How to Prevent Phishing Attacks with Multi-Factor Authentication
Tech Republic Security
JANUARY 25, 2024
Learn how to protect yourself and your sensitive information from phishing attacks by implementing multi-factor authentication.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Tech Republic Security
JANUARY 25, 2024
Learn how to protect yourself and your sensitive information from phishing attacks by implementing multi-factor authentication.

Tech Republic Security
MARCH 17, 2022
The first line of defense against ransomware lies with email authentication. Learn more information about how to take a proactive approach to cyber attacks. The post Email authentication helps governments and private companies battle ransomware appeared first on TechRepublic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
JUNE 11, 2020
A password alone will not protect sensitive information from hackers--two-factor authentication is also necessary. Here's what security pros and users need to know about two-factor authentication.

Association of Information Technology Professional
MARCH 22, 2023
SSH is an essential tool for today's administrators and key-based authentication enables smoother integration of SSH into automation and orchestration tasks.

Advertisement
Think your customers will pay more for data visualizations in your application? Five years ago they may have. But today, dashboards and visualizations have become table stakes. Discover which features will differentiate your application and maximize the ROI of your embedded analytics. Brought to you by Logi Analytics.

HID Global
MARCH 27, 2024
Passwordless authentication is preventing hackers from accessing sensitive information. In this post, we’ll discuss how FIDO is powering this revolutionary charge.

SecureWorld News
FEBRUARY 15, 2024
A sophisticated form of mobile malware dubbed "GoldPickaxe" has been uncovered, which collects facial recognition data to produce deepfake videos, enabling hackers to bypass biometric authentication protections on banking apps. Experts warn that biometric authentication alone is not foolproof.

CTOvision
NOVEMBER 4, 2014
With the movement of our personal and business critical data to the ‘cloud’, and directed attacks on that data, many of us make use of stronger security through use two-factor authentication. Sam Srinivas, Product Management Director, Information Security, Google, is the organization’s vice president.

CIO Business Intelligence
OCTOBER 26, 2022
As financial services become more digital in nature, it’s important that banks think differently when using data analytics, security tools, and education to improve identity authentication and customer data privacy. Have you thought about what can be done with this device to enhance identity authentication?

SecureWorld News
MARCH 10, 2021
GitHub announced a security update due to a bug causing issues with the authentication of sessions. On March 2, GitHub received an external report of anomalous behavior for their authenticated GitHub.com user session. This would give them the valid and authenticated session cookie for another user. How did GitHub fix the issue?

The Accidental Successful CIO
JANUARY 23, 2019
Everybody needs two factor authentication, but just exactly what is it? As everyone in the CIO position knows, keeping the company’s systems and applications secure is a top priority and has a lot to do with the importance of information technology. Two Factor Authentication. So just exactly is two factor authentication.

Phil Windley
MARCH 7, 2022
Summary: Authenticity and privacy are usually traded off against each other. At a recent Utah SSI Meetup , Sam Smith discussed the tradeoff between privacy, authenticity and confidentiality. Authenticity allows parties to a conversation to know to whom they are talking. The following diagram illustrates these tradeoffs.

CIO Business Intelligence
JANUARY 31, 2023
Here, I’ll share a few tips to help you uncover your authentic leadership style. If you can answer these questions, you’ll be on your way to uncovering your authentic style. Having hard conversations helps us make informed decisions, solve tough problems, and understand others. What are your strengths and weaknesses?

CIO Business Intelligence
JUNE 27, 2022
Multi-factor authentication, or MFA. Multi-factor authentication requires users to provide two or more pieces of evidence in order to gain access to a network, application, or system, and can dramatically decrease the likelihood of infiltration. One of the best ways to ensure security? million to $4.24

Kitaboo
DECEMBER 18, 2023
Literacy is often regarded as a puzzle piece that is difficult to fit into the evolving jigsaws of information dissemination. As the channels of information spread grew multifold and information access was more digitalized, ‘ digital literacy ‘ became the norm. Conclusion What is Digital Literacy?

Phil Windley
MARCH 14, 2022
Summary: Provisional authenticity and confidentiality can help us manage the trade offs between privacy and authenticity to support online accountability along with functional privacy. Fortunately, the trade off is informed by a number of factors, making the outcome not nearly as bleak as it might appear at first.

SecureWorld News
SEPTEMBER 5, 2023
The exposed database, containing more than 17 billion records, has raised concerns about the security of sensitive healthcare provider information and negotiated rates for medical procedures. Fortunately, this database did not contain any customer or patient information. terabytes of data.

ForAllSecure
OCTOBER 6, 2022
For most APIs, the next step is setting up authentication. After all, without successfully authenticating, Mayhem for API can only test for very superficial problems! Giving the fuzzer a way to authenticate to the target API will enable it to exercise more endpoints and maximize coverage. Basic Authentication.
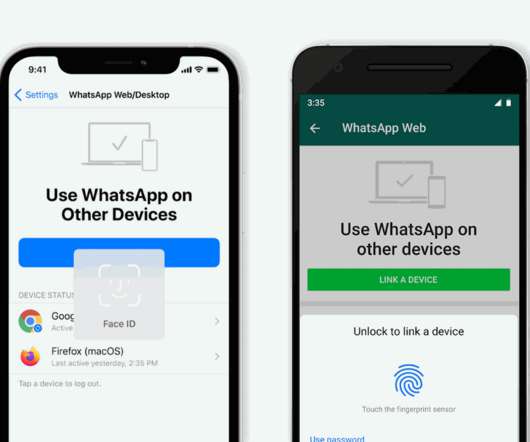
The Verge
JANUARY 28, 2021
Soon, if you’ve got biometric authentication enabled on your phone, you’ll have to unlock the app before you can link your account. The new system will be enabled by default on any iPhone devices running iOS 14 with either Touch ID or Face ID, and any Android devices that have biometric authentication enabled.

Dataconomy
NOVEMBER 21, 2023
The government of Canada has revealed the big “Canada data breach” that consists of information about government personnel, members of the Royal Canadian Mounted Police (RCMP), Canadian Armed Forces personnel, and more. Smelling something fishy in your accounts?

SecureWorld News
JULY 27, 2023
A new study from Uptycs has uncovered an increase in the distribution of information stealing malware. The 17-page report has a wealth of information, including the impact of stealers, the lifecycle of a stealer, the workflow of a stealer, and statistics around the stealers trending in 2023.

SecureWorld News
FEBRUARY 23, 2023
In a breach that's making headlines, hackers managed to steal data from the company, including sensitive employee information and upcoming game content. vx-underground also reported that a hacker managed to break into an Activision Slack channel, post offensive messages, and steal information related to upcoming "Call of Duty" releases.

The Verge
OCTOBER 5, 2021
In May, Google announced plans to enable two-factor authentication (or two-step verification as it’s referring to the setup) by default to enable more security for many accounts. In 2018, Google said that only 10 percent of its active accounts were using two-factor authentication. Illustration by Alex Castro / The Verge.

Forrester IT
OCTOBER 1, 2020
Biometric authentication is a powerful technology with many compelling use cases but is not without controversy and distinct risks. What are users’ privacy rights in how biometric information is processed and stored? How are biometrics regulated around the world? How can the use of biometrics lead to discriminatory practices?

Computer Weekly
JUNE 28, 2016
How can organisations move to biometric authentication of users without running the risk of exposing sensitive biometric information?

Association of Information Technology Professional
SEPTEMBER 24, 2021
2FA is widely used to improve an organization’s security. Learn why IT pros are expected to know how to explain and integrate it into IT environments.

Information Technology Zone Submitted Articles
OCTOBER 4, 2020
Pass-Through Authentication How to Synchronize your on-premise Active Directory with Azure Active Directory On-premise sync with AAD. Windows Active Directory sync with Azure AD

HID Global
JANUARY 31, 2023
RFID is a flexible secure and efficient wireless system used to exchange information effortlessly between devices and layers of protection and usability.

TechSpot
OCTOBER 1, 2021
It features two-factor authentication and now includes a "Masked Email" option. Available for the vast majority of operating systems, 1Password stores all your passwords and can be also used as a digital wallet. Though it is not free, you can try it for 14 days here.

Network World
JUNE 30, 2023
To reduce the risk of service problems, Cisco is making it harder for organizations to use weak cryptographic algorithms when setting up authentication for OSPF packets on certain Catalyst Edge Platforms and Integrated Services Routers (ISR). Newer versions of Cisco’s IOS XE software (Release 17.11.1

Galido
FEBRUARY 25, 2020
Information Technology Blog - - The Small Business Guide to Information Security - Information Technology Blog. Information security is a major issue in the business world, and security breaches cost businesses millions of dollars per year. But they can be particularly disastrous to small businesses. Salespeople.

Dataconomy
JULY 19, 2023
In a stunning turn of events, the popular online gaming platform Roblox faced a major data breach in July 2023, leading to the exposure of highly sensitive information from attendees of the 2017-2020 Roblox Developers Conferences. Here are all we know about the recent Roblox Data Leak so far.
The Verge
APRIL 9, 2021
A mobile carrier allowed anyone with one of its customers phone numbers to access their personal information, including name, address, phone number, and text and call history, according to a report by Ars Technica. A ton of information was available in the app, which didn’t ask for a password. Illustration by Alex Castro / The Verge.

The Verge
NOVEMBER 10, 2021
The heavily redacted screenshots show that hackers had access to buttons labeled “Disable MFA” (multi-factor authentication) and “Add to Trusted Device Email Code Whitelist,” along with information about what devices were logged into the account, and the ACH bank transfers the user had done.

SecureWorld News
APRIL 2, 2024
However, mounting evidence from cybersecurity researchers pointed to the data being authentic AT&T customer records. The compromised data includes names, addresses, phone numbers, and for many, highly sensitive information like Social Security numbers and dates of birth. "AT&T million former account holders."

CTOvision
APRIL 7, 2020
Read Adrian Moir take a look at how artificial intelligence impacts data protection strategies of businesses on Information Week : AI and machine learning are nothing new. From Siri, to self-driving cars, to biometric authentication, the development of AI and ML have been critical to enabling many technological advancements.

CTOvision
FEBRUARY 20, 2020
The breach, which was left open for more than 20 months, resulted in the theft of 30 million authentication tokens and almost as much personally identifiable information. Facebook recently pledged to improve its security following a lawsuit that resulted from a 2018 data breach.

Forrester IT
OCTOBER 16, 2019
Employees’ Advocacy Boosts Your Content And Customer Interactions While trust in brands has dwindled, B2B buyers hold those same brands’ employees in high regard as authentic and compelling sources of information. And they want to engage with them.

Future of CIO
JANUARY 21, 2019
Being authentic is the state of self-consciousness, self-discovery, and self-improvement. It seems everyone who considers authenticity has his or her own view of it. Does being authentic gives you the courage to be creative? Or actually, creativity makes your life seems more authentic, in pursuit of “Who you are.”
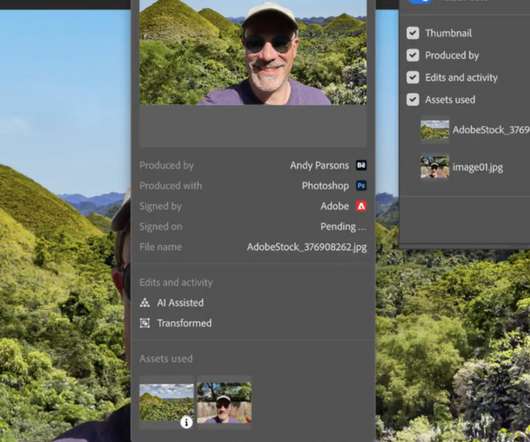
The Verge
OCTOBER 20, 2020
As part of a bigger software update, Adobe is moving forward with the Content Authenticity Initiative, a system it proposed last year. If the picture is uploaded to Behance, users can see all that information as a pop-up panel, or they can click through to a dedicated website.

Gizmodo
DECEMBER 28, 2021
Two-factor authentication, or 2FA, has been sold to web users as one of the most important and trustworthy tools for securing your digital life. You probably know how it works : By supplying an account with not just your password but also a secondary piece of information (typically an automated code texted to your… Read more.

Galido
JULY 26, 2018
Information Technology Blog - - Exciting Health Information Technology Breakthroughs - Information Technology Blog. Information Technology is helping doctors and patients to communicate better, automate, simplify and ultimately provide tools to share data and make it more understandable. More on Dr. VR.

Network World
AUGUST 2, 2016
With data breaches and information theft on the rise, it’s becoming even more crucial to protect your data from unwanted third parties. According to Symantec ’s annual Internet Security Threat Report , up to 80 percent of breaches could be eliminated with strong authentication.

Network World
SEPTEMBER 16, 2016
Insert another authentication step on top of these credentials and this gateway becomes harder to infiltrate. But once access is gained, how can the device or Web application be certain that the authenticated user is, in fact, the same person throughout the entire session? Usernames and passwords act as a gateway.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content