The State Of Data Security, 2023
Forrester IT
AUGUST 28, 2023
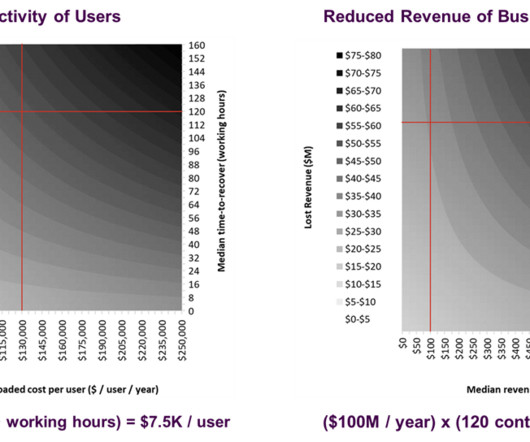
Data is everywhere. What constitutes sensitive data for organizations today has greatly expanded in type and format. In my latest report, The State Of Data Security, 2023, we reviewed and analyzed Forrester survey data to identify the key data security trends of the year.




















































Let's personalize your content