Let’s check the new experience of deploying BitLocker Disk Encryption policy using Intune. Microsoft released a new experience creating new BitLocker profiles for endpoint security Disk Encryption policy. The experience for editing your previously created BitLocker policy remains the same, and you can continue to use them.
BitLocker is a built-in Windows data protection feature available on devices that run Windows 10/11, capable of encrypting entire hard drives, including both system and data drives. BitLocker pre-provisioning can drastically reduce the time required to provision new PCs with BitLocker enabled.
This update is part of the continuing rollout of new profiles for endpoint security policies, which began in April 2022. This update applies only to the new BitLocker policies you create for the Windows 10 and later platform.
Some settings for BitLocker require the device to have a supported TPM. It is important to understand that BitLocker has specific hardware requirements and that some methods of enabling BitLocker are dependent on those conditions.
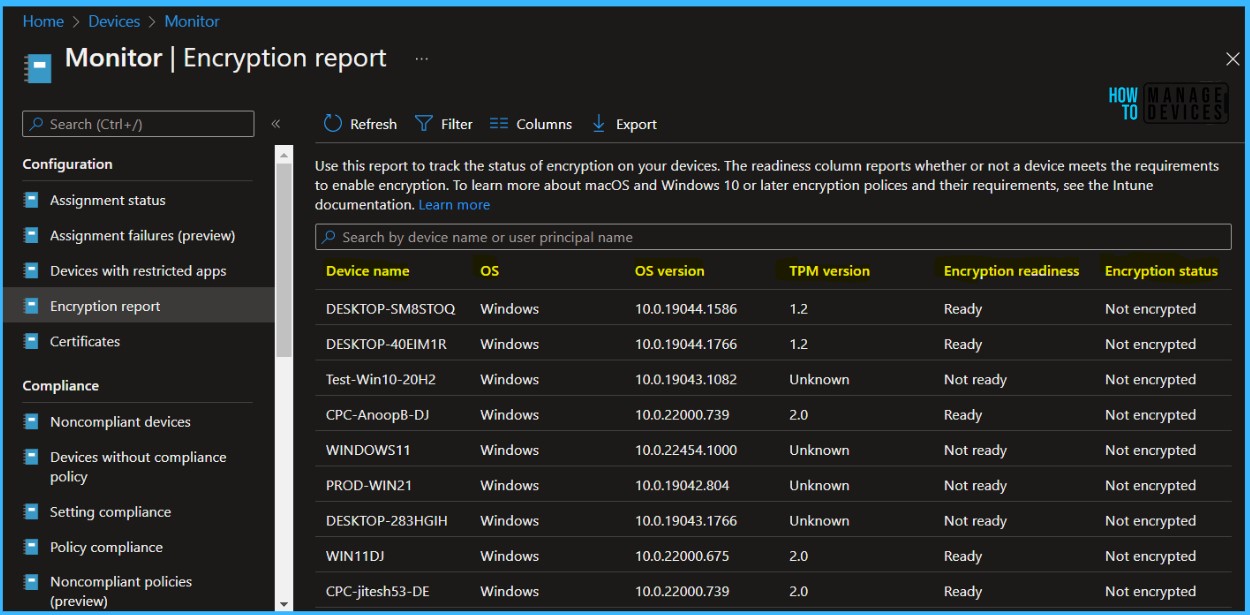
You can view the encryption status of all managed devices in the Encryption report (Devices – Monitor – Encryption Report). This includes status of encryption on the device, encryption readiness and any prerequisites missing or errors related to encryption on devices.
- Intune Bitlocker Drive Encryption A Deeper Dive To Explore
- Managing Windows Bitlocker Compliance Policy Using Intune | MS Graph | Grace Period
Deploy BitLocker Disk Encryption Policy using Intune
BitLocker Drive Encryption is a data protection feature that integrates with the operating system and addresses the threats of data theft or exposure from lost, stolen, or inappropriately decommissioned computers. The steps help you to configure settings for BitLocker Encryption for Windows 10 or 11 devices using Intune.
- Sign in to Microsoft Intune Admin Center https://intune.microsoft.com
- Navigate to the Endpoint Security node. Select Endpoint security > Disk encryption.
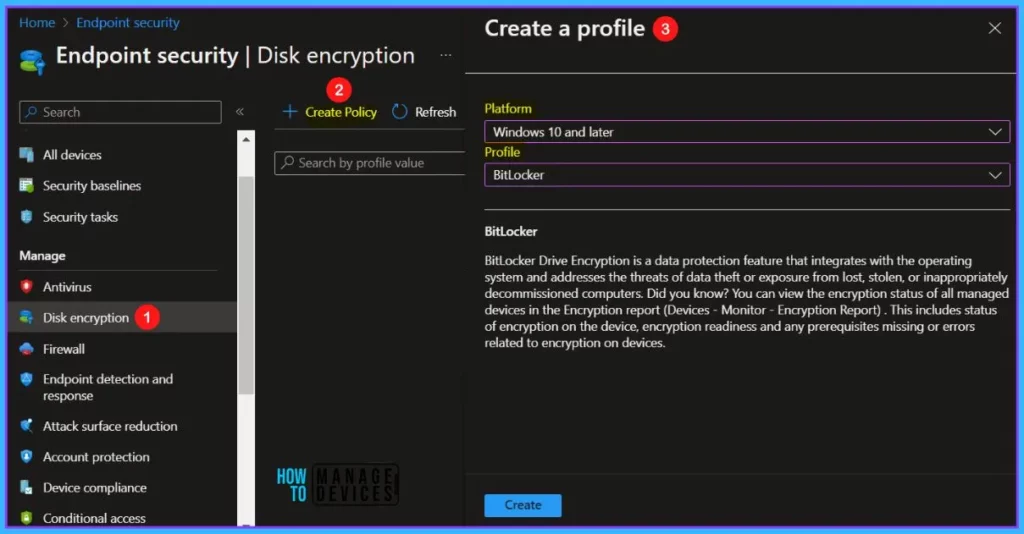
Click on + Creare Policy. In Create Profile, Select Platform, Windows 10, and later and Profile, Select Profile Type as Bitlocker. Click on Create button.
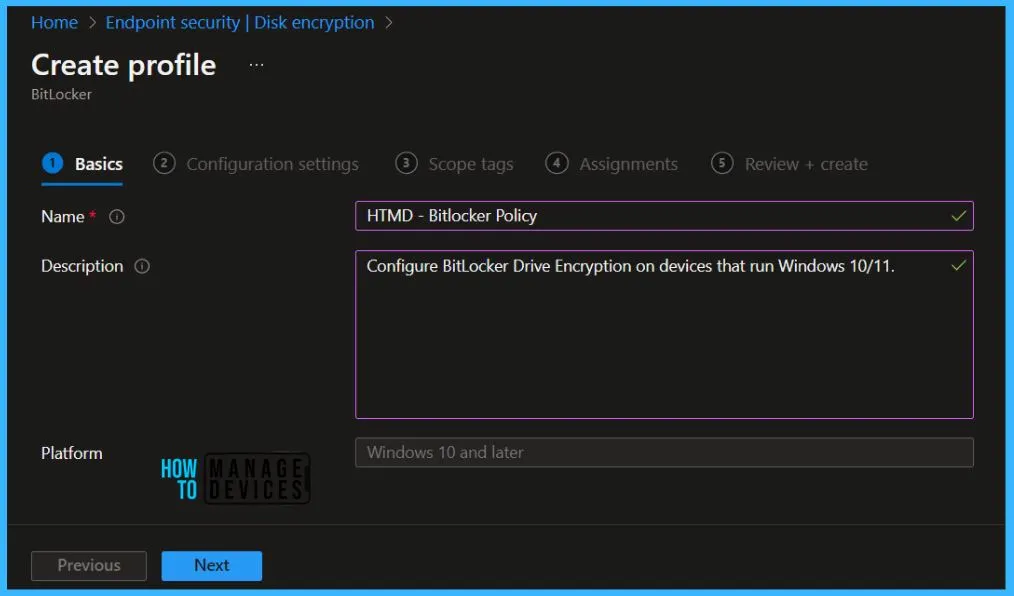
On the Basics tab, enter a descriptive name, such as HTMD – Bitlocker Policy. Optionally, enter a Description for the policy, then select Next.
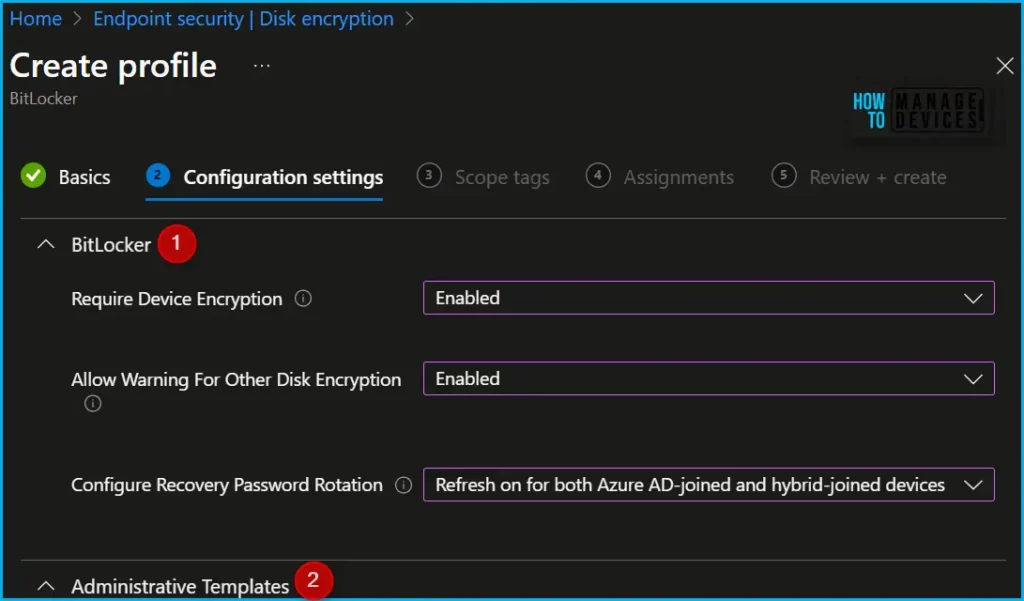
In Configuration settings, Scroll down and configure the policy you want to configure for your environment. Depending on the type of policy that you use to enable BitLocker silently, configure the following settings.
Here you will find the two tabs, Bitlocker and Administrative Templates, for Bitlocker policy configuration. Expand the settings to Configure the following settings in the BitLocker profile:
| Bitlocker Policy | Settings | Descriptions |
|---|---|---|
| Require Device Encyption | Enabled | Allows the Admin to require encryption to be turned on using BitLocker\Device Encryption. Disabling the policy will not turn off the encryption on the system drive. But will stop prompting the user to turn it on. |
| Allow Warning For Other Disk Encryption | Enabled | Allows Admin to disable all UI (notification for encryption and warning prompt for other disk encryption) and turn on encryption on the user machines silently. Warning: When you enable BitLocker on a device with third party encryption, it may render the device unusable and will require reinstallation of Windows. |
| Configure Recovery Password Rotation | Enable rotation on Azure AD-joined devices or Enable rotation on Azure AD and Hybrid-joined devices | Allows Admin to configure Numeric Recovery Password Rotation upon use for OS and fixed drives on AAD and Hybrid domain joined devices. When not configured, Rotation is turned on by default for AAD only and off on Hybrid. The Policy will be effective only when Active Directory back up for recovery password is configured to required. For OS drive: Turn on “Do not enable Bitlocker until recovery information is stored to AD DS for operating system drives” For Fixed drives: Turn on “Do not enable Bitlocker until recovery information is stored to AD DS for fixed data drives” |
Note – This is the most recent method of deploying BitLocker settings. If you are currently using a device configuration profile, consider migrating to an Endpoint security policy.
The Administrative Templates for Bitlocker policy has categorised into four sectors, including OS Drives, Fixed Data Drivers and Removal Data Drives.
- Windows Components > BitLocker Drive Encryption
- Windows Components > BitLocker Drive Encryption > Operating System Drives
- Windows Components > BitLocker Drive Encryption > Fixed Data Drives
- Windows Components > BitLocker Drive Encryption > Removable Data Drives
For OS volumes and fixed drives: XTS-AES 128-bit is the Windows default encryption method and the recommended value. An IT Admin can set this algorithm to AES-CBC 128-bit, AES-CBC 256-bit, XTS-AES 128-bit, or XTS-AES 256-bit encryption.
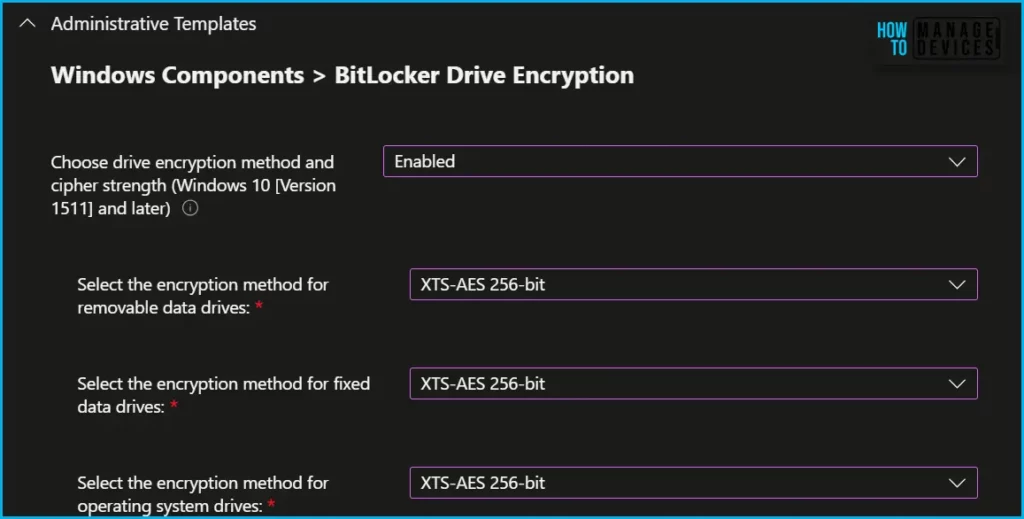
Windows Components > BitLocker Drive Encryption > Operating System Drives – In the BitLocker profile you’ll find the following settings in the BitLocker – OS Drive Settings category when BitLocker system drive policy is set to Configure, and then Startup authentication required is set to Yes.
The Compatible TPM startup PIN, Compatible TPM startup key and Compatible TPM startup key and PIN options are set to Blocked. BitLocker cannot silently encrypt the device if these settings are configured to be required because these settings require user interaction.
- Compatible TPM startup
- Compatible TPM startup PIN –
- Compatible TPM startup key
- Compatible TPM startup key and PIN
- Disable BitLocker on devices where TPM is incompatible
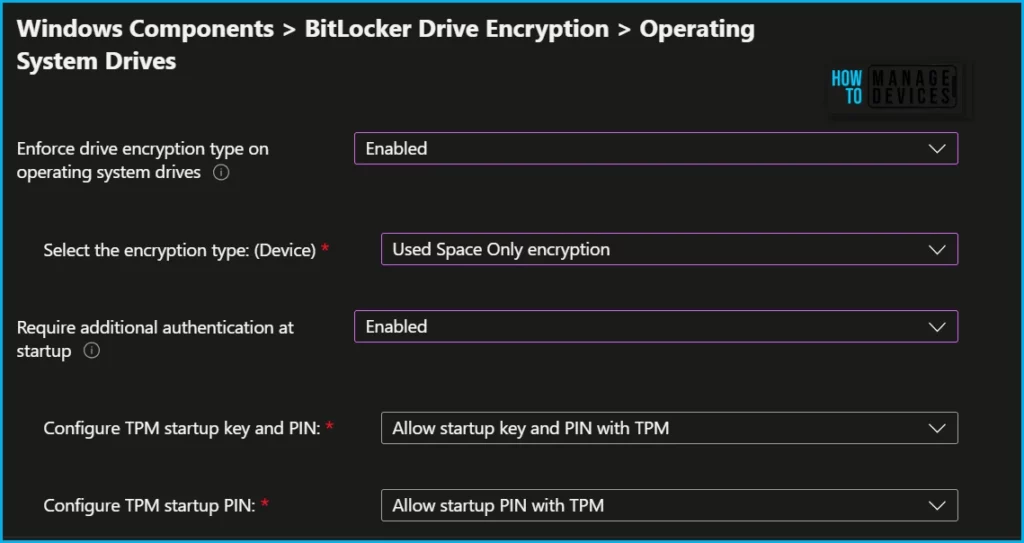
Here In Windows Components > BitLocker Drive Encryption > Fixed Data Drives, you can control how BitLocker-protected Fixed drives.
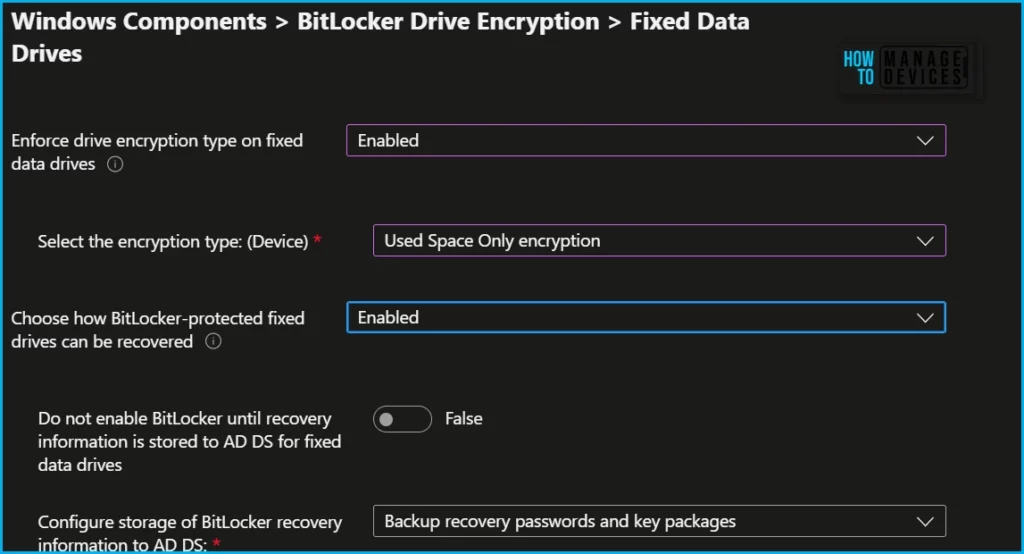
Here you can configure the Control use of BitLocker on removable drives group policy setting that controls the use of BitLocker on removable data drives. Removable drive settings apply to storage devices such as USB flash storage devices and external hard drives.
Note – You can also set do not configure Removable Drive settings with the new Bitlocker policy.
- Control use of BitLocker on removable drives
- Deny write access to removable drivers not protected by BitLocker
Scope tags are filtering options provided in Intune to ease the admin jobs. In Scope tags, you can assign a tag to filter the profile to specific IT groups. Add scope tags (if required) and click Next.
Under Assignments, In Included groups, click Add groups and then choose Select groups to include one or more groups. Click Next to continue.
In Review + create, review your settings. When you select Create, your changes are saved, and the profile is assigned for deploying BitLocker using Intune.
A notification will appear automatically in the top right-hand corner with a message. You can see the message “Profile HTMD- Bitlocker Policy created successfully”. Once you create the profile, it’s pushed to the assigned group.
Monitor Bitlocker Disk Encryption Status
Intune provides a built-in encryption report that presents details about the encryption status of devices, across all your managed devices. The encryption report shows common details across the supported devices you manage, Intune Device Encryption Status Report for deploying BitLocker using Intune.
If BitLocker is not enabled on a device after deploying a policy, check the encryption report to see if the device meets the prerequisites.
Joy has well explained the working mechanism of Bitlocker encryption, the internal OS components involved, and most importantly, Take a look at the blog post here if you have not seen it yet – why it is necessary and how it helps secure the OS platform from cold boot attacks.
There are already Bitlocker series providing you in-depth details on Bitlocker policies and working mechanisms. Links to the posts are mentioned below. Give them a read if you have not yet.
- Part 1 – Bitlocker Unlocked with Joy – Behind the Scenes Windows 10
- Part 2 – Device Encryption – Bitlocker made Effortlessly
- Part 3 – Deciphering Intune’s Scope w.r.t Bitlocker Drive Encryption
- Part 4 – Intune and Silent Encryption – A Deeper Dive to Explore the Internal
If you are experiencing any Bitlocker Policy missing with new experience, You can report it back to Microsoft Intune Team, Also, a hotfix is currently rolling out to all Intune tenants over the next few days to resolve this.
Author
About Author – Jitesh, Microsoft MVP, has over six years of working experience in the IT Industry. He writes and shares his experiences related to Microsoft device management technologies and IT Infrastructure management. His primary focus is Windows 10/11 Deployment solution with Configuration Manager, Microsoft Deployment Toolkit (MDT), and Microsoft Intune.


Hi,
In this new policy, I cant find how to upload backup recovery keys to Entra ID (like there is in configuration profile), are you guys aware how to do it in endpoint protection?
I’m also missing the option to upload backup recovery keys to Entra ID in these new endpoint security profile.