Configure PUA Protection in Microsoft Edge using Intune MEM | Microsoft Defender. Let’s check how you can configure Microsoft Defender Potentially Unwanted Applications PUA Protection in Microsoft Edge using Intune, aka Endpoint Manager.
Potentially unwanted applications aren’t considered viruses or malware, but these apps might perform actions on endpoints that adversely affect endpoint performance or use. PUA can also refer to applications that are deemed to have poor reputations.
PUA protection aims to safeguard user productivity and ensure enjoyable Windows experiences. This protection helps deliver more productive, performant, and delightful Windows experiences.
PUAs are not considered malware. Microsoft uses specific categories and definitions to classify software as potentially unwanted applications (PUA).
There are many other policies available to configure Microsoft Defender SmartScreen to block potentially unwanted apps, as mentioned below.
- Configure Microsoft Defender SmartScreen
- Configure Microsoft Defender SmartScreen to block potentially unwanted apps
- Force Microsoft Defender SmartScreen checks on downloads from trusted sources
- Prevent bypassing of Microsoft Defender SmartScreen warnings about downloads
You can perform the basic Microsoft Edge security policy troubleshooting from the MEM admin center portal. One example is given below How To Start Troubleshooting Intune Issues from the server-side. The next level of troubleshooting is with MDM Diagnostics Tool to collect the log and information from the client-side.
- Easily Manage Microsoft Edge Extensions using Intune
- Troubleshoot Microsoft Edge Security Policy Deployment issues with Intune
- Learn How to Enable Microsoft Edge Sleeping Tabs using Intune
Configure Microsoft Defender PUA using Group Policy
There are two ways to configure the PUA. Let’s check how to configure Microsoft Defender PUA using Group Policy. If you are doing it only for individual Windows 11/10 devices, you can do this using GPEDIT.MSC.
But if you want to implement it for many devices in the network and those devices are Domain Joined or Hybrid Azure AD joined, you can use the Group Policy Management option from the Domain controller.
- Launch Group Policy Management Console using any of the methods.
- Navigate to Computer Configuration > Administrative Templates > Windows Components > Microsoft Defender Antivirus.
- Select Configure Detection for potentially unwanted applications.
Enable or disable detection for potentially unwanted applications. You can choose to block, audit, or allow when potentially unwanted software is being downloaded or attempts to install itself on your computer.
Enabled:
Specify the mode in the Options section:
-Block: Potentially unwanted software will be blocked.
-Audit Mode: Potentially unwanted software will not be blocked, however if this feature would have blocked access if it were set to Block, then a record of the event will be in the event logs.
Disabled:
Potentially unwanted software will not be blocked.
Not configured:
Same as Disabled.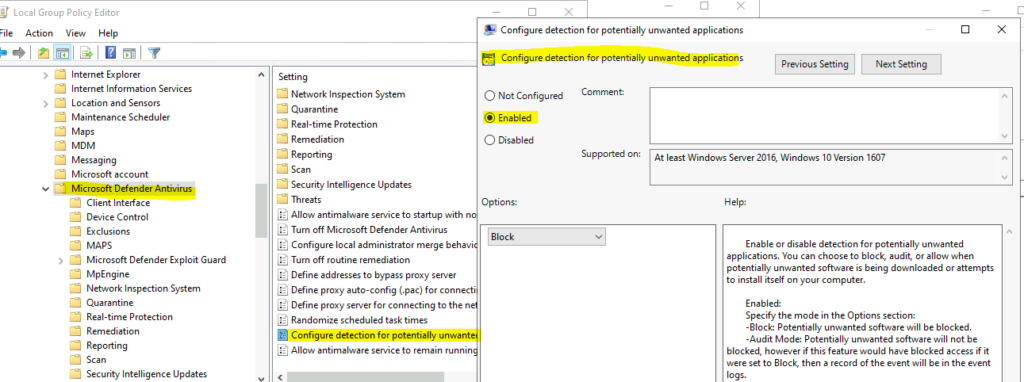
Configure Potentially Unwanted Applications PUA Protection in Microsoft Edge
This section will help you assign the policy set up protection by enabling the potentially unwanted apps to feature in Microsoft Edge using Intune setting catalog policies.
You can refer to the following guide to Create Intune Settings Catalog Policy and deploy it only to a set of Intune Managed Windows 11 or Windows 10 devices using Intune Filters.
Let’s follow the steps to configure PUA protection in Microsoft Edge using Intune –
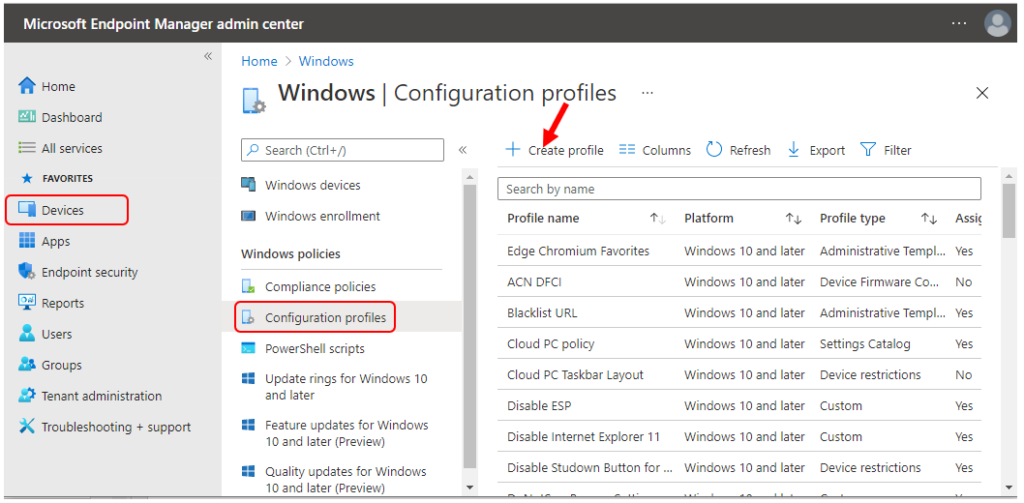
- Sign in to the Endpoint Manager Intune portal https://endpoint.microsoft.com/
- Select Devices > Windows > Configuration profiles > Create profile
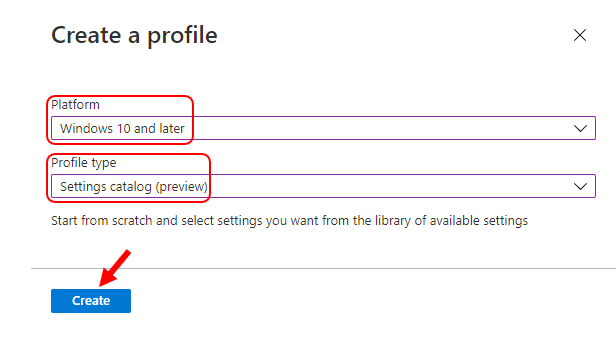
In Create Profile, Select Platform, Windows 10, and later and Profile, Select Profile Type as Settings catalog. Click on Create button.
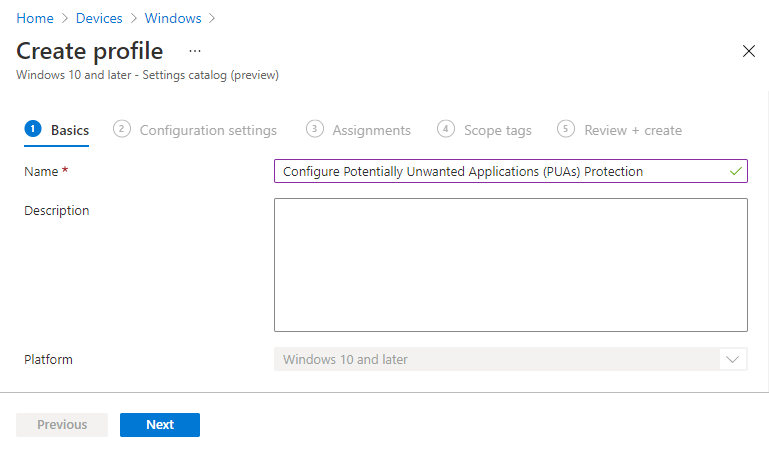
On the Basics tab, enter a descriptive name, such as Configure Potentially Unwanted Applications PUA Protection in Microsoft Edge. Optionally, enter a Description for the policy, then select Next.
In Configuration settings, click Add settings to browse or search the catalog for the settings you want to configure.
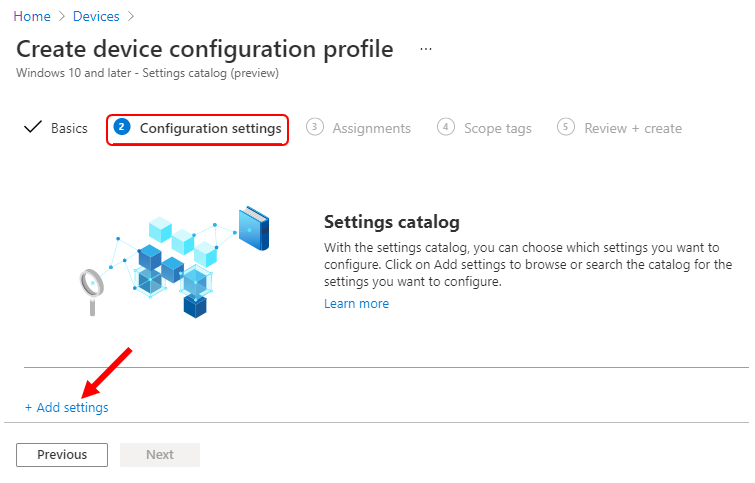
On the Settings Picker windows, Select Microsoft Edge, Under SmartScreen settings to see all the settings in this category.
Select Configure Microsoft Defender SmartScreen, Configure Microsoft Defender SmartScreen to block potentially unwanted apps, and Prevent bypassing Microsoft Defender SmartScreen warnings about downloads below.
After adding your settings, click the cross mark at the right-hand corner to close the settings picker.
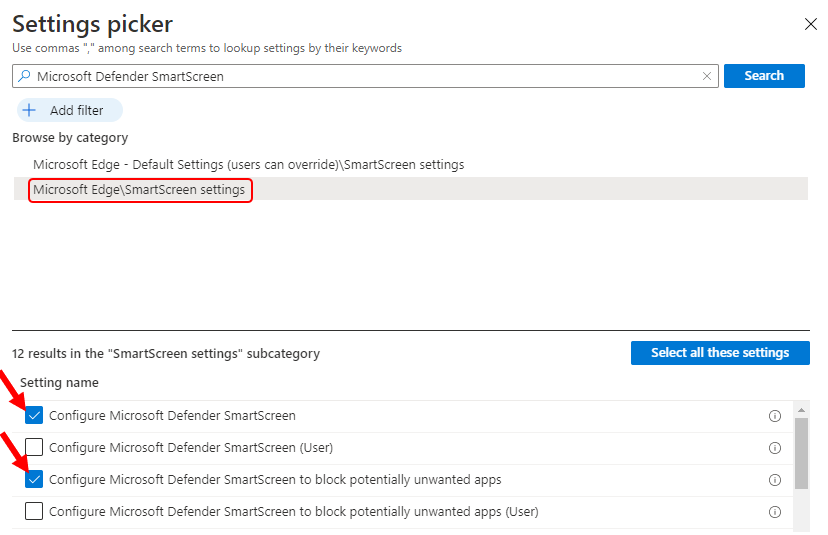
The setting is shown and configured with a default value Disabled. Set Configure Microsoft Defender SmartScreen to block potentially unwanted apps from Enabled. Click Next. Additionally, It’s good to enable the following policies –
Configure Microsoft Defender SmartScreen – This policy setting lets you configure whether to turn on Microsoft Defender SmartScreen. Microsoft Defender SmartScreen provides warning messages to help protect your users from potential phishing scams and malicious software.
Configure Microsoft Defender SmartScreen to block potentially unwanted apps – This policy setting lets you configure whether to turn on blocking for potentially unwanted apps with Microsoft Defender SmartScreen.
Potentially unwanted app blocking with Microsoft Defender SmartScreen provides warning messages to help protect users from adware, coin miners, bundleware, and other low-reputation apps hosted by websites.
Prevent bypassing Microsoft Defender SmartScreen warnings about downloads – This policy lets you determine whether users can override Microsoft Defender SmartScreen warnings about unverified downloads.
If you enable this policy, users in your organization can’t ignore Microsoft Defender SmartScreen warnings, and they’re prevented from completing the unverified downloads.
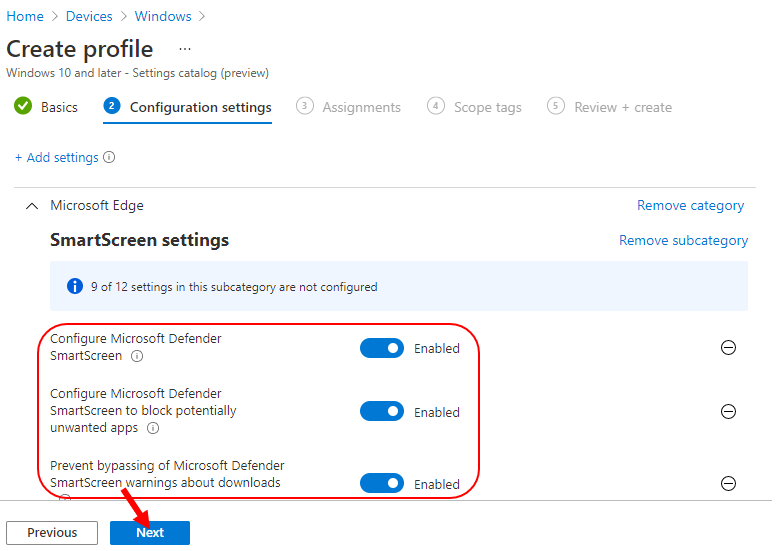
Under Assignments, In Included groups, select Add groups and then choose Select groups to include one or more groups. Select Next to continue.
You can assign a tag to filter the profile to specific IT groups in-Scope tags. Add scope tags (if required) and click Next.
In Review + create, review your settings. When you select Create, your changes are saved, and the profile is assigned.
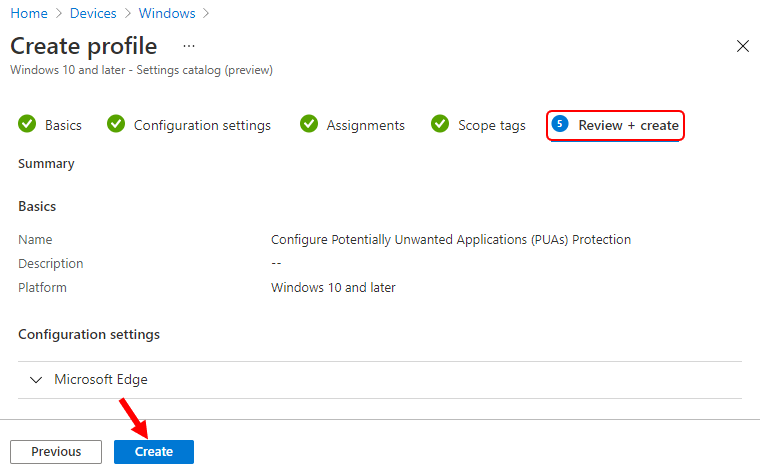
A notification will appear automatically in the top right-hand corner with a message. Here, Policy “Configure Potentially Unwanted Applications (PUAs) Protection” was created successfully.
The policy is also shown in the Configuration profiles list.
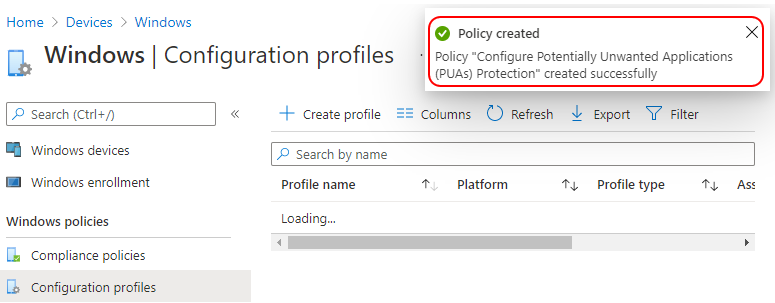
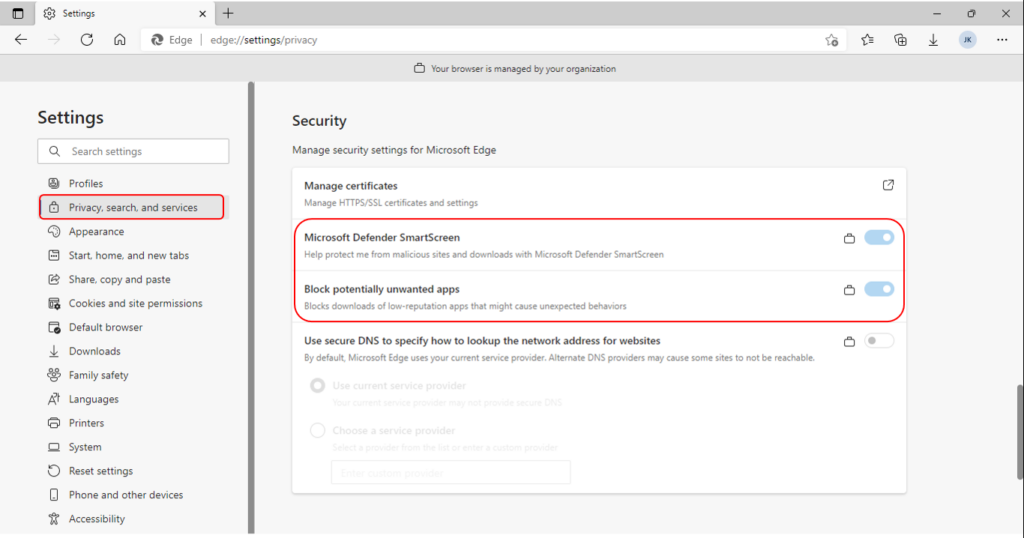
Your groups will receive your profile settings when the devices check-in with the Intune service. Once the policy applies to the devices, Open Settings in the browser and select privacy, search, and services.
Check to see that Microsoft Defender SmartScreen is turned on. Under the Security section, turn on Block potentially unwanted apps.
When Microsoft Edge detects a PUA, you will see a message when downloading a potentially unwanted app. Here is what users will know when the feature blocks a download; users can choose to keep it by tapping … in the bottom bar, choosing to Keep, and then choosing to Keep anyway in the dialog that appears.
Author
About Author -> Jitesh has over 5 years of working experience in the IT Industry. He writes and shares his experiences related to Microsoft device management technologies and IT Infrastructure management. His primary focus area is Windows 10, Windows 11 Deployment solution with Configuration Manager, Microsoft Deployment Toolkit (MDT), and Microsoft Intune.

