Earlier this year, 36 journalists, producers, anchors, and executives at Al Jazeera had their personal phones hacked.
Their phones were hacked through the use of an exploit chain known as KISMET, an invisible zero-click exploit in iMessage. In July of this year, KISMET was a successful Zero-Day attack against at least iOS 13.5.1 and could hack the Apple iPhone 11.
Citizen Lab believes that the journalists were hacked by four operators from NSO Group's Pegasus. Pegasus spyware is a phone surveillance solution that enables customers to remotely exploit and monitor devices. NSO Group sells its surveillance technology to governments around the world, and watchdog groups say the company's products are often found to be used in surveillance abuses.
These particular attacks used servers in Germany, France, the U.K., and Italy, and used cloud providers Aruba, Choopa, CloudSigma, and DigitalOcean.How do zero-click attacks work in iOS?
One of the journalists who was attacked, Tamer Almisshal, is an anchor on Al Jazeera's Arabic language channel. Almisshal has reported on a great number of politically sensitive topics in the Middle East, including the Bahrain government's hiring of a former Al-Qaeda operative for an assassination program and the Saudi killing of Jamal Khashoggi.
He was concerned that his phone had been hacked, so he contacted Toronto's Citizen Lab and agreed to let them install a VPN application that would give researchers a chance to track metadata associated with his internet traffic.
The figure below displays a timeline of the attack, according to Citizen Lab:
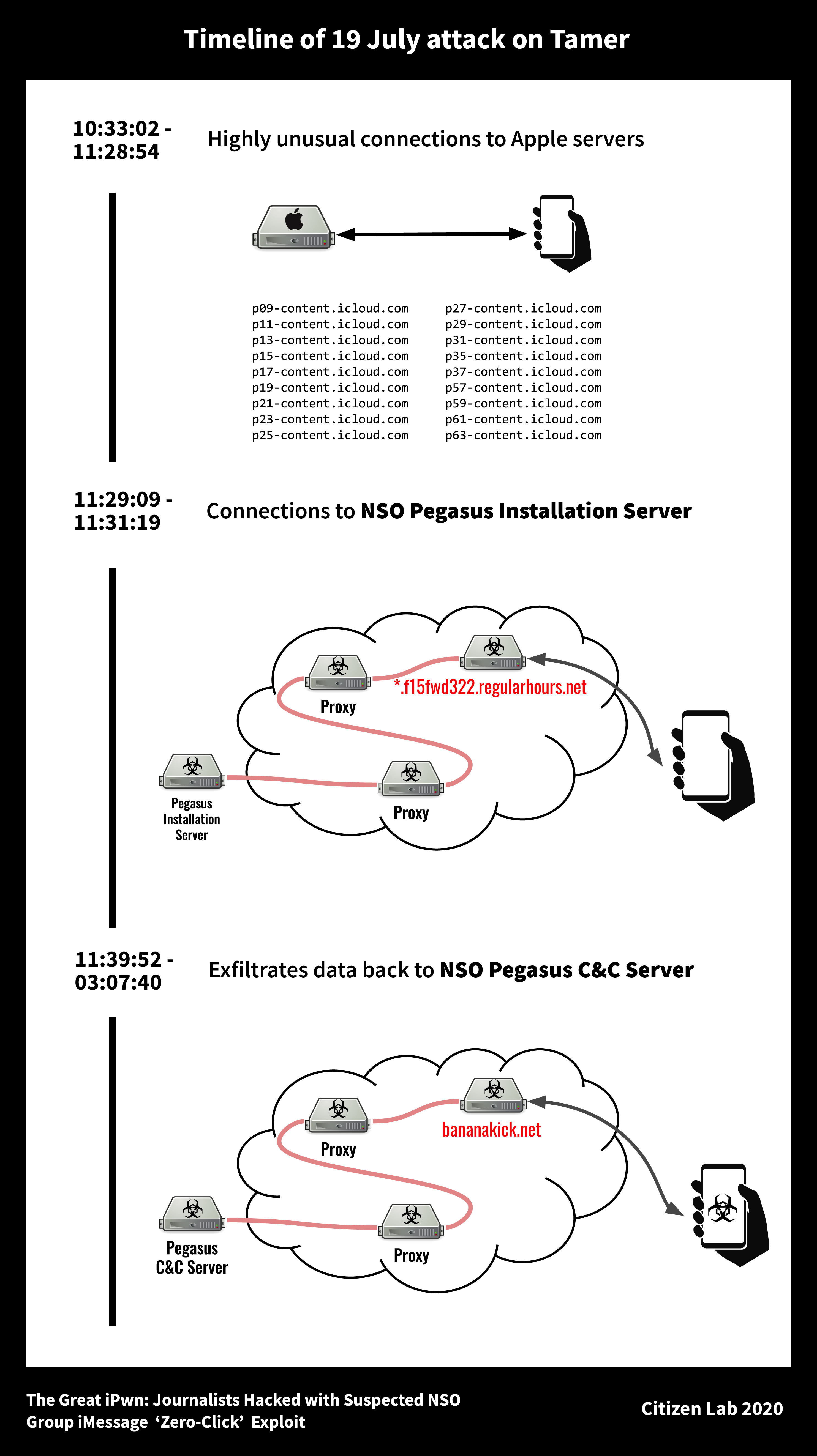
On July 19, researchers found that Almisshal's phone suddenly visited a website associated with NSO Group's Pegasus spyware, which is used in the process of hacking a target.
Citizen Lab says this was due to an apparent Apple related exploit. Here is why:
"In the 54 minutes prior to accessing the website, there was an unusually large amount of connections to iCloud Partitions. In 3,000 hours of monitoring his phone, it connected to iCloud partitions 258 times. 228 of these occurred within the 54 minutes prior to accessing the Pegasus Installation Server.
16 seconds after the final connection to Pegasus, Almisshal's phone communicated with three IP addresses over the following 16 hours. His phone had not previously communicated with these IPs and has not since.
From these communications, there was a total of 270.16MB of upload, and 15.15MB of download, and each IP returned a valid TLS certificate for bananakick.net. His phone did not set the SNI in the HTTPS Client Hello message and it did not perform a DNS lookup for bananakick.net. It is assumed that the three IPs were Pegasus command and control (C&C) servers."
What can this Pegasus iOS attack do?
Citizen Lab was able to run an analysis of device logs from a live Pegasus infection. Here is what researchers discovered from the analysis:
"We obtained logs from an iPhone 11 device inside Al Jazeera networks while it was infected. Our analysis indicates that the current Pegasus implant has a number of capabilities including: recording audio from the microphone including both ambient 'hot mic' recording and audio of encrypted phone calls, and taking pictures. In addition, we believe the implant can track device location, and access passwords and stored credentials."
The logs show a process "launchafd" on the phone that was communicating with four Pegasus IP addresses. The process was located in flash memory in a specific folder. That folder appears to be for iOS updates, but they believe it will likely not survive an iOS update.
The logs from the phone show that the spyware was accessing different frameworks on the phone, including the Celestial.framework and MediaExperience.framework, which can be used to record audio and camera data. The spyware also accessed the LocationSupport.framework and CoreLocation.framework, which can be used to track the user's location.
Spyware attacks becoming harder to detect
Commercial spyware companies like NSO Group enable nation-state cyber actors with the belief that they are acting in secret, so they can target individuals with powerful voices like journalists. And these attacks are becoming more and more difficult to track.
Citizen Lab explains:
"The current trend towards zero-click infection vectors and more sophisticated anti-forensic capabilities is part of a broader industry-wide shift towards more sophisticated, less detectable means of surveillance. Although this is a predictable technological evolution, it increases the technological challenges facing both network administrators and investigators.
While it is still possible to identify zero-click attacks—as we have done here—the technical effort required to identify cases markedly increases, as does the logistical complexity of investigations. As techniques grow more sophisticated, spyware developers are better able to obfuscate their activities, operate unimpeded in the global surveillance marketplace, and thus facilitate the continued abuse of human rights while evading public accountability."
Journalists have been increasingly targeted with spyware by authoritarian governments that want to silence prominent voices in the media.
Citizen Lab says there are at least 50 publicly known cases of journalists and others in the media who have been targeted with NSO spyware. These attacks have come from countries like China, Russia, Ethiopia, Mexico, the UAE, and Saudi Arabia.
[READ: The Great iPWN, from Citizen Lab]





