This is the story of a hacker-for-hire scheme that targeted hundreds of organizations and thousands of individuals across North America and five other continents.
Clients hired a group of perpetrators to phish and hack their way across an amazing array of industry verticals like banking, education, energy, law, media, government, and more.
And there was something quite peculiar about these attacks: they almost always focused on organizations and individuals involved in controversial legal proceedings, business deals, or advocacy campaigns.
The University of Toronto's Citizen Lab uncovered the campaign and dubbed it "Dark Basin."
The Citizen Lab says this hacker-for-hire case reveals intrusion services "at a scale not previously detected."
And just wait until you find out who is accused of running this cybercrime scheme.
IT and IT security firm allegedly runs hacker-for-hire scheme
Citizen Lab researchers say the company at the center of the "Dark Basin" attacks is BellTroX InfoTech Services, an IT and IT security firm based in Delhi, India.
The company's tagline is You desire, We do!, and the site lists a litany of cybersecurity services including pentesting, vulnerability assessments, and cybercrime investigation.
Perhaps this is a case of security up front, hacking in the back. Here is the company's homepage, captured by the Wayback Machine archive:

How was the hacker-for-hire scheme discovered?
According to researchers, this investigation started with a single tip from a journalist:
"In 2017, Citizen Lab was contacted by a journalist who had been targeted with phishing attempts and asked if we could investigate. We linked the phishing attempts to a custom URL shortener, which the operators used to disguise the phishing links."
And in the world of digital forensics, you never know what might be a key piece of evidence. It turns out that a series of URL shorteners helped investigators identify who was behind these "Dark Basin" cyberattacks.
"We subsequently discovered that this shortener was part of a larger network of custom URL shorteners operated by a single group, which we call Dark Basin. Because the shorteners created URLs with sequential shortcodes, we were able to enumerate them and identify almost 28,000 additional URLs containing e-mail addresses of targets.
We used open source intelligence techniques [OSINT] to identify hundreds of targeted individuals and organizations. We later contacted a substantial fraction of them, assembling a global picture of Dark Basin's targeting."
And then there were the timestamps from the thousands of phishing attempts, most of which aligned with a typical workday in India.
Also, researchers analyzed a large number of phishing kits and log files that perpetrators left open which revealed similarities. And they found some obvious clues, like a dumb criminal who drops his credit card while he's robbing the place.
"The source code also contained several scripts that processed details including usernames and passwords entered by victims, as well as the victims' IP address. These details were both emailed to a Gmail address controlled by Dark Basin and recorded in one or more log files on the web server itself."
A long list of clues that took investigators back again and again to BellTroX InfoTech Services as the operators of "Dark Basin."
But who was hiring them? Could it be a country?
"While we initially thought that Dark Basin might be state-sponsored, the range of targets soon made it clear that Dark Basin was likely a hack-for-hire operation. Dark Basin's targets were often on only one side of a contested legal proceeding, advocacy issue, or business deal."
In other words, Citizen Lab says, someone on one side of a contentious situation would hire BellTroX to launch cyberattacks against those on the other side of that contentious issue.
Merger gone bad? You could try to phish the other party for information that could help you in the upcoming lawsuit. Political enemies playing dirty? You could hire Dark Basin to phish up some dirt of your own.
Now that we know a bit about the scheme and how it was uncovered, let's take a closer look at how it operated.
Hacker-for-hire operator creates targeted phishing emails
The phishing campaigns used by the hack-for-hire operators were both sophisticated and target specific.
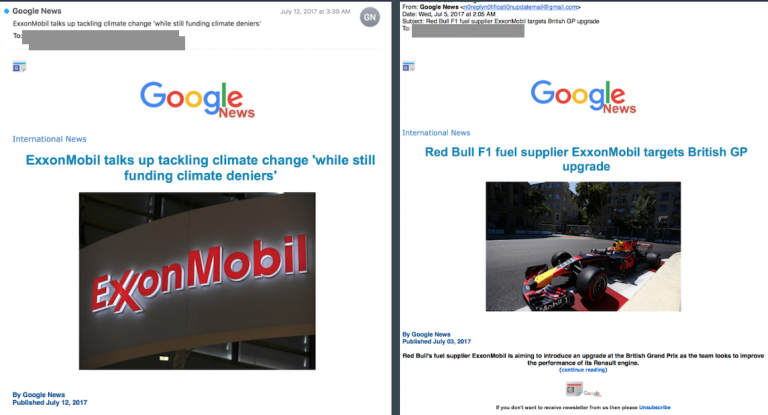
The new report highlights multiple case studies, but one of the most telling is a series of Dark Basin hacking attempts against those running the #ExxonKnew campaign.
The campaign claims petroleum giant ExxonMobil has led decades of climate deceit. And Exxon has fired back, saying don't be misled.
While both sides traded barbs via traditional and social media, the hack-for-hire scheme was operating in the background.
Someone hired the Dark Basin group to hack accounts used by those pushing the narrative against Exxon.
Citizen Lab says those #ExxonKnew targets had both personal and organizational email addresses phished with spoofed messages that were nearly impossible to resist. Some included fake news articles about Exxon's alleged cover-up. (Click to expand.)
And there were other phishing messages which appeared to be tips the anti-Exxon camp would want to read, seemingly from those within the #ExxonKnew camp:
"Notably, multiple phishing messages seemed to reference unspecified confidential documents concerning ExxonMobil.
A number of these messages impersonated individuals involved in the #ExxonKnew advocacy campaign or individuals involved in litigation against ExxonMobil, such as legal counsel."
Where did the phishing emails those who clicked a link?
Researching potential victims is the first step in the attack, targeting them with phishing emails is the second step, and that leads us to the third step.
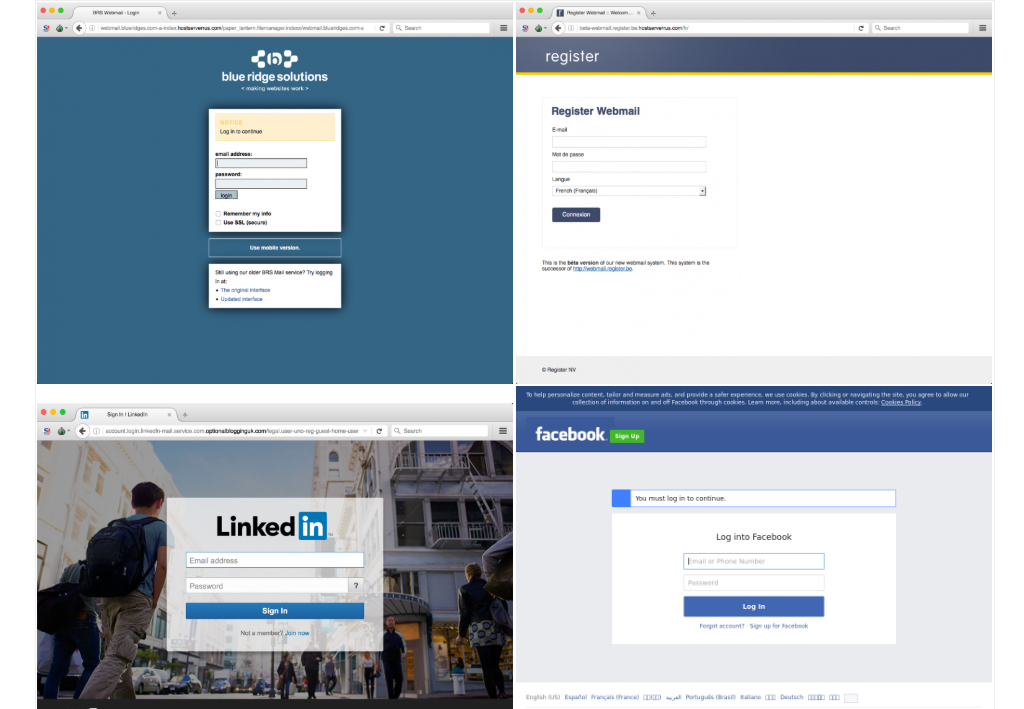
This is the part where the cybercrime operators got their victims to click on a link within the phishing email. It took them to a series of fake login pages that looked like a legitimate place to enter your username and password.
"The malicious links we discovered during our tracking each led to credential phishing sites, i.e., websites designed to look identical to popular online web services such as Google Mail, Yahoo Mail, Facebook, and others. In addition, Dark Basin operators had created phishing websites which copied the look and feel of specific web services used or operated by the target or their organization."
This is similar to the type of cyberattack uncovered against the World Health Organization during the heart of the COVID-19 pandemic. Listen to our podcast interview with the cyber attorney CISO who discovered it:
And phishing was only one of the ways the hack-for-hire services went after their targets.
Here is an overview of other cyberattack attempts by the hack-for-hire operators across a wide range of targets:
"Other ruses included fake Twitter direct messages and other correspondence purporting to concern climate change advocacy. Dark Basin also regularly employed more generic phishing emails using the same infrastructure. We observed a similar mix of topic-specific and generic attempts by Dark Basin against targets in other clusters, such as targeted hedge funds. Dark Basin also regularly made use of third-party link tracking services in their messages.
In at least one case, Dark Basin repurposed a stolen internal email to re-target other individuals. This incident led us to conclude that Dark Basin had some success in gaining access to the email accounts of one or more advocacy groups."
How significant is the hacker-for-hire industry
Is this an isolated case where you can hire a hacker to do your dirty work? The leaders at Citizen Lab highly doubt it:
"Dark Basin's activities make it clear that there is a large and likely growing hack-for-hire industry. Hack-for-hire groups enable companies to outsource activities like those described in this report, which muddies the waters and can hamper legal investigations.
Previous court cases indicate that similar operations to BellTroX have contracted through a murky set of contractual, payment, and information sharing layers that may include law firms and private investigators and which allow clients a degree of deniability and distance."
And SecureWorld News can confirm there are either a number of operators offering questionable hacking services, a growing appetite for hacker-for-hire services, or both.
We receive a steady number of hacker-for-hire advertisements that we block from appearing as comments below stories on our news site.
Some claim to be from hacking groups with a long track record:
"Are you in desperate need of hackers for hire? Do you need to keep a watchful eye on your spouse by gaining access to their emails, even constant updates on thier geo-location?
Whatever services you may require legal or illegal, Ranging from Bank Jobs, Flipping cash, Criminal records, DMV, Taxes, if you are looking to get any hack espionage accomplished . need funds urgently ? need your grades changed ? thorough background check or Just Name it, We can guarantee to get the job done.
We're a group of professional hackers with 25 Years+ experience. Contact via telegram+1 919-346-*****.guaranteed a solution to whatever problem you have Its that easy,Do try us out today."
While other ads we block claim to be from satisfied customers and point back to a single hacker who allegedly helped them out:
"If you ever want to change or up your university grades contact *****golden hacker he'll get it done and show a proof of work done before payment. He's efficient, reliable and affordable. He can also perform all sorts of hacks including text, whatsapp, password decrypt,hack any mobile phone, Escape Bancruptcy, Delete Criminal Records and the rest Email: *****goldenhacker at *****.com"
The Citizen Lab says this commercialization of hackers-for-hire services can undermine democracy, and it has turned over many additional details of its investigation to the U.S. Department of Justice, hoping it changes the threat landscape.
"Despite a previous DOJ indictment of the BellTroX Director, as well as indictments in other hack-for-hire cases, the companies that provide these services publicly promote their activities. This suggests that companies and their clients do not expect to face legal consequences and that the use of hack-for-hire firms may be standard practice within the private investigations industry."
That leaves us with a final question right now: who, exactly, has been hiring Dark Basin to launch the phishing attacks detailed in this story and the thousands of others that the Citizen Lab tracked?
Researchers say they're not ready to answer that question just yet. SecureWorld will let you know if and when they do.