What Is a Cloud Native Network Function (CNF)? Meaning, Architecture, and Examples
IT Toolbox
DECEMBER 5, 2022
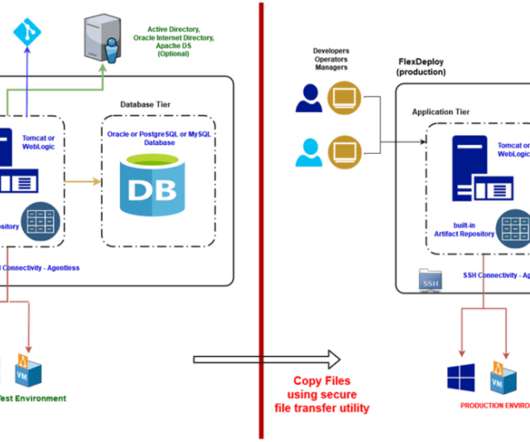
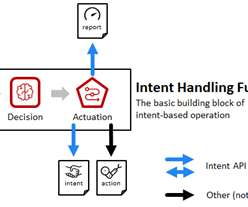
CNF is a software service that fulfills network functionalities while adhering to cloud-native design principles. The post What Is a Cloud Native Network Function (CNF)? Meaning, Architecture, and Examples appeared first on.












































Let's personalize your content