The number of devices infected with data-stealing malware in 2023 was 9.8 million, a sevenfold increase over the same figure for 2020, according to new research from Kaspersky Digital Footprint Intelligence. However, the researchers believe that the true figure could be as high as 16 million, as credentials from devices infected in 2023 may not be leaked onto the dark web until later this year.
Cybercriminals stole an average of 50.9 credentials per compromised device, and 443,000 websites have had user information leaked in the past five years.
The data was obtained from log files that record the activities of “infostealers.” Infostealers are a type of malware that covertly extracts data from infected devices without encrypting it. These logfiles are “actively traded in underground markets” and monitored by Kaspersky as part of its digital risk protection service.
Sergey Shcherbel, expert at Kaspersky Digital Footprint Intelligence, said in a press release, “Leaked credentials carry a major threat, enabling cybercriminals to execute various attacks such as unauthorized access for theft, social engineering or impersonation.”
Why is the number of data-stealing malware cases growing?
Infostealers are more accessible
According to a report by IBM, there was a 266% increase in infostealing malware in 2023 over the previous year. It appears to be effective, too, as incidences of criminals gaining access by using valid login credentials went up by 71%.
The popularity of infostealers is widely regarded to be linked to the increasing value of corporate data and the malware’s growing accessibility. In separate research, Kaspersky Digital Footprint Intelligence found that 24% of malware sold as a service between 2015 and 2022 was infostealers, which allow amateur cybercriminals to utilize infostealers developed by another group and distributed via the dark web.
Luke Stevenson, cyber security product manager at managed service provider Redcentric, told TechRepublic in an email, “Stealer malware significantly lowers the entry barrier to would-be cyber criminals, making data breaches easier. Exfiltrated data has immediate value irrespective of the direct victim’s financial resources and can be sold on quickly across the range of illicit criminal forums.
“The malware is relatively easy to compile and deploy with source codes accessible for those starting out. Unlike ransomware which has its own business ecosystem, those operating infostealers generally have much lower overhead costs.”
Aamil Karimi, threat intelligence leader at cybersecurity firm Optiv, told TechRepublic in an email, “There was a notable rise in new stealer malware introduced to the cybercriminal ecosystem beginning in 2019, including very popular strains like RedLine, Lumma and Raccoon. Some of these stealer malware variants have been used in ransomware operations that have shown increased activity over the last few years. These variants are very inexpensive, and they have proven to work, so there is incentive for more potential criminals to join these malware-as-a-service operations and affiliate programs.”
Furthermore, the proliferation of “dedicated leak sites,” where stolen credentials are posted, provides more targets for infostealers. The more sites of this nature are active — and the number grew by 83%, according to Group-IB’s Hi-Tech Crime Trends 2022/2023 report — the higher the risk that companies will have their devices compromised. Research from Group-IB revealed the number of companies that had their data uploaded to leak sites in 2023 increased by 74% over the previous year.
Supply chains are becoming more complex and vulnerable
Another reason that data-stealing malware cases are growing is due to the supply chain. Third-party vendors are often given access to internal data or use linked systems and may provide an easier entry point that leads to confidential data belonging to the target organization.
Dr. Stuart Madnick, an IT professor and cybersecurity researcher at the Massachusetts Institute of Technology, wrote in the Harvard Business Review, “Most companies have increased the cyber protection of their ‘front doors’ through measures such as firewalls, stronger passwords, multi-factor identification, and such. So, attackers seek other — and sometimes more dangerous — ways to get it. Often, that means coming in via vendors’ systems.
“Most companies rely on vendors to assist them, from doing air conditioning maintenance to providing software, including automatic updates to that software. In order to provide those services, these vendors need easy access to your company’s systems — I refer to these as the ‘side doors.’ But, these vendors are frequently small companies with limited cybersecurity resources.
“Attackers exploit vulnerabilities in these vendor systems. Once they have some control over these vendor systems, they can use the side door to get into the systems of their customers.”
Research from the Bank for International Settlements suggests that global supply chains are becoming longer and more complex, which increases the number of potential entry points for attackers. A report from the Identity Theft Resource Center found that the number of organizations impacted by supply chain attacks surged by more than 2,600 percentage points between 2018 and 2023.
Malware types are increasing in number
The amount of malware available to cybercriminals is increasing exponentially, according to Optiv’s senior malware analyst McKade Ivancic, facilitating more data-stealing attacks. He told TechRepublic in an email, “The more that stealer-family malware is authored, the more those families’ code bases will be pilfered and re-written into similar, yet slightly different, data-stealers.”
He added, “Security teams, products, signatures and the like cannot grow exponentially like malware can. Until a more permanent solution is found, the ‘good guys’ will be naturally outpaced due to sheer numbers, compound growth, ease of access, lack of enforcement and attack surface expansion via growing technology and software investments.”
WFH and BYOD models are more commonplace
Karimi told TechRepublic, “The increase in the work-from-home and bring-your-own-device models since 2020 also likely contributed to increased risk to companies whose employees’ devices were not centrally or responsibly managed.”
Personal devices tend to lack the same security measures as company-provided devices, creating a larger attack surface for criminals looking to deploy data-stealing malware. Microsoft’s Digital Defense Report 2023 stated that up to 90% of ransomware attacks in 2023 originated from unmanaged or bring-your-own devices.
What type of credentials do cybercriminals target?
The credentials often targeted by attackers using data-stealing malware are those that could lead to valuable data, money or privileged access. Such details may include corporate logins for emails or internal systems, as well as social media, online banking or cryptocurrency wallets, according to the Kaspersky research.
SEE: Kaspersky’s Advanced Persistent Threats Predictions for 2024
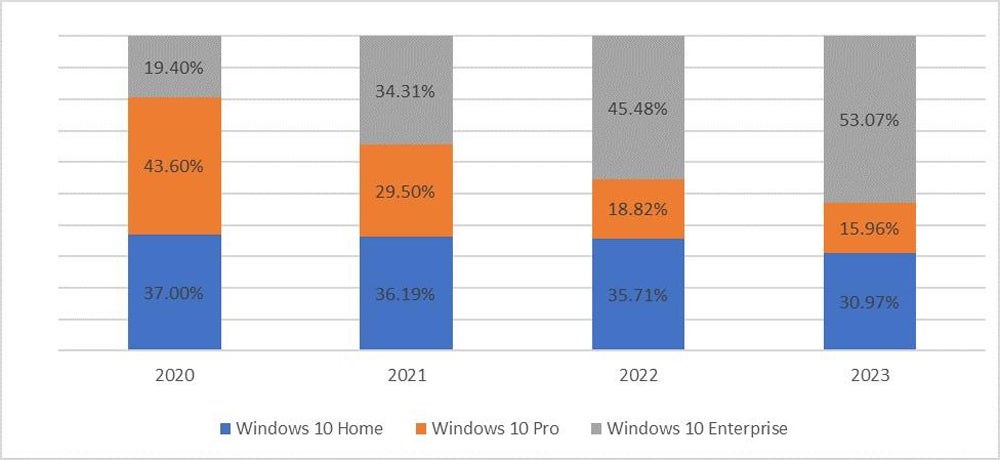
Another study by the firm found that over half (53%) of devices infected with data-stealing malware in 2023 were corporate. This conclusion was drawn from the fact that the majority of infected devices with Windows 10 software are specifically running Windows 10 Enterprise (Figure A).
How much data can be extracted with data-stealing malware?
Each log file analyzed by Kaspersky Digital Footprint Intelligence in this study contained account credentials for an average of 1.85 corporate web applications, including emails, internal portals and customer data processing systems. This means that criminals are often able to access multiple accounts, both business and personal, after infecting a single device.
The log file data also revealed that a fifth of employees would reopen the malware on their device more than once, giving the cybercriminals access to their data on multiple occasions without the need for reinfection.
Shcherbel said in the press release, “This may indicate several underlying issues, including insufficient employee awareness, ineffective incident detection and response measures, a belief that changing the password is sufficient if the account has been compromised and a reluctance to investigate the incident.”
What do cybercriminals do with the stolen data?
According to Kaspersky Digital Footprint Intelligence, threat actors will use the credentials stolen from malware-infected devices for a number of purposes. These include:
- Perpetrating cyberattacks on other parties.
- Selling them to others on the dark web or shadow Telegram channels.
- Leaking them for free to sabotage an organization or better their own reputation.
Shcherbel said in the press release, “The dark-web value of log files with login credentials varies depending on the data’s appeal and the way it’s sold there.
“Credentials may be sold through a subscription service with regular uploads, a so-called ‘aggregator’ for specific requests, or via a ‘shop’ selling recently acquired login credentials exclusively to selected buyers. Prices typically begin at $10 per log file in these shops.
“This highlights how crucial it is both for individuals and companies – especially those handling large online user communities – to stay alert.”
How can businesses protect themselves from data-stealing malware?
To guard against data-stealing malware, researchers at Kaspersky Digital Footprint Intelligence recommended the following:
- Monitor dark web markets for compromised accounts associated with the company.
- Change the passwords of compromised accounts and monitor them for suspicious activity.
- Advise potentially infected employees to run antivirus software on all devices and remove any malware.
- Install security solutions on company devices that alert users to dangers like suspicious sites or phishing emails.
TechRepublic consulted other experts for additional advice.
Encryption and access controls
Matthew Corwin, managing director at cybersecurity firm Guidepost Solutions, told TechRepublic in an email: “Encryption of data both at rest and in transit is critical for preventing data-stealing and exposure attacks, but for this to be effective a comprehensive defense-in-depth security architecture around the encrypted assets is also required.”
Stevenson added that “securing accounts via password managers and multi-factor authentication” is an important basic step for protecting account credentials from unauthorized use.
SEE: 6 Best Open-Source Password Managers for Windows in 2024
Risk assessments
Corwin told TechRepublic, “Periodic security and risk assessments can help identify specific weaknesses in an organization’s security posture which could be exploited by threat actors using data-stealing malware.”
Education
Karimi told TechRepublic, “Developing a more proactive approach to risk management requires education and awareness — both for the IT team and security administrators, as well as users in general.
“Security awareness is often touted as a default recommendation, but risk awareness is not. It is more comprehensive than a single online security awareness training module… It is important to establish processes to identify and track the most relevant threats that are unique to your environment.”
He added that “drafting, updating and enforcing business use cases and user policies for web activity” can provide additional security assurance by ensuring all staff are handling their credentials safely.


