The point-and-click deployment tools in the Spring Update of the Windows Virtual Desktop (WVD), the technical preview for Config Manager 2004 that makes it easier to manage on-premise devices from the cloud in the new Microsoft Endpoint Manager admin centre in Azure, and the way Endpoint Manager and Azure AD now use the same control plane to manage both devices and access: these remote-friendly features, have been in development for a while – but they’re certainly timely.
Microsoft set up 32,000 desktops in WVD for its own developers in two days and many WVD customers are doing even larger deployments. One WVD partner alone (Nerdio, which has its own WVD management service) has deployed virtual desktops for over 300,000 enterprises since March, ranging from 150,000 to a million desktops.
With so many people working from home, VDI and Desktop as a Service (DaaS) has suddenly become relevant to organizations that are used to physical devices and that don’t necessarily have experience in managing and securing virtual desktops, so managing it needs to be easier. When WVD first launched, setting it up required understanding Azure resources and manually connecting it to your Azure AD tenant; you could only monitor and manage your WVD tenant through PowerShell or by hosting your own Azure WebApps, and scaling out for more users meant running the same deployment again.
“Customers who did have that expertise were able to spin up 10,000 VMs really quickly and get a lot of benefit from that,” Melissa Grant, director of product marketing for Microsoft 365, told TechRepublic. “But we can make it a simpler scenario for folks who may be endpoint managers but who don’t have experience with Azure, who didn’t need to do that before but who need to do that now, because virtual machines are going to be the best solution for their employees who didn’t have a corporate-procured laptop or weren’t able to take it with them when they went home. They’re having to enable people to work on personal machines and they’re trying to acquire and remotely provision and deploy new machines.”
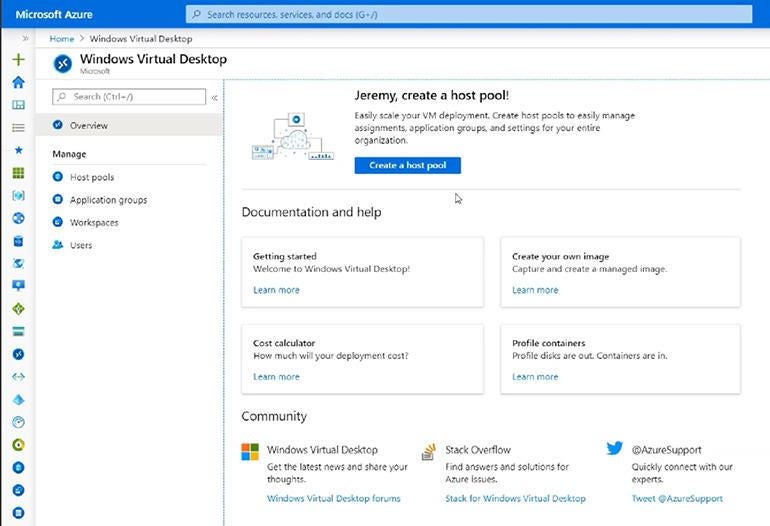
Now that WVD is an Azure Resource Manager (ARM) service, you can deploy, manage and scale it from the Azure portal using a simple new interface.
As an ARM service, WVD is also easier to connect to other Azure services that you may already be using. Using ARM you can publish RemoteApps and desktops not just to individual users, but also to Azure AD Groups, and you can use Azure RBAC to control permissions for every WVD ARM object, giving you a lot more granularity for delegating control than you get with the four admin roles in WVD itself.
You can also monitor WVD through Log Analytics rather than having to trawl through logs with PowerShell, so you can run Kusto queries or Power BI reports on the data. (If you’re still using PowerShell to manage WVD, the RDS module has been replaced with AzWvd; run Install-Module Az.DesktopVirtualization to add the new commands.)
SEE: 250+ tips for telecommuting and managing remote workers (TechRepublic Premium)
You can monitor WVD desktops with Microsoft Defender ATP like any other device, and combine that information with the Windows event logs and the WVD diagnostic logs in Azure Sentinel so you can do full threat hunting across virtual desktops, VMs and other resources. The process for setting that up is much simpler if you’re managing WVD with the new Azure Resource Manager objects than with the existing tools.
Although you can start using it now, the Spring Update is still in preview and you can’t manage existing WVD desktops with the new tools; Microsoft will have a conversion tool to migrate them to ARM before general availability later in 2020.
Also coming later in the year is the option to choose where the metadata and configuration information for your WVD tenants is stored: that’s now separate from the operational WVD data. So far that’s just in the US, only with the choice of more US regions, but you will soon be able to choose locations in Europe and later globally.
Connecting cloud and Config Manager
Connecting many more staff by VPN isn’t always easy to scale quickly and some organisations have told staff to limit work during core hours or consider slowing down security patching or reducing their disaster recovery options to protect VPN capacity. Setting up split tunnelling for Office 365 and Config Manager traffic and doing more device management from the cloud reduces VPN usage without increasing security risks. Microsoft estimates that getting the Patch Tuesday updates to Windows from Config Manager using the Azure Cloud Management Gateway would cost eight cents per PC and not put any load on your VPN.
The next step is the new tenant attach in Endpoint Manage; that’s a halfway house between using Config Manager on-premises and full co-management with Intune that Grant says will act as “a lower barrier to entry”.
“This allows you to take those traditionally managed devices, and get the benefits of a cloud service,” Grant said. “IT pros have a consolidated view of all the devices in their estate, whether those devices were managed by Config Manager, or whether they’re managed by Intune. They can see one viewpoint of all the devices, and take actions that apply to all of those devices directly from the Microsoft Endpoint Manager admin centre. You don’t have to go to separate portals, and you don’t have to take separate actions to use cloud services and cloud management across all of those devices.”
Microsoft has worked with some organisations provisioning 100,000 new laptops through Endpoint Manager and Autopilot so they could send them straight to employees’ homes. “Now they can manage all of those in a single unified console and take action against those to ensure they’re all secure, ensure that there’s no data leakage, and ensure that identities are guaranteed as well,” said Grant.
SEE: Cross-training toolkit (TechRepublic Premium)
The ability to use MFA and single sign-on for as many cloud apps as you want (whether that’s a MongoDB database, a Cisco Meraki IT dashboard or Salesforce) will be useful for organisations who have to move away from on-premise apps quickly.
That’s available to any customer with an Azure AD Premium licence. “Any Microsoft customer with a subscription for a commercial online service can use single sign-on and then be able to protect access with multi-factor authentication at no extra cost, because identity is that first jumping off point to making sure that you can have a secure and reliable remote-work scenario,” Grant said. “We guarantee the identity, we can then apply management, whether that is co-management in Endpoint Manager or cloud only [Intune] and ensure we have the right set of applications getting out to those users, whether those are corporate and line-of-business applications, or education applications.”
But having Azure AD and Endpoint Manager use the same control plane for identity and access is a much bigger step forward than just enabling SSO. Whether they’re using a virtual desktop or a cloud app, collaborating on documents or joining a Teams meeting, all those devices can do things like attesting to their level of security before getting access: you can make sure that the device is managed, that it’s patched and has up-to-date anti-malware and encryption turned on, or even that there’s a timeout to lock the device and have the user enter a PIN if they walk away and come back. That’s a big step towards implementing ‘zero trust’ security that offers much more protection than applying group policies to lock down device features, and has much less impact on how quickly PCs boot up.
More apps on more devices with less bandwidth
Intune is also getting a long-awaited expansion of the management controls for macOS devices, and more control over Outlook Mobile through Intune, because lockdown means dealing with a wider range of devices.
The macOS management doesn’t replace Microsoft’s partnership with JAMF, which will continue, Grant confirmed. “This adds some additional controls customers have been asking for to do scripting and task automation that make configuring Macs easier within the Endpoint Manager console.”
The Intune app protection policies for Outlook Mobile – limiting which storage work and school accounts can access on iOS and Android – are to protect both company data and employee privacy as work and home overlap so very much, Grant explained.
“When people are going between personal and work on a mobile device, or in a BYOD scenario — whether they intended it to be BYOD or that’s just what they’re left with — we’re providing security so they don’t accidentally attach a personal file to a work email in Outlook Mobile. Maintaining privacy is still really important and people are multitasking; they’re working in new ways they’re less familiar with. We want to make sure that we’re not allowing malicious content into the corporate environment, but we’re also protecting people’s privacy by helping them to keep their personal and their work estates separate.”
Unified app delivery is partly about removing confusion by combining two app galleries, Config Manager Software Centre and Azure AD My Apps, in the new Company Portal from Intune. Normally, having those separate might make sense, Grant suggests. “Maybe part of the organisation is a highly mobile workforce that’s really used to using Company Portal and the folks back at headquarters were using Software Centre. But now those headquarters folks are also out in the field, so to speak, so we just wanted to make it easier for an IT admin to deploy apps securely regardless of what portal they’re going through.”
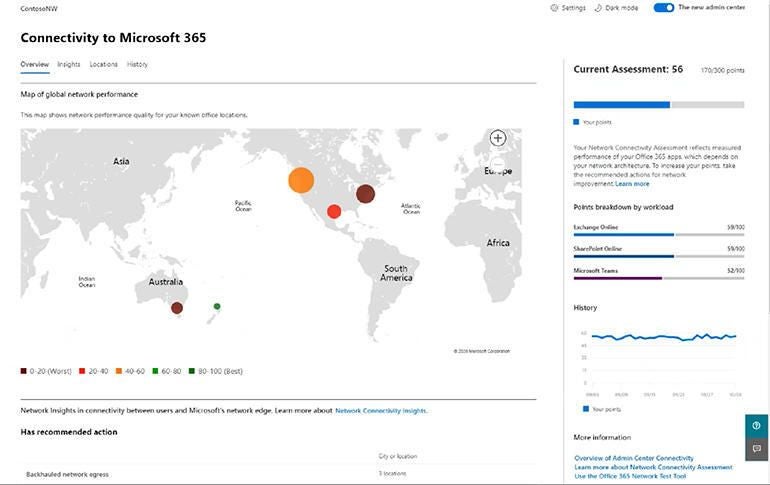
But it also works with the new Network Connectivity and Endpoint Analytics in Endpoint Manager’s Productivity Score to let IT admins help speed up employees.
“We’re able to provide visibility into which worksite locations have network challenges, and take a look at whether or not there is some sort of issue with the network that could be preventing people from getting their work done,” said Grant. Previously that was useful to apply policies to office locations with poor connectivity or latency issues; now it lets IT staff make suggestions. “If you’re seeing connectivity issues in an area, you might want to recommend that folks utilise web apps, you might reduce packet size, you might go about your patching in a different ways to put less pressure on the broadband. If they’re noticing that their home broadband is slow they might suggest to that employee, ‘why don’t you use Company Portal on your mobile phone to get access to that application?'”
Endpoint Analytics will show not just the health of devices, but also what is slowing them down, before a frustrated employee raises a help-desk ticket. “They can see where things like Group Policy, or the lack of an update or maybe a really klugey application is slowing down performance,” Grant said.
Strip away the unnecessary agents and the draconian policies, and Microsoft suggests any SSD-based laptop should be able to match the 23 seconds from cold boot to being able to open a web browser that Microsoft 365 corporate vice-president Brad Anderson boasts about getting on his PC.