Report: 80% of fintech execs worry about authentication security tools
Venture Beast
NOVEMBER 14, 2021
Legacy IT authentication security tools, such as one-time passwords, possess vulnerabilities capable of being exploited. Read More.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Venture Beast
NOVEMBER 14, 2021
Legacy IT authentication security tools, such as one-time passwords, possess vulnerabilities capable of being exploited. Read More.

SecureWorld News
FEBRUARY 15, 2024
A sophisticated form of mobile malware dubbed "GoldPickaxe" has been uncovered, which collects facial recognition data to produce deepfake videos, enabling hackers to bypass biometric authentication protections on banking apps. Experts warn that biometric authentication alone is not foolproof.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Forrester IT
MAY 30, 2019
I have recently released a new report looking at the second phase of the Payment Services Directive (PSD2) and its security requirements along with my colleagues Jacob Morgan and Andras Cser. Banks and financial institutions are currently hard at work building APIs and testing their Strong Customer Authentication (SCA) solutions.

Forrester IT
APRIL 9, 2020
It is a humbling to work with a team of talented individuals like the ones I work with on Forrester’s Security & Risk team. This week, I’m highlighting 5 reports some of these fine folks published in Q1 that I got a lot of value out of, and I think you will too. Optimize […].

Advertisement
Think your customers will pay more for data visualizations in your application? Five years ago they may have. But today, dashboards and visualizations have become table stakes. Discover which features will differentiate your application and maximize the ROI of your embedded analytics. Brought to you by Logi Analytics.

CIO Business Intelligence
AUGUST 17, 2022
In my last column for CIO.com , I outlined some of the cybersecurity issues around user authentication for verification of consumer and business accounts. . Didn’t the FIDO Alliance just recently announce new UX guidelines to speed up MFA adoption with FIDO security keys?” Identity and access – the user authentication challenge .

CIO Business Intelligence
NOVEMBER 6, 2023
This makes it more critical than ever to adopt strong security measures to protect sensitive information and infrastructure. However, while cloud computing offers benefits like improved efficiency, scalability, and accessibility, it poses new security challenges.

SecureWorld News
MARCH 10, 2021
GitHub announced a security update due to a bug causing issues with the authentication of sessions. On March 2, GitHub received an external report of anomalous behavior for their authenticated GitHub.com user session. This would give them the valid and authenticated session cookie for another user.

CIO Business Intelligence
OCTOBER 26, 2022
Digitalization is a double-edged sword for banks, especially when it comes to security. As interactions and transactions become more interconnected, even the simplest processes like opening a new account or making a balance transfer become riddled with security concerns. Avaya’s research report reveals three critical ways to do so.

Network World
JULY 16, 2020
In a disconcerting event for IT security professionals, counterfeit versions of Cisco Catalyst 2960-X Series switches were discovered on an unnamed business network, and the fake gear was found to be designed to circumvent typical authentication procedures, according to a report from F-Secure.

Dataconomy
APRIL 2, 2024
The MRC 2023 Global E-commerce Payments and Fraud report revealed that almost half the merchants surveyed (46%) aimed primarily at reducing fraud and chargebacks. Meanwhile, strong security builds customer trust, which is essential for lasting relationships and business stability. The report states 34% of merchants faced this in 2023.

Dataconomy
MARCH 1, 2024
That’s the unsettling discovery made by Consumer Reports in their recent investigation into certain video doorbells. The report highlights serious flaws in video doorbells from brands like Eken, Tuck, Fishbot, and Rakeblue, all of which use the Aiwit app for control. The Christian Horner messages leak controversy What to do now?

CIO Business Intelligence
OCTOBER 25, 2023
On October 20, 2023, Okta Security identified adversarial activity that used a stolen credential to gain access to the company’s support case management system. Traditional security controls are bypassed in such attacks as bad actors assume a user’s identity and their malicious activity is indistinguishable from routine behavior.
CIO Business Intelligence
MAY 24, 2022
million fraud reports from consumers that totaled more than $5.8 Traditional IAM, however, was built to manage internal employees, which means that the organization has control over connecting users to their real identities, birthright provisioning and device security. In 2021, the Federal Trade Commission [1] received 2.8

Venture Beast
OCTOBER 31, 2021
Consumers are concerned about their online security, and many have taken action by moving to biometrics and using authentication software. Read More.

CIO Business Intelligence
JUNE 27, 2022
One of the best ways to ensure security? Multi-factor authentication, or MFA. Multi-factor authentication requires users to provide two or more pieces of evidence in order to gain access to a network, application, or system, and can dramatically decrease the likelihood of infiltration. IT Leadership, Security

CIO Business Intelligence
NOVEMBER 14, 2023
billion devices reported in 2023. It also introduces new security challenges that demand our attention, especially as IoT is integrated into operational technology (OT) environments. 6 IoT vulnerabilities to watch out for Security risks are a significant concern for businesses using LoT and OT technology.

SecureWorld News
JANUARY 17, 2024
That troubling dynamic motivates a comprehensive new report on AI security published by the U.S. The report maps out a detailed taxonomy of current adversarial threats to AI systems across different modalities such as computer vision, natural language processing, speech recognition, and tabular data analytics.
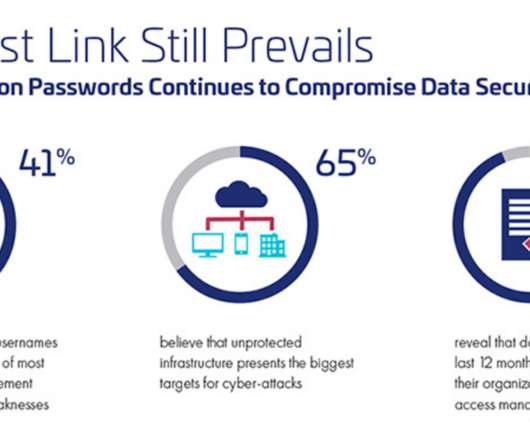
Tech Republic Security
JUNE 18, 2020
IT leaders remain under pressure to balance security and authentication methods, yet this remains a challenge for most organizations, according to a new report by Thales.

CIO Business Intelligence
JANUARY 22, 2024
The remote work revolution has pushed companies to rethink their security and data protection practices amidst hybrid work and cloud environments. trillion by 2025, as cyber risk management has not kept up with digital transformation posing serious risks to organizations’ security and revenue.

SecureWorld News
DECEMBER 18, 2023
This morning, the Qualys Threat Research Unit released its 2023 Threat Landscape Year in Review report. According to the report: "Of the 206 high-risk vulnerabilities we tracked, more than 50 percent of those were either leveraged by threat actors, ransomware, or malware to compromise systems. 115 exploited by named threat actors.

Computerworld Vertical IT
MARCH 22, 2021
Everyone has been lecturing IT about how horrible the security is from texting numbers for authentication for years, including me. Now, due to some excellent reporting from Vice , it's clear that the text situation is far worse than almost anyone thought.

The Verge
OCTOBER 7, 2020
Tesla accounts can now be secured with two-factor authentication (2FA), giving owners an extra layer of security around their cars’ connected services, Electrek reports. A support page on Tesla’s website outlining how to set up the feature says any third-party authenticator apps can be used to provide the passcodes.

Linux Academy
APRIL 8, 2019
I am a huge fan of password managers because they make my life more secure and easier. They were stored securely online, and we could access them from anywhere. I can access any password from my phone or computer via a secure connection. Multi-factor authentication (MFA). Where to use MFA.

SecureWorld News
FEBRUARY 17, 2024
A 2021 Cynerio report revealed a staggering 123% increase in ransomware attacks on healthcare facilities, resulting in more than 500 incidents and costs exceeding $21 billion. New security solutions are now aiding healthcare organizations' IT teams in promptly resolving issues, even with devices from various manufacturers.

The Verge
DECEMBER 28, 2021
This time around, attackers accessed “a small number of” customers’ accounts, according to documents posted by The T-Mo Report. According to the report, customers either fell victim to a SIM swapping attack (which could allow someone to bypass SMS-powered two-factor authentication), had personal plan information exposed, or both.

CIO Business Intelligence
DECEMBER 19, 2023
When making decisions about network access, businesses need to be aware of and assess the security implications associated with network technology to help keep their digital assets protected. Cyber hygiene best practices include device security , cyber security education , and secure networking strategies.

The Verge
DECEMBER 13, 2020
The same Russian government hacking group responsible for a security breach at FireEye compromised the Treasury and Commerce departments and other US government agencies, The Washington Post reported. Illustration by Alex Castro / The Verge.

Kitaboo
MARCH 26, 2024
It is a security system that can protect your hard work from being stolen. It provides publishers and authors with a secure and efficient way to distribute and monetize their content while protecting it from piracy and misuse. Analytics and reporting tools to track eBook sales and user engagement.

The Verge
AUGUST 15, 2021
Motherboard reported that it was in contact with the seller of the data, who said they had taken data from T-Mobile’s servers that included Social Security numbers, names, addresses, and driver license information related to more than 100 million people. After reviewing samples of the data, Motherboard reported it appeared authentic.

The Verge
OCTOBER 6, 2021
While The Verge is unable to immediately verify the contents of the leak, Video Games Chronicle reports that it’s legit. Twitch’s internal security tools. Video Games Chronicle reports that the data may have been obtained as early as this week and that Twitch is aware of the breach.

The Verge
JUNE 5, 2021
An analysis of the cyberattack on Colonial Pipeline found that the hackers were able to access the company’s network using a compromised VPN password, Bloomberg reported. The password was discovered among a batch of passwords leaked on the dark web, Bloomberg reported. The hack led to a ransomware payout of $4.4

SecureWorld News
OCTOBER 22, 2023
Cyber challenges facing businesses expanding overseas Companies expanding into overseas markets face amplified cyber security challenges. Benefits of safeguarding global assets Properly securing critical assets and data against cyber threats when operating overseas provides major benefits.

SecureWorld News
OCTOBER 2, 2023
As we embark on the 20th anniversary of Cybersecurity Awareness Month this October, SecureWorld proudly steps forward to champion the 2023 theme, "Secure Our World." Cybersecurity and Infrastructure Security Agency (CISA) produced its first public service announcement (PSA) that that will air on stations around the country.

CIO Business Intelligence
OCTOBER 16, 2023
But casino gaming companies MGM Resorts International and Caesars Entertainment were caught short in this area in recent weeks by hackers using identity-based and social engineering attacks that spoofed identity to gain access to secure systems. According to reports, MGM and Caesars were both customers of identity management company Okta.

SecureWorld News
FEBRUARY 20, 2023
Web hosting provider GoDaddy has revealed it suffered a security breach that lasted for several years, resulting in the installation of malware on its servers and the theft of source code related to some of its services. A 10-K report filed by GoDaddy with the U.S.

CIO Business Intelligence
JANUARY 9, 2024
Achieving and sustaining compliance with the Payment Card Industry Data Security Standard (PCI DSS) is a daunting challenge for hotels because they handle many complex payment business cases. See the PCI Security Standards Council (SSC) Requirements and Testing Procedures , Version 4.0 Four recommended steps in the PCI DSS v4.0

SecureWorld News
APRIL 2, 2024
However, mounting evidence from cybersecurity researchers pointed to the data being authentic AT&T customer records. The compromised data includes names, addresses, phone numbers, and for many, highly sensitive information like Social Security numbers and dates of birth. "AT&T million former account holders."

Tech Republic Security
OCTOBER 8, 2019
Users still have to juggle far too many passwords, which leads to password sharing, reuse, and other bad habits, according to a new report from password manager LastPass.

Venture Beast
MARCH 25, 2022
Consumers are so frustrated that many would rather shovel snow, sit in traffic or deal with a flight delay than reset their passwords. Read More.

SecureWorld News
OCTOBER 28, 2022
LinkedIn has announced a new set of security features that will help verify user identity, remove fraudulent accounts, and boost authenticity, according to an official blog post from the company. These warnings will also give you the choice to report the content without letting the sender know.".
Venture Beast
FEBRUARY 3, 2022
Microsoft disclosed in a new report that just 22% of Azure Active Directory accounts are using MFA for authentication. Read More.

SecureWorld News
OCTOBER 26, 2023
A new report from the Identity Theft Resource Center (ITRC) reveals cyberattacks and data breaches targeted at small and medium-sized businesses (SMBs) continue to climb, reaching their highest levels in the three years of the study. If self-reported, it may not be accurate. But for now, the adoption of protections remains low.

SecureWorld News
AUGUST 29, 2023
Kroll, a leading provider of risk management and financial consulting services, finds itself in the midst of dealing with the consequences of a recent and alarming security breach. Following the breach, reports emerged of phishing attempts targeting individuals associated with the affected crypto companies.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content