of the easy ways in which we can set a registry key as a detection method, Easy Way to Set Detection Method for Intune Win32 App.
- Intune Application Deployment using MSI EXE IntuneWin Formats
- Intune Win32 App Deployment Toast Notification | User Experience
- Intune Company Portal Branding Customization Options
Intune Win32 App Deployment Detection Methods
Let’s have a look at detection rules available in Intune.
- Sign in to the Microsoft Endpoint Manager admin center https://endpoint.microsoft.com
- Select Apps > Windows > Windows apps. Select the existing Win32 application from the list.
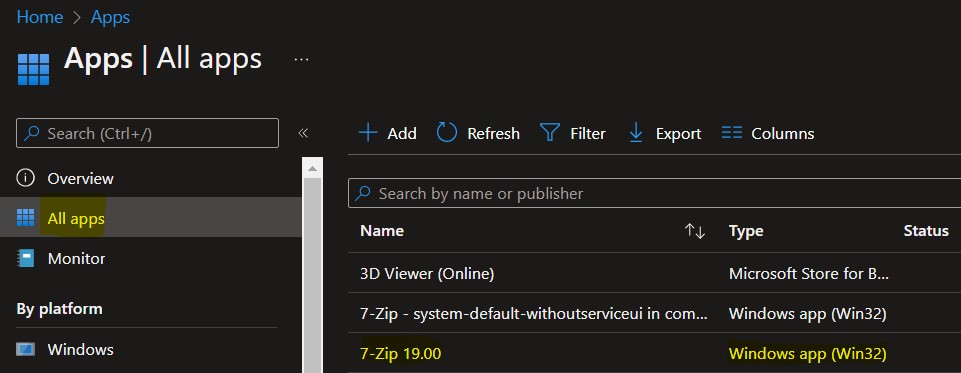
Select the application and select Properties. Scroll down and click on Edit in the Detection rules.
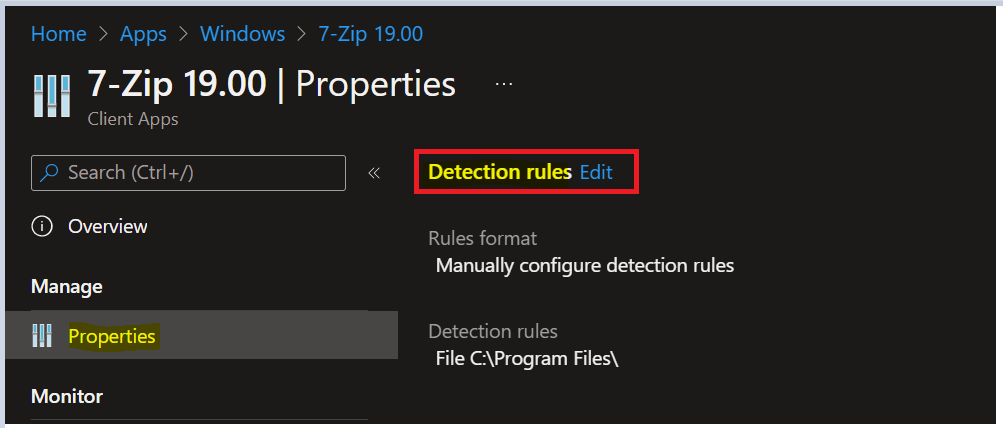
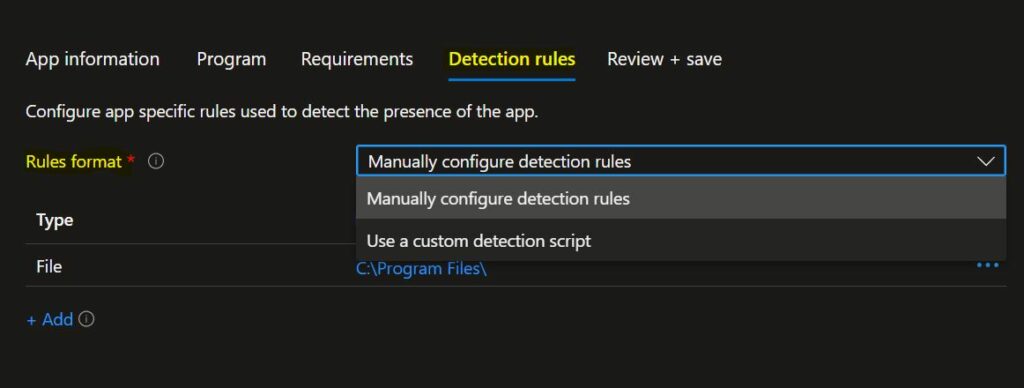
On the Detection rules blade, You can choose to either manually configure the detection rules or use a custom script to detect the presence of the app. The following Win32 apps detection rule formats appear –
Manually Configure Detection Rules – This detection rule format allows the administrator to specify a detection rule based on MSI product code, file or folder existence, file version, registry key, or value.
Use a custom detection script – This detection rule format allows the administrator to use a custom script for detecting the app.
Note – You must choose at least one detection rule. You can choose to add multiple rules.
Manually Configure Detection Rules
Here I selected the Manually configure detection rules format. Click on Add button, and A popup will appear showing the Detection rule. This detection rule format provides three detection rules MSI, File, and Registry.
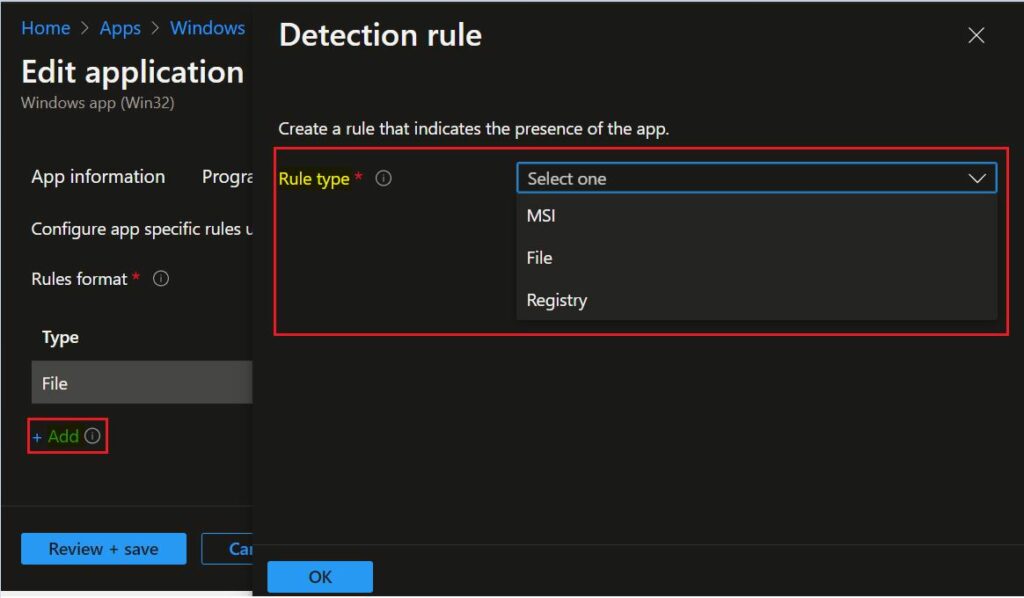
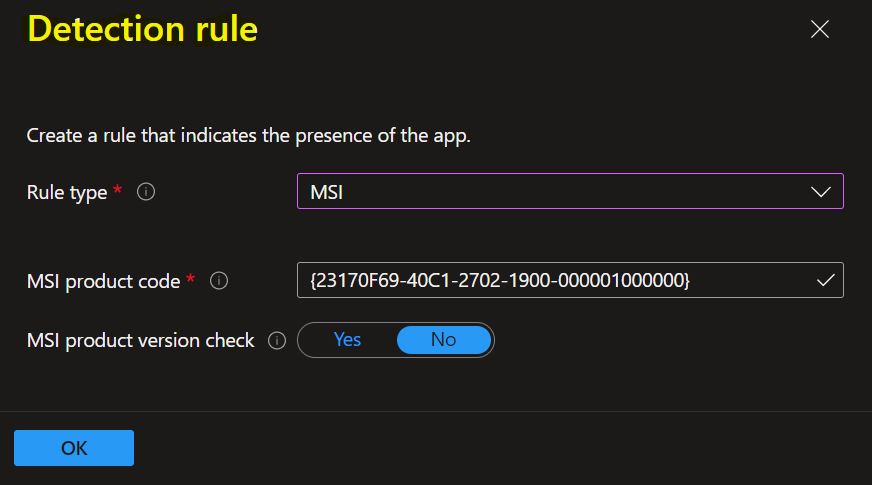
The next is Selected Rule type MSI. Let’s see the available option to detect app –
MSI: Verify based on an MSI version check. This option can be added only once. When you choose this rule type, you have two settings:
MSI product code: Add a valid MSI product code for the app. (The app’s GUID is based on the applications). For example – For 7zip Version 19, It’s {23170F69-40C1-2702-1900-000001000000}
MSI product version check: Select Yes to verify the MSI product version in addition to the MSI product code.
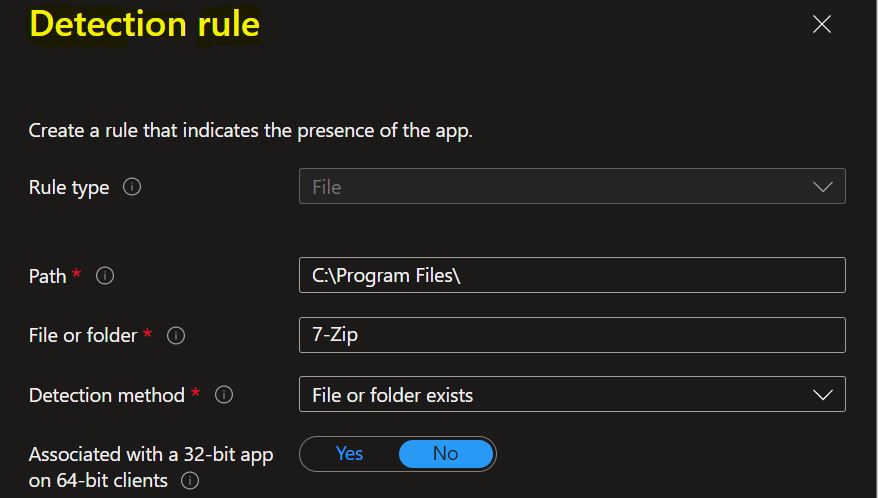
The next, Selected Rule type File: Verify based on file or folder detection, date, version, or size.
- Path: Enter the full path of the folder that contains the file or folder to detect.
- File or folder: Enter the file or folder to detect.
- Detection method: Select the type of detection method used to validate the presence of the app. The following detection methods are available in file based detection rules.
- File or folder exists.
- Date modified
- Date created
- String (version)
- Size in MB
- Associated with a 32-bit app on 64-bit clients: Select Yes to expand any path environment variables in the 32-bit context on 64-bit clients. Select No (default) to expand any path variables in the 64-bit context on 64-bit clients. 32-bit clients will always use the 32-bit context.
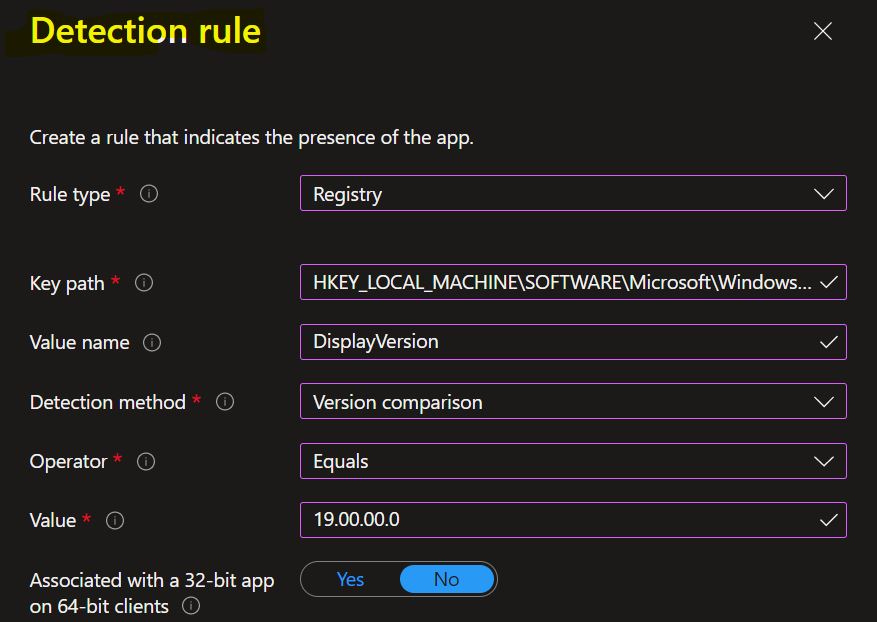
In the next, Selected Rule type Registry: Verify based on value, string, integer, or version.
- Key path: The full path of the registry entry that contains the value to detect. A valid syntax is HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\O365ProPlusRetail or HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\O365ProPlusRetail.
- Value name: The name of the registry value to detect. If this value is empty, the detection will happen on the key. The (default) value of a key will be used as a detection value if the detection method is other than file or folder existence.
- Detection method: Select the type of detection method that’s used to validate the presence of the app. The following detection methods are available in registry based detection rules.
- Key exists
- Key does not exist
- String comparison
- Version comparison
- Integer comparison
- Associated with a 32-bit app on 64-bit clients: Select Yes to search the 32-bit registry on 64-bit clients. Select No (default) to search the 64-bit registry on 64-bit clients. 32-bit clients will always search the 32-bit registry.
Here you can check the registry path for the applications. Most apps are installed in the same location depending on the app architecture – Detection Method for Intune Win32 App. For Example, Here, Check for registry value string equals.
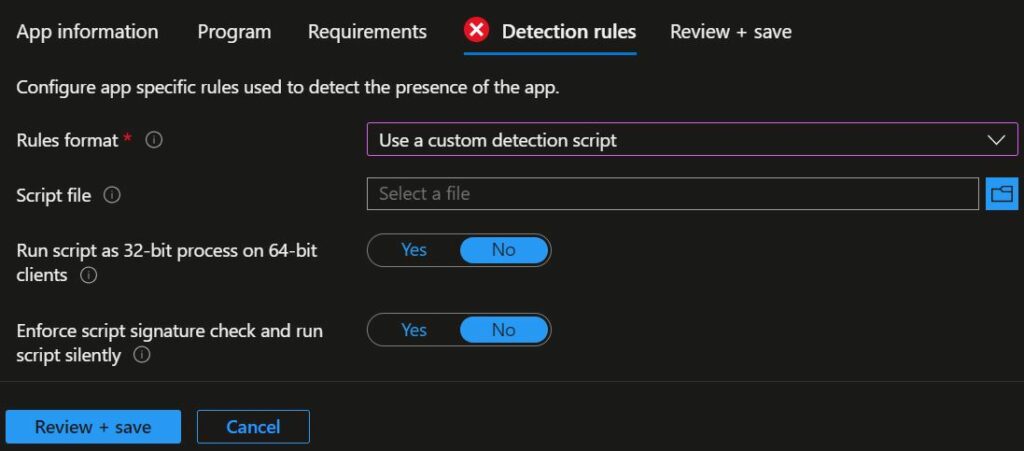
Use a Custom Detection Script
On the Detection rules pane, configure the rules format to Use a custom detection script. You can specify the PowerShell script that will be used to detect this app.
- Script file: Select a PowerShell script that will detect the presence of the app on the client. The app will be detected when the script both returns a 0 value exit code and writes a string value to STDOUT.
- Run script as 32-bit process on 64-bit clients: Select Yes to run the script in a 32-bit process on 64-bit clients. Select No (default) to run the script in a 64-bit process on 64-bit clients. 32-bit clients run the script in a 32-bit process.
- Enforce script signature check: Select Yes to verify that a trusted publisher has signed the script, which will allow the script to run with no warnings or prompts displayed. The script will run unblocked. Select No (default) to run the script with user confirmation without signature verification.