It's a race to the bottom for hackers and cybercriminals who are looking to make money from the coronavirus (COVID-19) or trying to disrupt information that can keep people informed.
Sometimes, they are doing both at once.
The coronavirus app that is ransomware
Android users are coming across a website that offers you the power of coronavirus tracking in your pocket.
Download the app and get alerts when someone near you is diagnosed with the virus. Even someone on "your street."
You can imagine how tempting this tool would be for many people as a means of protecting themselves.
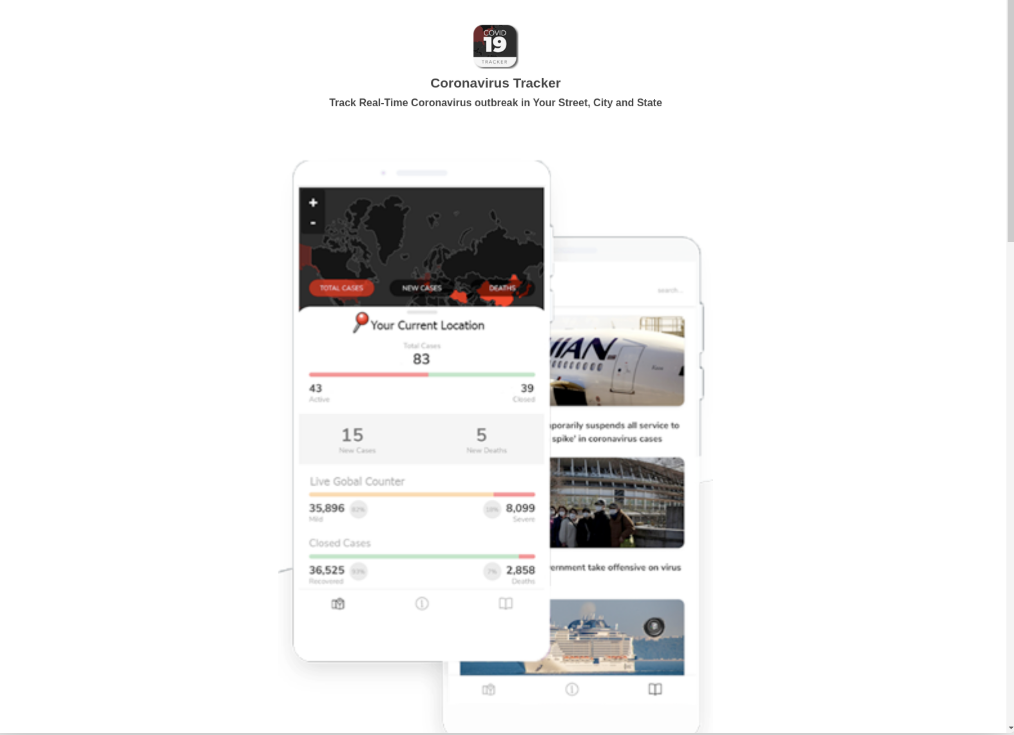
Researchers at Domaintools came across the website and tested the app.
"The domain prompts users to download an Android App that will give them access to a Coronavirus map tracker that appears to provide tracking and statistical information about COVID-19, including heatmap visuals."
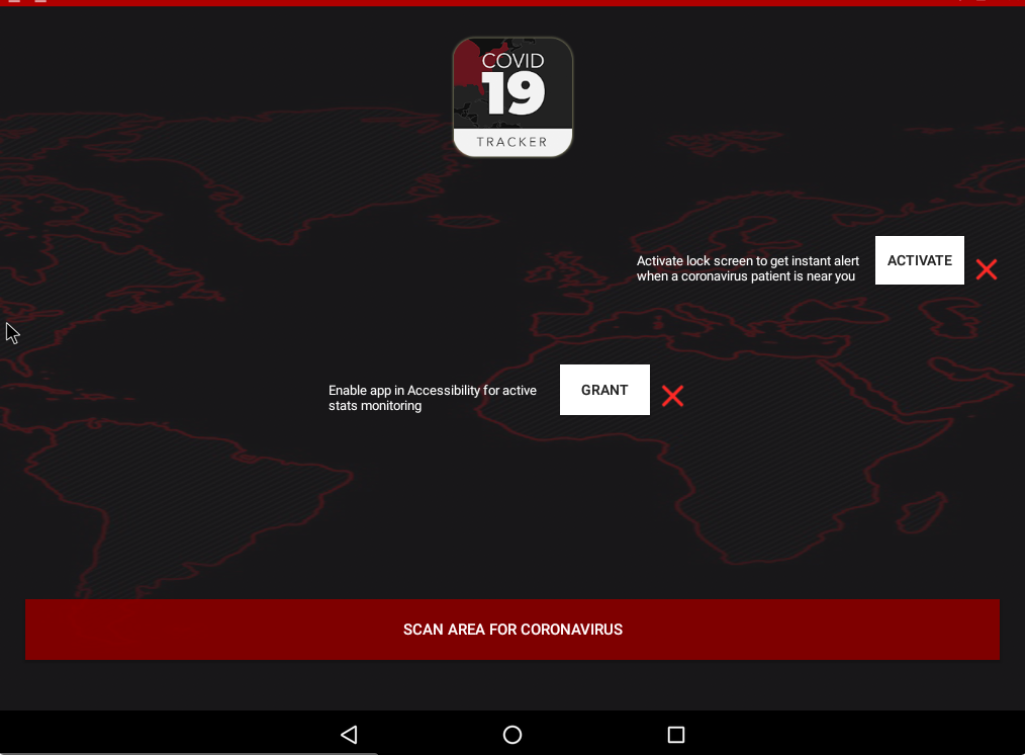
You can see the app asking you for various permissions.
And once you give it those, you quickly find out this app is not about helping you stay safe, it's about cybercriminals profiting from you and coronavirus fears.
A ransom note pops up on the screen:
"YOUR PHONE IS ENCRYPTED: YOU HAVE 48 HOURS TO PAY 100$ in BITCOIN OR EVERYTHING WILL BE ERASED."
Can you imagine?
You've lost any sense of normalcy to the coronavirus, and in an effort to stay informed you could now lose your contacts, your photos, and whatever else you have on your device.
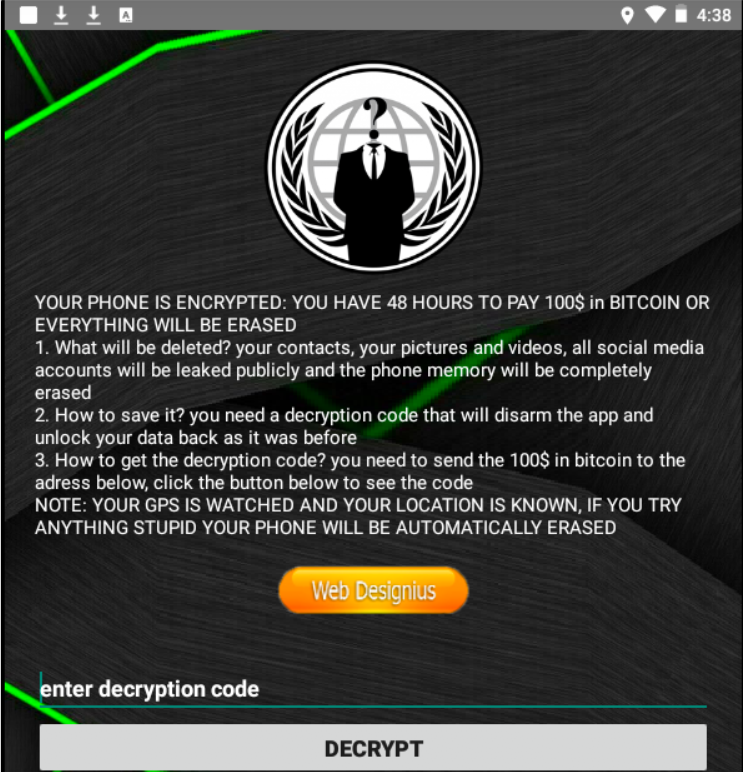
Domaintools researchers uncovered this about the app:
"This Android ransomware application, previously unseen in the wild, has been titled 'CovidLock' because of the malware's capabilities and its background story. CovidLock uses techniques to deny the victim access to their phone by forcing a change in the password used to unlock the phone. This is also known as a screen-lock attack and has been seen before on Android ransomware."
The Android Nougat OS does offer some protection against attacks like CovidLock, but users must enable the password unlock feature in Nougat for the protection to work.
No, this app is not available from the Google Play store. It's another reason to remind end-users to never download an app from anything but the official store for the OS.
Hackers selling COVID-19 map infected with malware, ransomware
Here is another example of how hackers and cybercriminals are going to new lows to make a capitalize off the coronavirus pandemic.
Johns Hopkins University is both respected and trusted, so it is no surprise that the interactive coronavirus (COVID-19) map the university developed is being used by people around the world to track outbreaks.
![]()
Unfortunately, hackers are trying to profit on this credibility, and cybersecurity journalist Brian Krebs explains how they are doing it:
Late last month, a member of several Russian language cybercrime forums began selling a digital Coronavirus infection kit that uses the Hopkins interactive map as part of a Java-based malware deployment scheme. The kit costs $200 if the buyer already has a Java code signing certificate, and $700 if the buyer wishes to just use the seller's certificate.
"It loads [a] fully working online map of Corona Virus infected areas and other data," the seller explains. "Map is resizable, interactive, and has real time data from World Health Organization and other sources. Users will think that PreLoader is actually a map, so they will open it and will spread it to their friends and it goes viral!"
In other words, hackers are poisoning the very map that is trying to keep us healthy. How low can hackers go?
Be sure to advise your end-users to only view the map from this legitimate link: Johns Hopkins University and Medicine COVID-19 Map.
Phishing attack targeting hospital staff with "corona virus awareness"
If there's a hot topic in the world, you can count on hackers to try and exploit it through phishing attacks.
But this may be one of the sleaziest examples we've seen. It's a phishing attack on medical professionals in the midst of the coronavirus pandemic. You must click the link to join a "mandatory" seminar on the coronvirus:
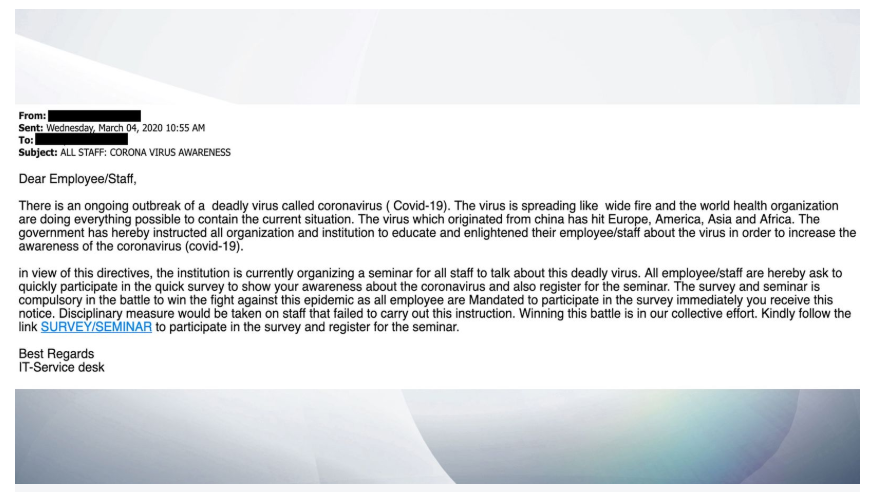
And the point, says Sky News, is to try and phish or capture the username and password of those working in hospitals. Read our full story on how the healthcare phishing attack works.
And while we're talking about phishing attacks, you should know about this one: some hackers are combining the "sex-stortion scam" email (where they claim to have screen shots of you) with the coronavirus.
"Now, the price is $4000, and if you don’t pay…
…then they’re threatening to infect your family with coronavirus," says Sophos.
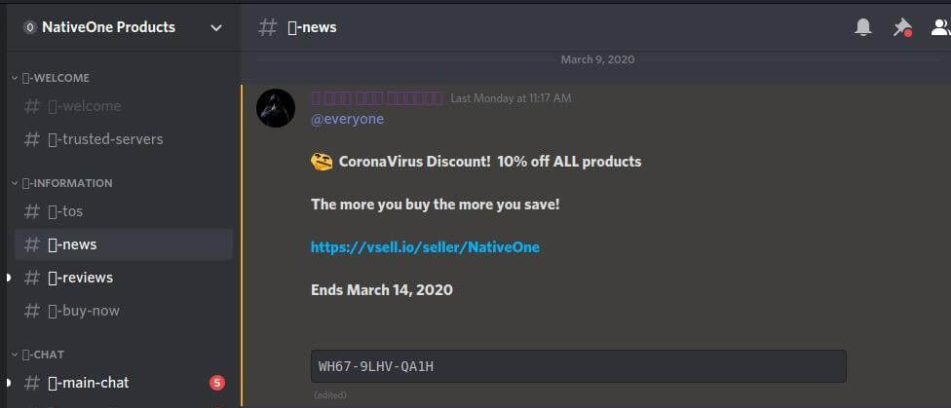
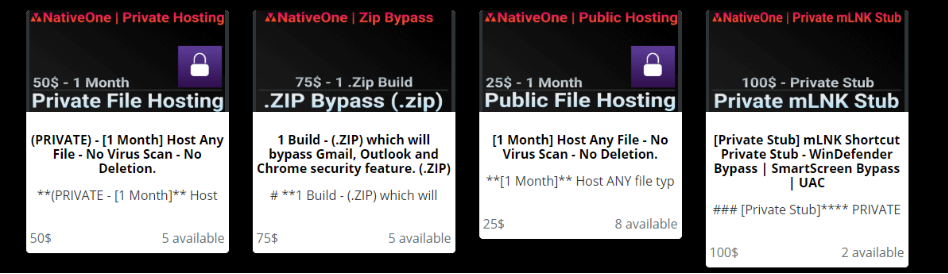
COVID-19 hacking services on sale
Meanwhile...on the dark web: it's not exactly a black Friday sale but Check Point researchers found hacking forums celebrating the coronavirus pandemic with discounts.
This includes 10-15% off various hacking services and tools you can use to compromise corporate networks.
Phone scammers making money off coronavirus fears
And the chance for criminals to make money goes beyond the cyber realm. They might reach out and call you.
In the Bay Area, Daly City Police tweeted about a maddening phone scam that appears to involve identity theft and ripping off your bank account at the same time:
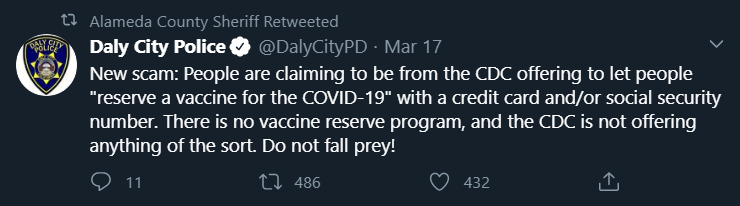
"People are claiming to be from the CDC offering to let people "reserve a vaccine for COVID-19" with a credit card and/or social security number."
We're guessing some of the tech support and virus removal call centers have found a new market.
Cyberattack on Health and Human Services website
On Sunday, March 15, the U.S. Health and Human Services (HHS) website was hit by what may have been a DDoS cyberattack when its servers were flooded with incoming traffic in hopes of knocking things offline.
According to Bloomberg, that effort failed.
However, it may be linked to or timed with some sort of disinformation campaign that required the U.S. National Security Council to tweet out what was true and what was not:
The coronavirus and cyberattacks: 'seen as an opportunity'
We'll keep adding to this list as we come across ways hackers and cybercriminals are stooping to new lows in the face of an unprecedented situation.
It's a situation that Thomas Hatch, CTO and Co-Founder at SaltStack, recently summed up in a way that makes sense:
"In 1776, George Washington launched a surprise attack on a group of Hessian mercenaries on Christmas night. It helped turn the tide of the revolutionary war for the US, because the attack happened while the enemy was weak and distracted.
As we hunker down and try to fight Coronavirus, we should expect cyberattacks to continue, and to be seen as more and more opportunistic. Those who wish to launch cyberattacks will not show mercy because of the situations that we are in, but rather this will be seen as an opportunity."
Thankfully, this fight is not one-sided.
There is also a brand new opportunity for cybersecurity leaders and their teams to continue learning and growing right now.
It's the reason we've developed the SecureWorld Remote Sessions for the cybersecurity community to stay connected and sharing critical information during these challenging times.




