Some hackers are apparently shooting for the stars by attacking the agency known for its work in outer space.
A new security audit reveals that cyber bad actors hit the National Aeronautics and Space Administration (NASA) with more than 6,000 attacks during the last four years.
And the audit found that attackers did successfully introduce malware into agency systems.
But here's the biggest fact any organization can take away from the NASA audit: work from home during the pandemic led to skyrocketing problems with shadow IT. These violations by employees became the primary threat vector for the agency in the past year.
Let's look at these findings from two different angles.
NASA audit: work from home greatly increases attack surface
The audit proves what we've heard from many security leaders during our SecureWorld Remote Sessions: the pandemic and work from home have greatly increased the cyber attack surface and attack attempts.
"This year in particular NASA has experienced an uptick in cyber threats: phishing attempts have doubled and malware attacks have increased exponentially during the COVID-19 pandemic and the concomitant move to telework for much of the NASA workforce.
The Agency's cybersecurity challenges are further exacerbated by the number and variety of IT devices at NASA and the sheer volume of data the Agency maintains...."
And while it's not quite as vast as space itself, NASA's IT attack surface is significant and varied as you can see here:
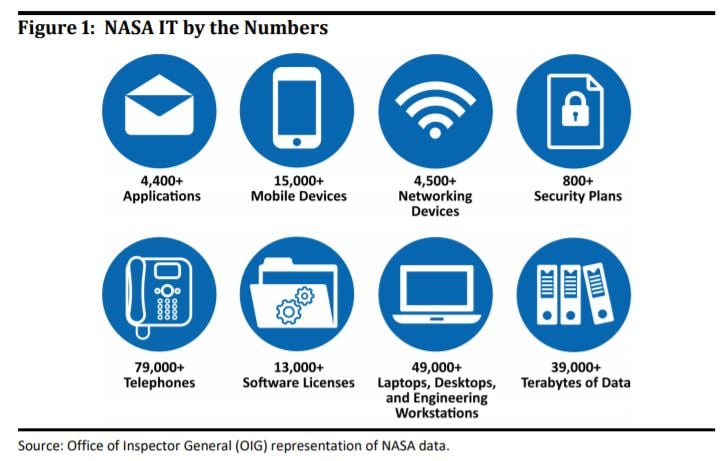
NASA audit: work from home leads to risky end-user choices
When your employees suddenly shifted to work from home during the pandemic, did you see an increasing number of IT security policy violations? Did you even have the visibility to track them?
In this case, the audit found that employees were opening the space agency to cyber threats like never before:
"According to NASA data, the Agency identified 1,785 cyber incidents in 2020... Significantly, improper use incidents—which result from a violation of an organization's acceptable use policies, such as installing unapproved software or viewing inappropriate material—increased the most, from 249 in 2017 to 1,103 in 2020, a 343 percent growth.
Further, improper use continued to be the top attack vector type in 2020."
NASA says some of these incidents would have gone unnoticed before, but a new cybersecurity solution is finally giving the agency much-needed visibility across its networks.
NASA cyber threats: insiders, third-parties, nation-states
The audit also spells out that cyberattacks against NASA's networks come from all directions: from those using NASA's supercomputing power to make money to nation-states looking for secrets. Here are three examples from the new report:
- "In 2019, a NASA contract employee used a personal computer to access NASA-owned networks and systems to mine cryptocurrency."
- "In 2019, two Chinese nationals, members of a hacking group operating in China, were indicted on criminal charges for gaining unauthorized access to a NASA computer to steal data."
- "In 2018, an account belonging to an external user was compromised and used to steal approximately 500 megabytes of data from a major mission system."
A wide-ranging list of attack vectors, for sure. The audit says NASA's cybersecurity is making progress, but is still significantly behind where it should be.
6 key areas where NASA's information security is failing
The U.S. General Accounting Office says previous audits have identified more than two dozen information security shortfalls at NASA that still need to be implemented.
In this report, auditors listed their top six concerns, ranging from strategy to mobile device management to the agency's security operations center.
How does your organization compare?
- The Chief Information Officer (CIO) has struggled to implement an effective IT governance structure that aligns authority and responsibility with the Agency's overall mission.
- NASA lacked an Agency-wide risk management framework for information security and an information security architecture.
- Pervasive weaknesses exist in NASA IT internal controls and risk management practices.
- The Security Operations Center lacks visibility and authority to manage information security incident detection and remediation for the entirety of NASA's IT infrastructure.
- NASA's cybersecurity program remained ineffective at a Level 2 out of 5 (Federal Information Security Modernization Act rating)—meaning the Agency has issued, but has not consistently
implemented, policy and procedures defining its security program. - NASA is not adequately monitoring and enforcing the business rules necessary for granting Mobile Device Management access to its network.
And the audit creates a theme around NASA's information security which focuses on the agency's architecture and fragmentation:
"NASA's ability to prevent, detect, and mitigate cyber-attacks is limited by a disorganized approach to the Agency's Enterprise Architecture. Enterprise Architecture and Enterprise Security Architecture—the blueprints for how an organization analyzes and operates its IT and cybersecurity—are crucial components for effective IT management.
Enterprise Architecture has been in development at NASA for more than a decade yet remains incomplete while the manner in which the Agency manages IT investments and operations remains varied and ad hoc.
Overall, a fragmented approach to IT, with numerous, separate lines of authority, has long been a defining feature of the environment in which cybersecurity decisions are made at the Agency. The result is an overall cybersecurity posture that exposes NASA to a higher-than-necessary risk from cyber threats."
The Inspector General's NASA Audit is smaller than the universe, but at 38 pages long, you'll find a constellation of cybersecurity data points by reading it yourself.
(Image credit: NASA, Bill Ingalls)



