It’s Time For Sales Leaders To Coach Sellers Like Athletes
Forrester IT
APRIL 15, 2024
Sales managers now have the visibility needed to coach sellers beyond the basics.

Forrester IT
APRIL 15, 2024
Sales managers now have the visibility needed to coach sellers beyond the basics.

IT Toolbox
APRIL 15, 2024
State-sponsored hackers are exploiting a new zero-day flaw in Palo Alto Networks firewall software. Find out about the flaw, which impacts devices running PAN-OS, and the nature of the threat. The post Palo Alto Zero-Day Flaw Exploited Through Python Backdoor appeared first on Spiceworks.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Forrester IT
APRIL 11, 2024
Tech leaders are rethinking their strategic partnerships because silicon matters again. Whether your infrastructure is in the cloud, on-premises, or at the edge, or any combination thereof, the accelerators and specific features in your silicon can make an enormous difference to what you can do with AI and how quickly you can roll it out.

Social, Agile and Transformation
APRIL 15, 2024
Ten years ago, it was less likely for CIOs and Digitial Trailblazers to form a partnership with their CHRO and human resources departments. At that time, IT was largely focused on run and grow initiatives with little focus on transformation – and the term digital transformation was in its infancy.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Anoop
APRIL 12, 2024
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post Declarative Device Management A New Way of Managing Apple Devices appeared first on HTMD Community Blog #1 Modern Device Management Guides by Malepati Naren.

Information Week
APRIL 15, 2024
Leaders expect AI to reshape business, but readiness varies. Here’s why it's crucial for CEOs, CIOs, and CTOs to develop responsible AI safety and innovation strategies now.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

IT Toolbox
APRIL 10, 2024
Learn why protecting data against cyber threats is paramount this Tax Day. The post Safeguard Your Data and Financial Future This Tax Season appeared first on Spiceworks.

Tech Republic Security
APRIL 12, 2024
Apple recommends that iPhone users install software updates, use strong passwords and 2FA, and don’t open links or attachments from suspicious emails to keep their device safe from spyware.

Anoop
APRIL 10, 2024
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post Microsoft is Working to Fix Intune 23H2 Security Baselines Issue appeared first on HTMD Community Blog #1 Modern Device Management Guides by Gopika S Nair.
Information Week
APRIL 12, 2024
Adoption of AI continues, further fueled by generative AI. Like with all things tech, the hype needs to be tempered with a realistic expectation of results.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.
Forrester IT
APRIL 10, 2024
Businesses are increasingly reliant on technology to drive growth and innovation in a rapidly evolving digital landscape. The growing complexity of IT infrastructures creates a daunting task to manage and optimize systems especially while maintaining a vital business-IT alignment. This is where AIOps and observability come into play.

IT Toolbox
APRIL 10, 2024
Consumers are demanding more videos in their buying journey. So, how are companies meeting the demand, what works for their video strategies, and what resonates with the audience? Check out a few key insights from Wistia’s latest study. The post Product, Educational, and Instructional Videos Remain Most Popular Among Consumers appeared first on Spiceworks.

Tech Republic Security
APRIL 12, 2024
Research has found that criminals can demand higher ransom when they compromise an organisation’s backup data in a ransomware attack. Discover advice from security experts on how to properly protect your backup.

Anoop
APRIL 10, 2024
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post How to Deploy PPPC Utility on macOS using Intune appeared first on HTMD Community Blog #1 Modern Device Management Guides by Snehasis Pani.

Advertisement
You’ve read the PMBOK® Guide several times, taken the certification exam for project managers, passed, and you are now a PMP®. So why do you keep making rookie mistakes? This whitepaper shows 20 of the most common mistakes that young or inexperienced project managers make, issues that can cost significant time and money. It's a good starting point for understanding how and why many PMs get themsleves into trouble, and provides guidance on the types of issues that PMs need to understand.

Information Week
APRIL 12, 2024
Not only does licensing data for AI development provide the obvious benefit of avoiding protracted (and public) battles on the world stage, but it also provides many convenient side benefits.

IT Toolbox
APRIL 9, 2024
The United States government is dispensing billions of dollars in incentives and loans as part of the CHIPS and Science Act passed by Congress in August 2022. TSMC and Samsung have emerged as the third and fourth beneficiaries of billions of dollars available under the U.S. CHIPS and Science Act after GlobalFoundries and Intel. The post U.S. Gov Subsidizes Domestic Chip Production With $6.6B Incentives for TSMC and Samsung Under CHIPS Act appeared first on Spiceworks.

Tech Republic Security
APRIL 9, 2024
Discover the top open-source password managers for Windows. Learn about the features and benefits of each to determine which one is the best fit for your needs.

TechSpot
APRIL 12, 2024
Andy Young, an ex-Microsoft senior software engineer, posted a message on X/Twitter bemoaning that even with his $1,600 Core i9 CPU and 128 GB of RAM, Windows 11 Start menu's performance is often awful.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Information Week
APRIL 10, 2024
Evenness founder and CEO Eve Logunova-Parker previews her upcoming keynote presentation for the ‘Strategies for Maximizing IT Automation’ live virtual event on Thursday, March 28.
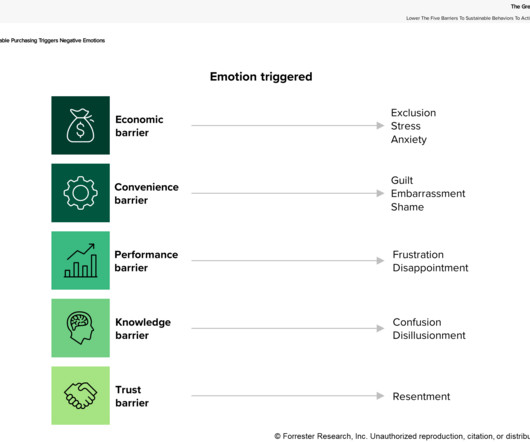
Forrester IT
APRIL 15, 2024
Learn the five most common barriers impeding widespread customer adoption of sustainable offerings and how to encourage sustainable behaviors among B2C buyers.

IT Toolbox
APRIL 9, 2024
Home improvement retailer Home Depot confirmed with multiple publishers that it suffered a data break due to a third-party SaaS vendor inadvertently exposing a subset of employee data. IntelBroker, the threat actor behind the attack claims it has the information of 10,000 Home Depot employees. The post Home Depot Data Compromised Through Third-Party SaaS Misconfiguration appeared first on Spiceworks.
Tech Republic Security
APRIL 11, 2024
Find the best open-source password managers to keep your sensitive information secure and easily accessible. Explore top options for protecting your passwords.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

CIO Business Intelligence
APRIL 12, 2024
Global banks and investment firms are currently mulling plans to replace entry-level financial analyst positions with artificial intelligence (AI), with as many as two-thirds of these positions potentially on the chopping block. This anticipated move could completely transform how these companies hire new employees and how they manage and deliver the technology employees use.

Information Week
APRIL 10, 2024
Some of the major IT trends in 2024 aren’t a surprise, but they do require more critical thinking to drive value.
Forrester IT
APRIL 12, 2024
This blog post is a brief overview of the 2024 B2B Summit North America session, "Building a Connected Messaging Team That Drives Alignment," where VP, Principal Analysts Barry Vasudevan and Ian Bruce will discuss current state of B2B messaging, companies that get it right, and how to build your connected messaging team.

IT Toolbox
APRIL 12, 2024
Over 30,000 attendees and 2,500 partners flocked to Google Cloud Next 2024 in Las Vegas this week. Google Cloud Next 2024 also saw the company’s renewed resolve for generative AI optimization and AI in general. Here’s a recap of the most important highlights from the company’s flagship cloud event. The post The Road To AI Lies Through the Cloud: Google Cloud Next 2024 Highlights appeared first on Spiceworks.

Advertisement
Outdated or absent analytics won’t cut it in today’s data-driven applications – not for your end users, your development team, or your business. That’s what drove the five companies in this e-book to change their approach to analytics. Download this e-book to learn about the unique problems each company faced and how they achieved huge returns beyond expectation by embedding analytics into applications.

Tech Republic Security
APRIL 15, 2024
Our review methodology for VPNs provides you with a reliable assessment of the best solutions based on the key factors analyzed.

GeekWire
APRIL 15, 2024
Inside the attic where Galvanick got its start. From left: Josh Steinman; Brandon Park; and Feliks Pleszczynski. (Galvanick Photo) Josh Steinman spent four years working as a senior director inside the National Security Council at the White House. One of his biggest takeaways from that experience was the vulnerability of industrial operations that were becoming more digitized — and more susceptible to cyberattacks.

Information Week
APRIL 10, 2024
As the trailblazers of organizations' modernization journey, CIOs must consider three key strategic factors before starting such a journey to maximize value and minimize risk.

Forrester IT
APRIL 11, 2024
ZT strategies are often undermined by overly ambitious or haphazard implementation plans that ultimately become incomplete projects and end up stalling or getting scrapped. Successful zero trust implementations tackle fundamental organizational and technology problems before embarking on ambitious transformation projects.

Advertisement
Project managers are now spending more time managing strategic projects where the scope is susceptible to changes as the projects progress. Scope change control is now becoming a critical component of project management requiring project teams to become more active in solving problems and making decisions. Scope change control will require collaboration with stakeholders and possibly government agencies.
Let's personalize your content