Let’s discuss the Latest MDE Architecture Changes to enhance the onboarding experience. This post will explore two interesting Microsoft Defender for Endpoint (MDE) aspects. Firstly, let’s explore the exciting enhancements that Microsoft has introduced to the MDE Onboarding process.
These improvements aim to streamline and optimize the experience of getting your devices up and running with MDE, making it easier than ever to support your endpoint security. The second topic there is fantastic news for device management in MDE.
We have an article highlighting how to Enable New MDE Security Settings Management Experience. This feature promises to revolutionize how security teams manage endpoint security settings across diverse platforms like Windows, macOS, and Linux.
You can now easily enrol your devices into Intune, allowing for seamless management of MDE policies, baselines, and other security settings-related policies. This integration with Intune empowers you to efficiently handle devices that may not be suitable for direct Intune enrollment. It opens up possibilities for managing endpoint security, catering to diverse device scenarios.
- MDE Troubleshooting Tools Explained
- Microsoft Defender for Endpoint Portal Walkthrough
- Get Microsoft Defender for Endpoint Product Comparison and License Assignment Options
What is the New Architecture Change with MDE?

Some onboarding enhancements exist for non-Intune enrolled or non-Azure ID hybrid Azure AD joint devices. You can create security settings policies in MDE in Intune portal. There are differences between Intune-managed and MDE-managed devices.
Citrix VDI/AVD Non-Persistent Supported for this MDE Scenario?

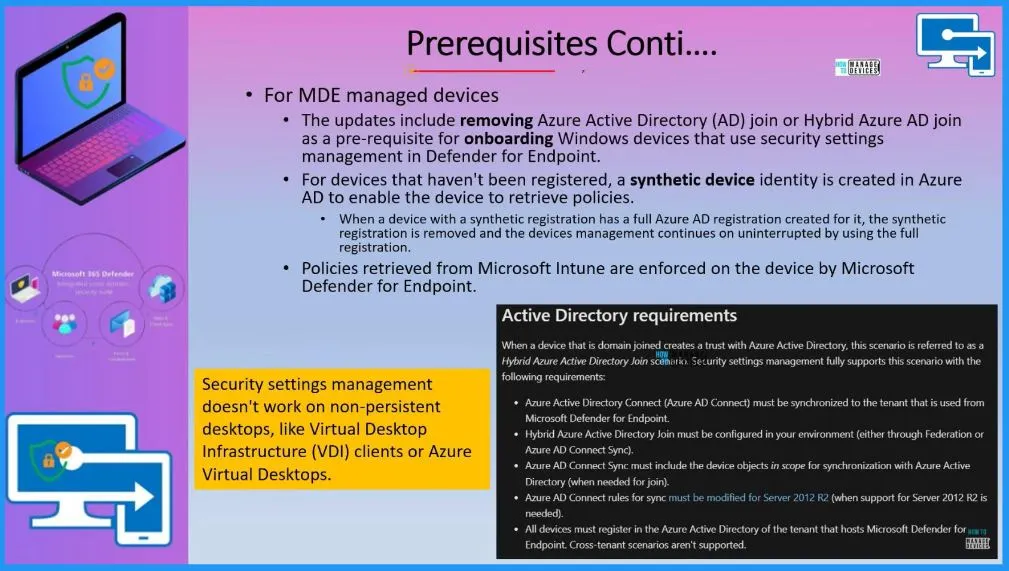
Security settings management doesn’t work on non-persistent desktops, like Virtual Desktop Infrastructure (VDI) clients or Azure Virtual Desktops.
What is MDE Synthetic Device Registration Removal?
When a device with a synthetic registration has a full Azure AD registration created for it, the synthetic registration is removed, and the device’s management continues uninterrupted by using the full registration.
MDE Only Enrollment is Available for Workgroup Joined Devices?

Yes, MDE only enrollment is available for Workgroup joined devices along with Azure AD or Hybrid Azure AD joined devices, as explained in the below section of this post.
Latest MDE Architecture Changes to Remove Onboarding Challenges
In this informative video, we will delve into two exciting topics that are revolutionizing Microsoft Defender for Endpoint (MDE). Firstly, we will explore the groundbreaking enhancements to the MDE onboarding process, eliminating the Azure AD (Entra ID) join or hybrid Azure AD join requirement.
The second topic we will cover is MDE-managed devices. The great news is that you no longer need to enrol on Intune to manage security settings policies on these devices.
Endpoint Security Settings
With the recent enhancements in Microsoft Defender for Endpoint, there is a new centralized location where you can now create security settings for MDE. The security settings help you to secure the managed devices. You can easily apply the security policies to the devices.
- Organizations follow various security standards; the CIS benchmark is the most common std used.
- Group policy settings are the most popular method to implement security policies.
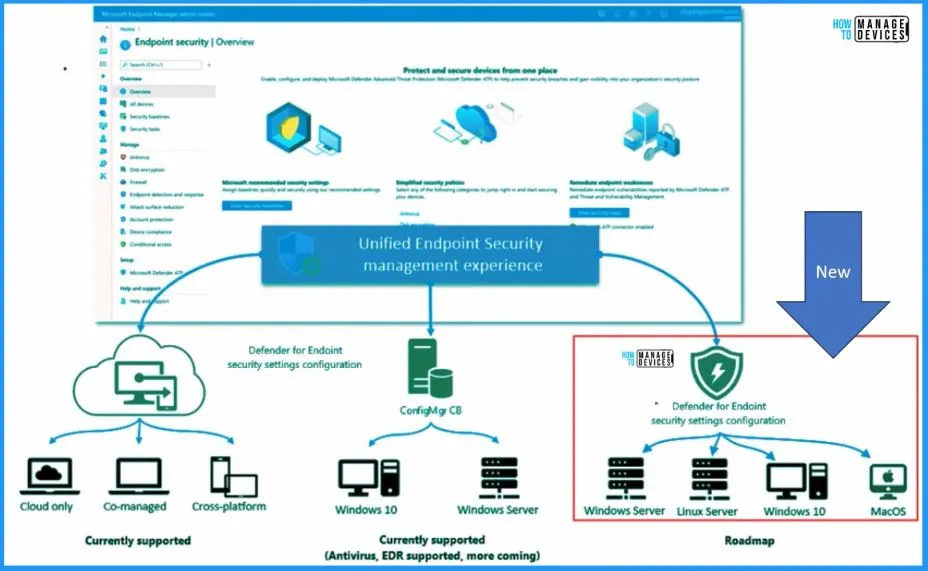
Unified Endpoint Security Management Experience
This is the New enhancement that Microsoft introduced for Defender for endpoint, called security settings configuration. You now have a unified and centralized approach to managing security policies for various devices. You can efficiently handle Linux servers, Windows 10, Windows 11, and Mac OS devices without enrolling on Intune or Configuration Manager.
- With MDE, you could manage Defender policies for Windows servers, Linux servers, Windows 10 devices, Windows 11 devices, and Mac OS devices.
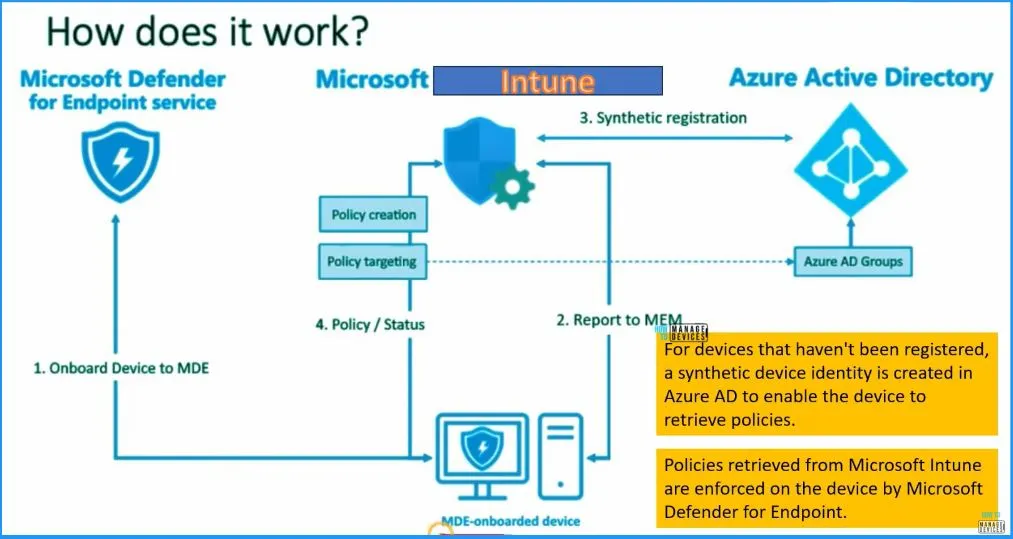
Latest MDE Architecture Flow and Schema Diagram – How Does it Work?
In this high-level architecture diagram shared by Microsoft. The onboarding process to Microsoft Defender for Endpoint (MDE) has become more straightforward and efficient. There are no complex requirements like hybrid AD join to bring devices into MDE.
Once a device is onboarded to MDE, it will seamlessly report to Microsoft Endpoint Manager (MEM). Previously known as Intune, MEM is the central hub for managing devices and their security settings. The device will undergo synthetic registration if not registered in Azure AD conventionally.
- For devices that have not been registered, a synthetic device identity is created in Azure AD to enable the device to retrieve policies.
- Microsoft Defender for Endpoint enforces policies retrieved from Microsoft Intune on the device.
Let’s check the MDE Enrollment flow in more detail with clarity. We will use the following latest MDE Architecture schema diagram to make it easy.
- Onboard Device to MDE
- Report to Microsoft Intune
- Synthetic Device Registration
- Send the policy status to Intune
Prerequisites for MDE Managed Devices
When a device is managed by Intune (enrolled to Intune), the device does not process policies for Defender for Endpoint security settings configuration. Instead, use Intune to deploy the policy for Defender for Endpoint to your devices.
- When a device receives a policy, the Defender Endpoint components enforce the policy and report on the device’s status.
- The device’s status is available in the Microsoft Intune admin center and the Microsoft 365 Defender portal.
| Supported Device Onboards to Microsoft Defender for Endpoint |
|---|
| The device is surveyed for an existing Microsoft Intune presence, and a mobile device management (MDM)enrollment to Intune. |
| Devices without an Intune presence enable the security settings management feature. |
| For devices that aren’t fully Azure AD registered, a synthetic device identity is created in Azure AD that allows the device to retrieve policies. Fully registered devices use their current registration. |
| Microsoft Defender for Endpoint enforces policies retrieved from Microsoft Intune on the device. |

MDE Only Enrollment – Additional Prerequisites
MDE Only enrollment is supported for Hybrid and Azure AD joined devices. But there are some additional prerequisites for the same. You can get more details about the forest trust requirements for this scenario from the below table.
When a domain-joined device creates trust with Azure Active Directory, this scenario is called a Hybrid Azure Active Directory join scenario. Security settings management fully supports this scenario with the following requirements.
- Azure Active Directory Connect (Azure AD Connect) must be synchronized to the tenant used from Microsoft Defender for Endpoint.
- Hybrid Azure Active Directory Join must be configured in your environment (either through Federation or Azure AD Connect Sync).
- Azure AD Connect Sync must include the device objects in scope for synchronization with Azure Active Directory (when needed for join).
- Azure AD Connect rules for sync must be modified for Server 2012 R2 (when support for Server 2012 R2 is needed).
- All devices must register in the Azure Active Directory of the tenant that hosts Microsoft Defender for Endpoint; cross-tenant scenarios aren’t supported.
MDE Onboarding
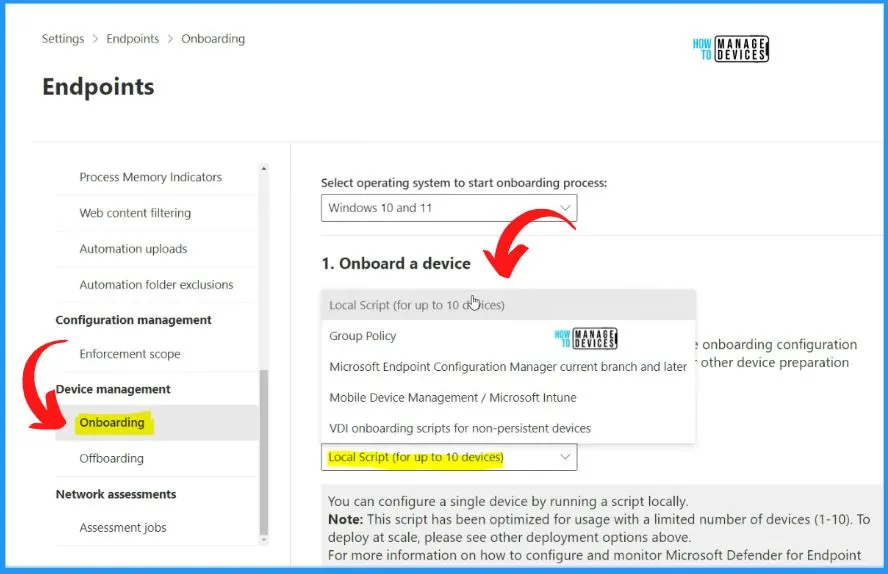
Let’s check how to Onboard the devices to MDE without using Intune. We have an article related to Intune onboarding. There are different devices to Onboard devices to MDE.
The local script is one of the options if you want to test it for a limited number of devices. The Onboarding deployment method is allowed only for 10 devices‘ local scripts. You can also use GPU if your device is domain joined.
- Open Microsoft 365 Defender portal – security.microsoft.com and sign in using your admin account.
- Settings > Endpoints >Onboarding
Microsoft Defender Endpoint Security Policies
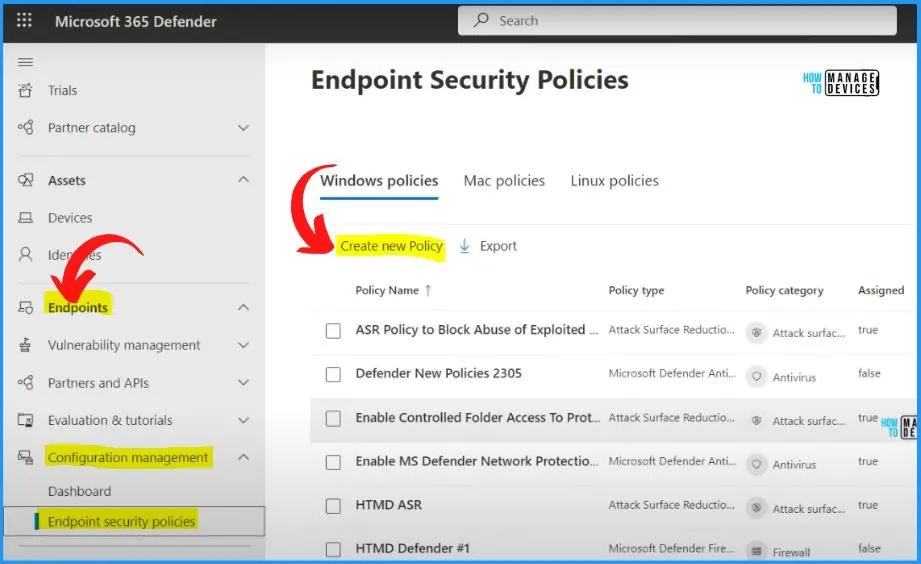
In the Microsoft Defender for Endpoint (MDE) portal, you can access the Endpoint security policies section to view and manage the policies created in Intune. This integration between MDE and Intune allows you to centralize your policy management for different operating systems, including Windows, Mac, and Linux devices.
- Log in to the Microsoft 365 Defender portal – security.microsoft.com
- Navigate to the “Endpoints” section in the left-hand menu.
- Click on “Endpoint security policies” under Endpoints -> Configuration Management.
- Here, you will see a list of all the policies created in Intune and available for various devices, such as Windows, Mac, and Linux.
MDE Security Settings
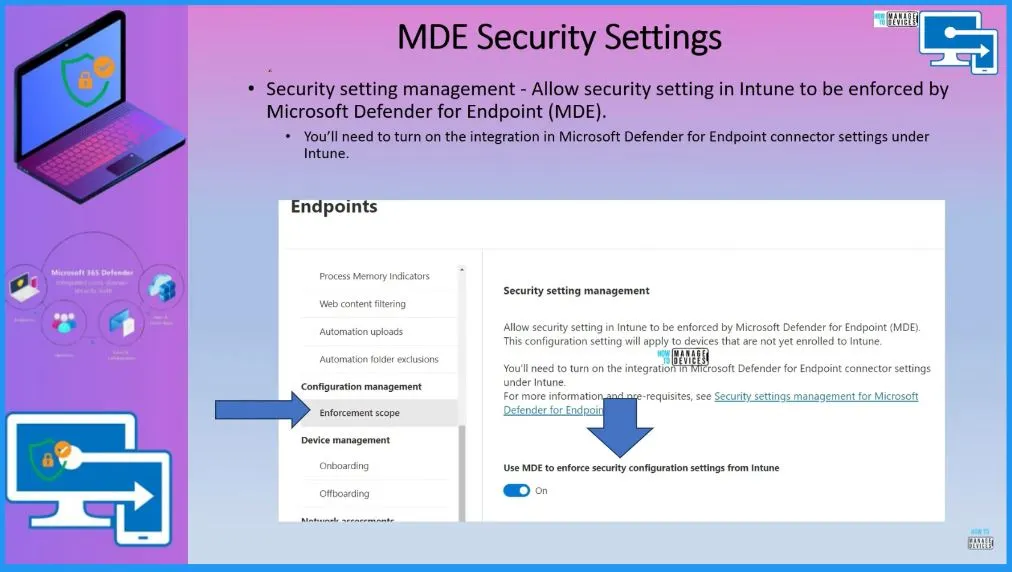
The security setting management allows security settings in Intune to be enforced by Microsoft Defender for Endpoint (MDE). This configuration setting will apply to devices not yet enrolled on Intune.
- Enable the option called Use MDE to enforce security configuration settins from Intune – Toggle the pane to the Right side.
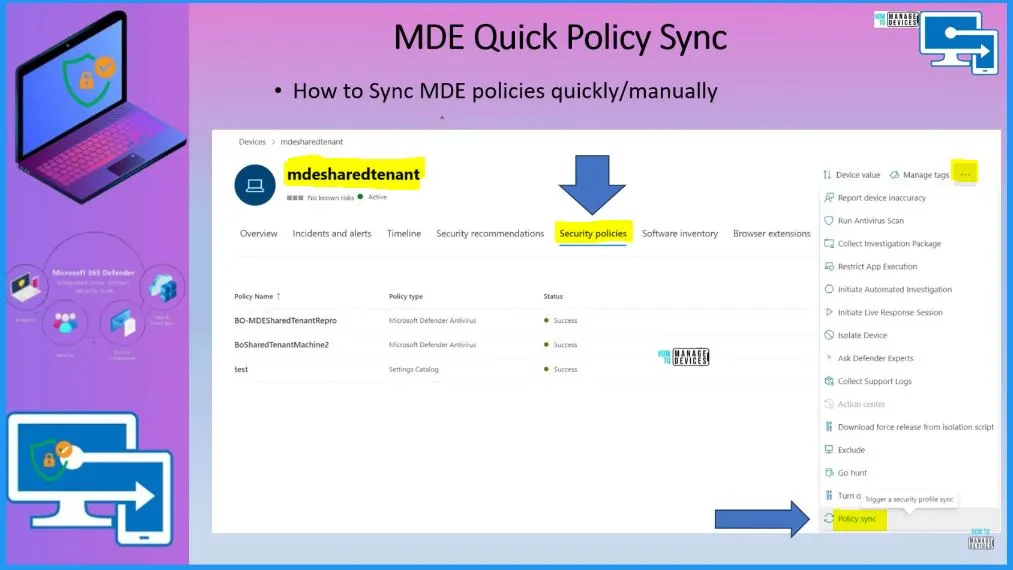
MDE Quick Policy Sync
You can manually or quickly sync the policies from the MDE portal. If you go to the device in the MDE portal, Go to security policies and click on the 3 dots on the Right top of the below window, there is a last option: policy sync default sync schedule is 90 minutes.
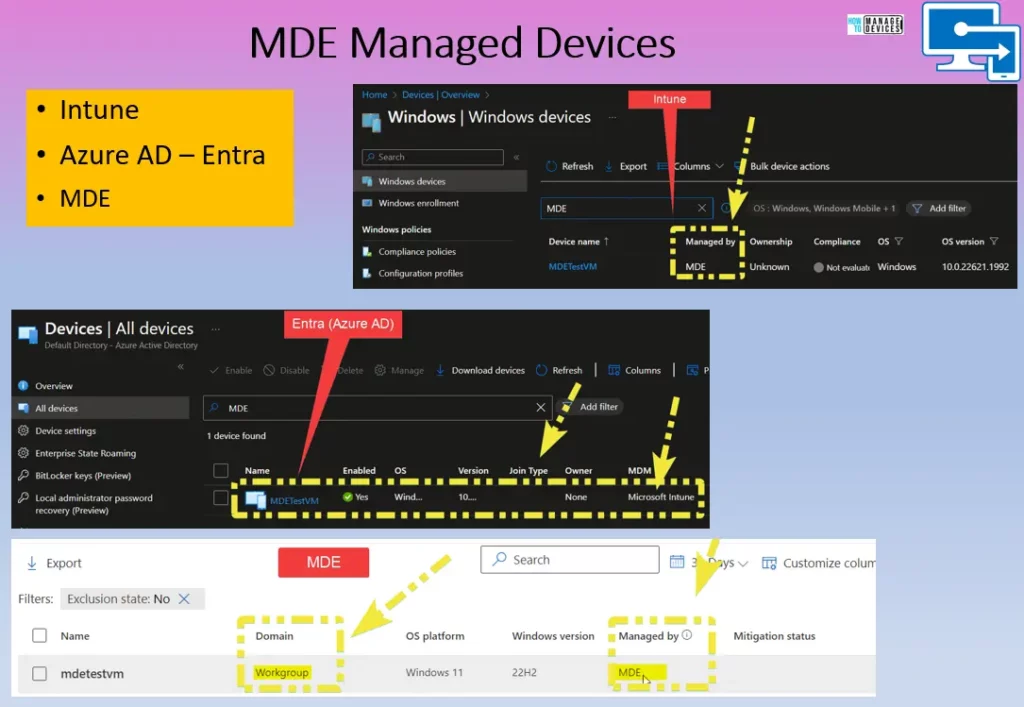
MDE Managed Devices
When Microsoft Defender manages a device for Endpoint (MDE) through the Intune portal, enforcing policies for these devices will happen exclusively through MDE and not Intune. In this scenario, Intune policies will not be applied or affect the devices managed by MDE.
On the other hand, if the devices were Intune-managed instead of MDE, policy enforcement would be done by Intune. Intune would handle the configuration and enforcement of policies for these devices.
You can refer to the following video for more details on MDE-only architecture, and Workgroup joined device onboarding scenarios.
Author
About Author – Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She loves writing on Windows 11 and related technologies. She is also keen to find solutions and write about day-to-day tech problems.

