How to secure your internet activity on iOS devices
Tech Republic Security
MAY 6, 2022
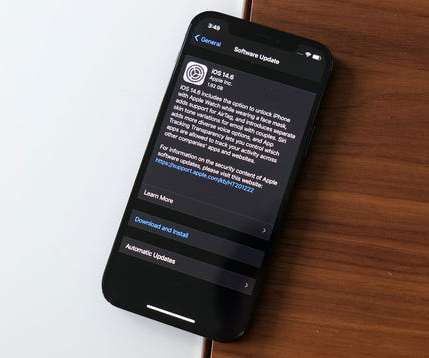
Learn about the on-device and network security options available to you in order to supercharge your internet security when browsing the web and using apps on iOS. The post How to secure your internet activity on iOS devices appeared first on TechRepublic.
















































Let's personalize your content