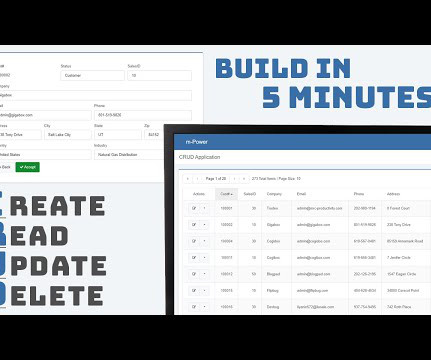
Navigating Cloud Cost Complexity and Security
CIO Business Intelligence
OCTOBER 31, 2023
In the ever-evolving landscape of cloud computing, today’s leading enterprises are seeking ways to optimize their operations and enhance their security measures. Cloud costs and security are two critical aspects that every organization must carefully manage, and they are more closely intertwined than you might think.















































Let's personalize your content