Consumers Crave Authenticity, And CMOs Can Deliver
Forrester IT
APRIL 5, 2022
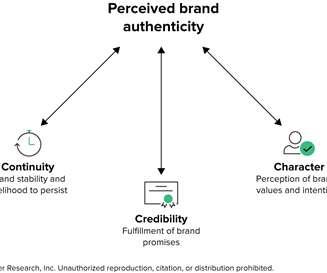
As the age of misinformation and slew of dubious corporate claims threaten consumers’ trust in brands, consumers are desperate for authenticity. While conventional wisdom suggests that authenticity means “being yourself,” that quickly breaks down when CMOs translate the sentiment into action.

















































Let's personalize your content