Doctors are generally trusted as people who want to help others. Depending on the type of doctor, their job description is quite literally to save lives.
But one doctor from Venezuela wanted to help people in a little bit more unconventional, and criminal, way.
The U.S. Department of Justice (DOJ) unsealed charges against 55-year-old Moises Luis Zagala Gonzalez (Zagala), also known as "Nosphoros," for his use and sale of ransomware and profit sharing arrangements with other cybercriminals.
Breon Peace, United States Attorney for the Eastern District of New York, discussed Zagala:
"As alleged, the multi-tasking doctor treated patients, created and named his cyber tool after death, profited from a global ransomware ecosystem in which he sold the tools for conducting ransomware attacks, trained the attackers about how to extort victims, and then boasted about successful attacks, including by malicious actors associated with the government of Iran."
Creation of Jigsaw and Thanos ransomware
Zagala created multiple ransomware tools in his time as a cybercriminal, starting with Jigsaw. What made Jigsaw unique, at the time, was that it came with a "Doomsday" counter which tracked the number of times the end-user attempted to kill the ransomware. Zagala said "if the user kills the ransomware too many times, then it's clear he won't pay so better erase the whole hard drive."
In 2019, Zagala moved on to create a new "Private Ransomware Builder," which he called Thanos, a reference to the popular Marvel villain who destroyed half of all life in the universe with a snap of his fingers.
The Thanos software allowed users to create their own unique strain of ransomware, which they would use or sell to other cybercriminals. The DOJ shared a screenshot of what the user interface of Thanos looks like:
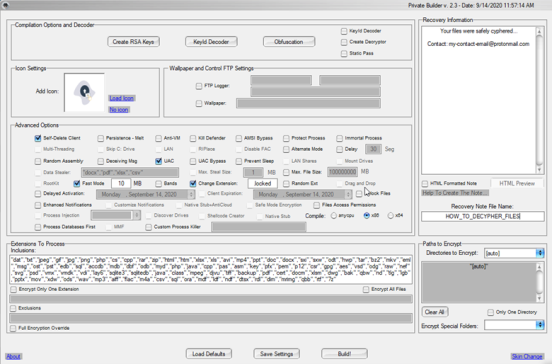
The DOJ also describes the interface:
"The screenshot shows, on the right-hand side, an area for 'Recovery Information,' in which the user can create a customized ransom note. Other options include a 'data stealer' that specifies the types of files that the ransomware program should steal from the victim computer, an 'anti-VM' option to defeat the testing environments used by security researchers, and an option, as advertised, to make the ransomware program 'self-delete.'"
Cybercriminals had two choices when it came to acquiring Thanos ransomware from Zagala. The first was that they could buy a "license" to use it for a set amount of time. The second was to join Zagala in what the DOJ refers to as an "affiliate program" in exchange for a share of the profits from the following ransomware attack.
Zagala often bragged, even on public forums, that Thanos was nearly undetectable by antivirus programs, and that "once encryption is done," the ransomware would "delete itself," making detection and recovery "almost impossible" for the victim.
"Almost" being the key word here.
A confidential human source from the FBI, referred to as "CHS-1," attempted to join Zagala's affiliate program in early May 2020, but he was hesitant at first to let in someone new. After months of back-and-forth between the two, Zagala eventually let the FBI into the program.
By May 2022, law enforcement agents conducted a voluntary interview with one of Zagala's relatives in Florida. This relative's PayPal account was used to receive illicit funds from Zagala. They also confirmed that Zagala lived in Venezuela, taught himself computer programming, and showed contact information that matched the registered email for malicious infrastructure associated with the Thanos malware.
Zagala faces up to five years in prison for attempted computer intrusion, and five years in prison for conspiracy to commit computer intrusions.
For more information, see the criminal complaint from the Department of Justice.





