Mobile private network deployment growth brings wins for telcos
TM Forum
AUGUST 12, 2021
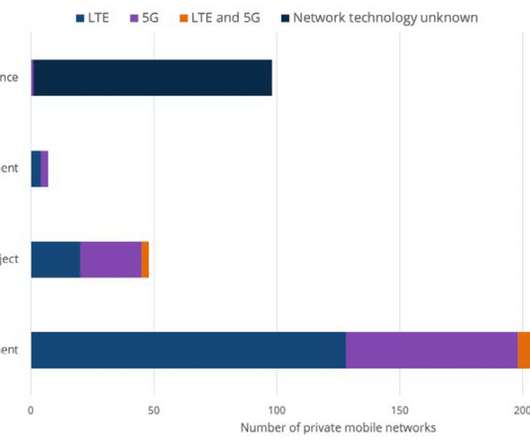
The Global Mobile Suppliers Association’s (GSA's) latest figures for 5G or LTE mobile private network (MPN) deployments and pilots show that communication service providers (CSPs) are winning MPN business amid stiff competition. Recent wins by communication service providers to supply 5G mobile private networks include.

















































Let's personalize your content