How to make AI more ethical
Venture Beast
AUGUST 29, 2021
My team came up with these 5 ethical AI principles while developing our own framework. Your team may find them helpful. Read More.

Venture Beast
AUGUST 29, 2021
My team came up with these 5 ethical AI principles while developing our own framework. Your team may find them helpful. Read More.

Forrester IT
SEPTEMBER 3, 2021
In my past 30 years in the contact center industry at organizations like RingCentral, Genesys, 8×8, and IBM, I’ve watched the same movie over and over and over again…too many contact centers are laboring under the tyranny of being a cost center with schizophrenic goals of making customers happy while “doing more with less”. This […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
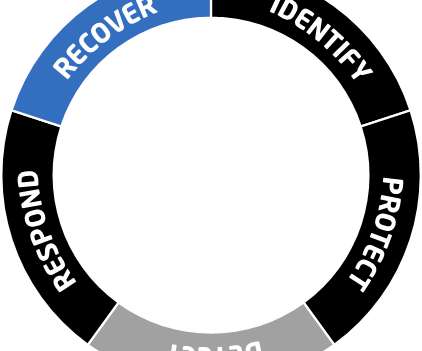
Association of Information Technology Professional
AUGUST 30, 2021
Dig into the five functions of the NIST Cybersecurity Framework and learn the types of tools IT pros can use to defend their organizations.

Anoop
SEPTEMBER 1, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Easiest Method to Create SCCM WQL Queries for Collection appeared first on HTMD Blog #1 by Anoop C Nair.

Advertiser: GEP
The technological landscape is dynamic and changes quickly. And for procurement and supply chain leaders looking to harness the power of technology to navigate complex challenges and an uncertain business environment, keeping up with the latest trends can be its own obstacle. So, what’s on the technological horizon for procurement and supply chain for the year ahead?

Tech Republic Security
SEPTEMBER 3, 2021
Cybersecurity training is not the same across all companies; SMB training programs must be tailored according to size and security awareness. Here are an expert's cybersecurity training tips.

Forrester IT
SEPTEMBER 2, 2021
Will all of the digital urgency brought about by the pandemic disappear? Learn how AI can help drive creativity and innovation in your organization.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.
Anoop
AUGUST 30, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Translate SCCM Error Codes to Error Messages appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Security
AUGUST 31, 2021
Authentication sans password is already possible and solutions are on the market from companies like Ping Identity. With passwords passé, it's time to make the leap to better security.

Forrester IT
SEPTEMBER 2, 2021
Out of the 14 different spheres of influence that we track at Forrester, the channel industry trade press ranks near the top. Smart vendors and distributors know that the magic of finding, influencing, recruiting, enabling, and nourishing a top performing channel boils down to three simple questions about partners: What do they read? Where do […].

Tech Republic Cloud
AUGUST 30, 2021
If you frequently lose your tabs, Jack Wallen wants to remind you about pinned tabs and one behavior that can totally frustrate you with that feature.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Anoop
SEPTEMBER 1, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Learn How to Resize Cloud PC Windows 365 appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Security
SEPTEMBER 3, 2021
Fail2ban should be on every one of your Linux servers. If you've yet to install it on either Rocky Linux or AlmaLinux, Jack Wallen is here to help you out with that.

Forrester IT
SEPTEMBER 2, 2021
Static annual plans often collect dust on a shelf. Leaning into the planning process can help you build a more dynamic and effective marketing plan that drives forward the objectives of the business.

Information Week
SEPTEMBER 2, 2021
Crunching sports data and making it presentable to tennis fans continues even with the return of live audience in the stands.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.

Anoop
AUGUST 29, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post FIX: SCCM Task Sequence Failed to Run Command Line Error 0x8007010B appeared first on HTMD Blog #1 by Jitesh Kumar.

Tech Republic Security
AUGUST 31, 2021
Soft skills are just as important, if not more so, than technical skills in cybersecurity professionals. People with soft skills can be trained in tech skills, expert says.

Forrester IT
AUGUST 30, 2021
Many B2B marketers find joy in campaign planning — but not so much in budgeting. It turns out the two are intimately connected.

Information Week
AUGUST 30, 2021
Bringing a major real estate services company with multiple brands in its portfolio to the cloud required a multifaceted strategy that continues to evolve.

Advertisement
Outdated or absent analytics won’t cut it in today’s data-driven applications – not for your end users, your development team, or your business. That’s what drove the five companies in this e-book to change their approach to analytics. Download this e-book to learn about the unique problems each company faced and how they achieved huge returns beyond expectation by embedding analytics into applications.

Anoop
AUGUST 30, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Easily Add Apply Driver Package Step to SCCM Task Sequence appeared first on HTMD Blog #1 by Jitesh Kumar.

Tech Republic Security
SEPTEMBER 2, 2021
The Labor Day holiday could be prime time for more than just barbecues and closing the pool for the year as the open season on ransomware continues.

Tech Republic Cloud
SEPTEMBER 1, 2021
If you're a Google Docs power user who works with a Chromebook, this is one handy tip you'll want to implement.

Information Week
AUGUST 31, 2021
AI has moved from an experiment to mainstream production during the pandemic. Here are some of the high-value use cases enterprises should be deploying.

Advertisement
Project managers are now spending more time managing strategic projects where the scope is susceptible to changes as the projects progress. Scope change control is now becoming a critical component of project management requiring project teams to become more active in solving problems and making decisions. Scope change control will require collaboration with stakeholders and possibly government agencies.

Anoop
SEPTEMBER 2, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post How to Reprovision Cloud PC Windows 365 appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Security
AUGUST 30, 2021
Microsoft 365's "secure by default" stance removes some tools used by security teams. Here's how to work around the new restrictions.

TechSpot
SEPTEMBER 3, 2021
A court in Alexandria, Virginia, ruled that inventions can only be patented under the name of a "natural person." The decision was made against someone who tried to list two designs under the name of an AI as part of a broader project to gain worldwide recognition of AI-powered inventions.

Information Week
SEPTEMBER 2, 2021
Artificial intelligence is seeping into enterprises in various ways. Smart enterprises integrate AI into their business strategy.

Advertiser: GEP
Direct materials sourcing is evolving, with procurement now tasked not only with cost efficiency but managing sustainability and risk management. The environment is marked by heightened demand and expectations, compounded by challenges such as rising input prices, supply chain disruptions and geopolitical tensions. While some embrace cutting-edge tools like AI and blockchain for global trade functions, others lag in technology adoption.

Anoop
AUGUST 31, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post KB10503003 Hotfix Released for SCCM 2107 Early Ring appeared first on HTMD Blog #1 by Anoop C Nair.

Gizmodo
SEPTEMBER 3, 2021
After users threatened to boycott the internet domain service GoDaddy for hosting the newly-established tip line that allows Texans to anonymously snitch on private citizens they suspect of performing an abortion after six weeks or anyone who “aids or abets” such abortions in the state, the company abruptly announced… Read more.

The Verge
SEPTEMBER 3, 2021
Photo by PATRICK T. FALLON/AFP via Getty Images. In case you haven’t heard, Texas now has a law that makes it illegal for anyone to help women get an abortion after six weeks of pregnancy — and to take advantage of that, the anti-abortion group Texas Right to Life is encouraging citizens to report those people at a dedicated “whistleblower” website, promising to “ensure that these lawbreakers are held accountable for their actions.”.

TechSpot
SEPTEMBER 1, 2021
The Surveillance Legislation Amendment (Identify and Disrupt) Bill 2020 gives the Australian Federal Police (AFP) and the Australian Criminal Intelligence Commission (ACIC) powers to modify, add to, copy, or delete data to "frustrate the commission of serious offenses online." To gather evidence of suspected criminal activity, they also have the.

Speaker: Shreya Rajpal, Co-Founder and CEO at Guardrails AI & Travis Addair, Co-Founder and CTO at Predibase
Large Language Models (LLMs) such as ChatGPT offer unprecedented potential for complex enterprise applications. However, productionizing LLMs comes with a unique set of challenges such as model brittleness, total cost of ownership, data governance and privacy, and the need for consistent, accurate outputs. Putting the right LLMOps process in place today will pay dividends tomorrow, enabling you to leverage the part of AI that constitutes your IP – your data – to build a defensible AI strategy fo
Let's personalize your content