7 Ways a System Administrator Directly Impacts Your Business
IT Toolbox
JULY 26, 2023
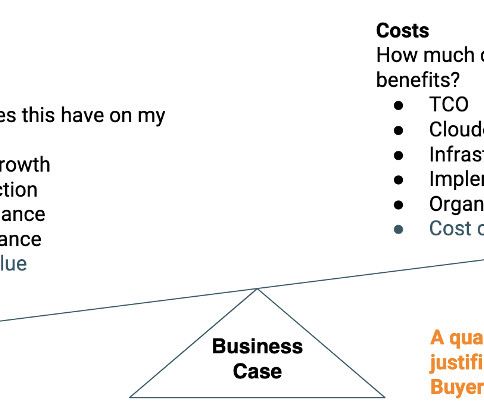
Good system administrators can handle data security, disaster recovery, communications, scalability, vendor relations, and more. The post 7 Ways a System Administrator Directly Impacts Your Business appeared first on Spiceworks.


















































Let's personalize your content