Let’s discuss MDE Portal Security Settings Policy Creation and Troubleshooting using Windows Sense Event Logs. We will cover the simple process of crafting security policies and deploying them to devices managed by MDE.
You can deploy these policies to work group join devices, Linux servers, Mac OS devices etc. In this post, we will explore the differences between the UI experience in the policy creation of Intune portal and the MDE portal and also explain the limitations of the MDE portal security policy creation process.
We have an article highlighting how to Enable New MDE Security Settings Management Experience. A security policy is the backbone of an organization’s protection strategy. The post will show how to create Azure AD or Entra dynamic groups to deploy these policies only to MDE-managed devices.
In the article, we will learn how to make Azure AD or Entra dynamic groups apply these policies exclusively to MDE-managed devices. We will also cover how to troubleshoot both on the client side and within the portal to identify any problems with the policies we deployed. Additionally, a new event log node will be introduced specifically for addressing troubleshooting scenarios related to devices managed by MDE.
- Workgroup Joined Device Enrollment to MDE Defender for Endpoint
- Latest MDE Architecture Changes to Enhance Onboarding Experience
- MDE Troubleshooting Tools Explained
What is MDE Portal Security Settings Policy?
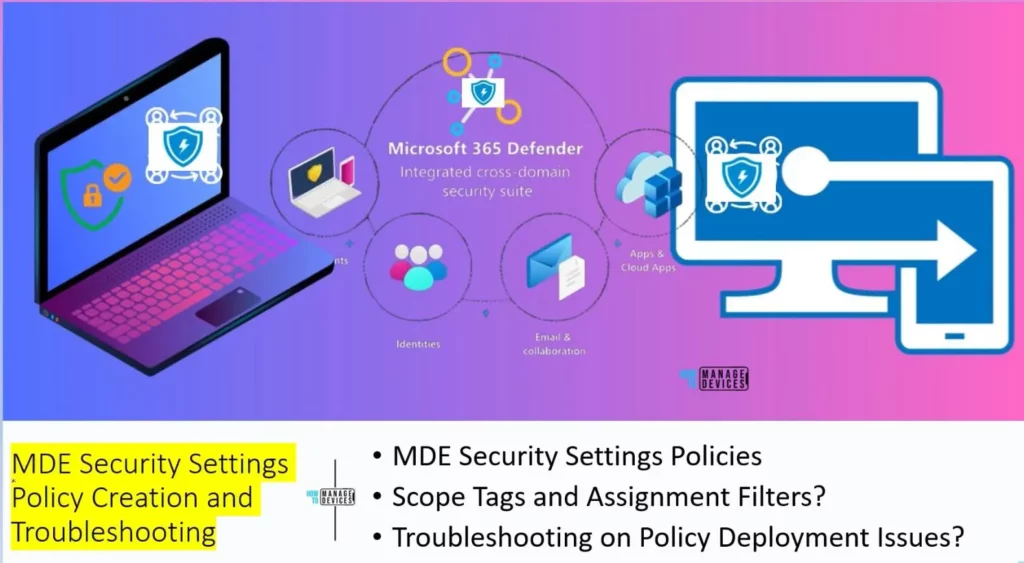
The MDE Portal, Security Settings Policy, is a configuration framework within the Microsoft Defender for Endpoint (MDE) portal. It allows you to define and manage security-related rules, configurations, and practices for devices managed by MDE.
MDE Portal Security Settings Policy Creation and Troubleshooting using Windows Sense Event Logs
This video provides a comprehensive overview of MDE-managed devices and the overview of security policies and settings accessible through the MDE portal. This video encompasses a deep dive into troubleshooting techniques, with insights into Microsoft’s transmission of crucial event logs, event IDs, and related components.
MDE Portal Security Settings Policy Creation and Troubleshooting
Let’s check how to create MDE security settings policies and the troubleshooting process, specifically focusing on the essential event logs within the MDE portal. You will also learn how to assess the status of your policy settings results within the Intune portal, gaining insights into whether the status can be tracked there.
Microsoft has introduced a fresh improvement for Defender for Endpoint. Our previous post showcased the latest MDE architecture changes designed to improve the onboarding experience.
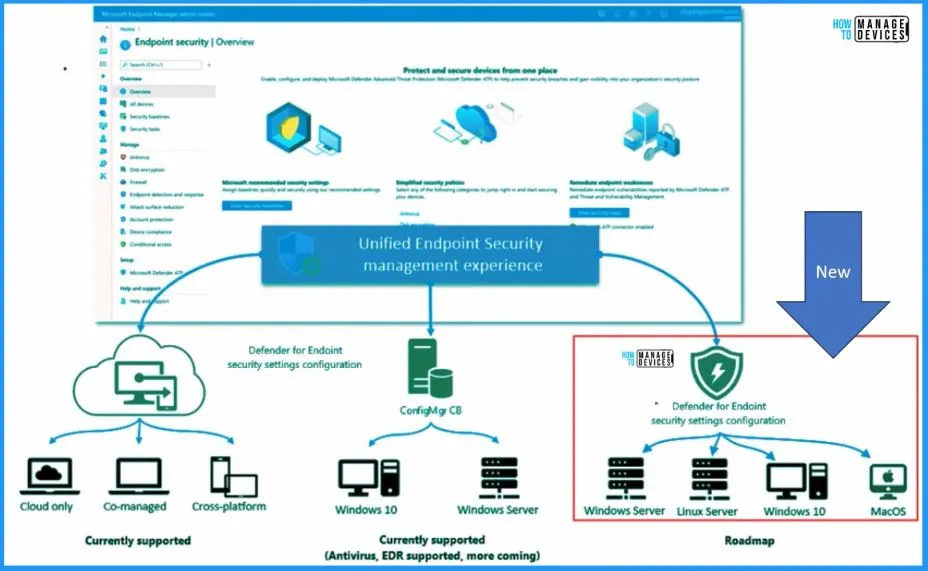
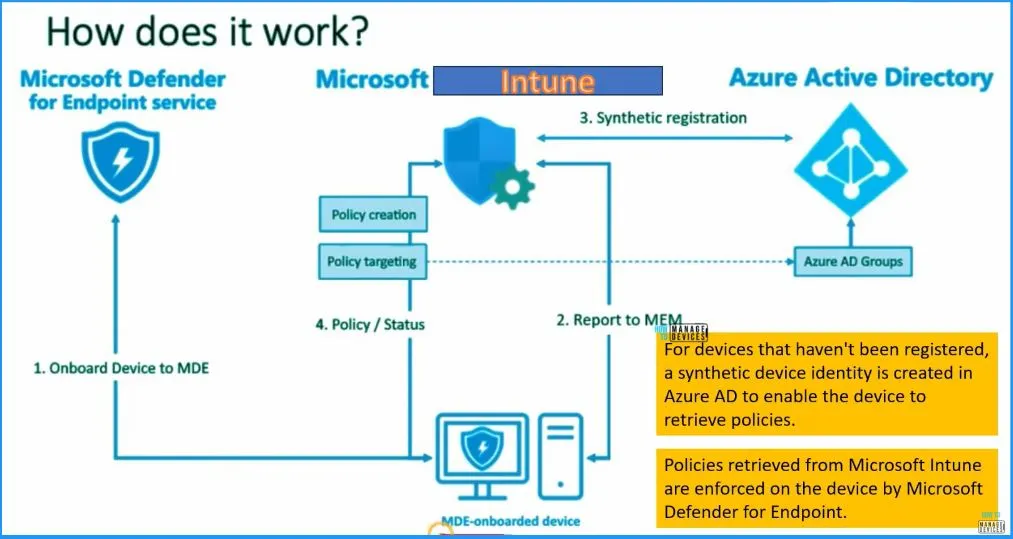
Let’s check the MDE Enrollment flow in more detail with clarity. We will use the latest MDE Architecture schema diagram to make it easy.
- Onboard Device to MDE
- Report to Microsoft Intune
- Synthetic Device Registration
- Send the policy status to Intune
Create Security Settings from Microsoft 365 Defender portal
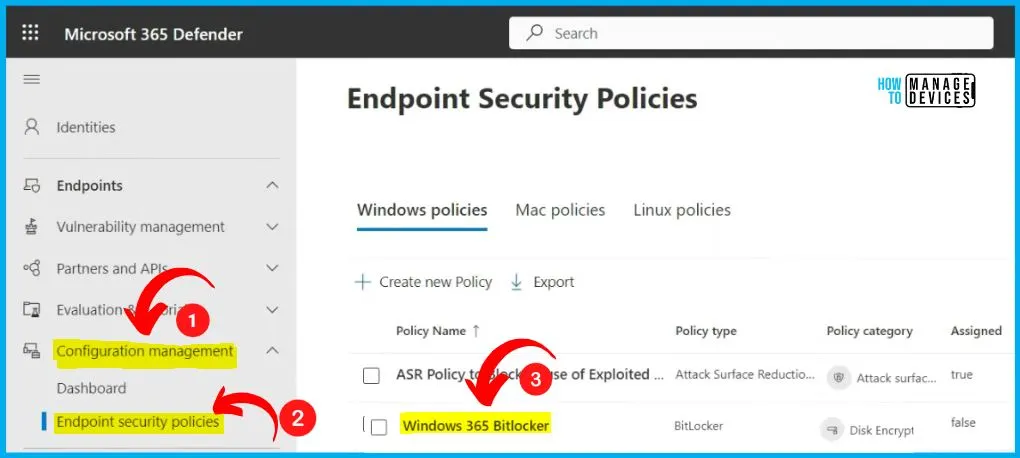
Let’s walk through crafting security settings using the Microsoft 365 Defender portal, accessible at security.microsoft.com. When you scroll down and explore the navigation menu on the left-hand side under “Endpoints,” you will see the option for “Configuration Management.” That’s where you will find the path to create configurations for MDE security settings.
- Configuration management includes 2 options such as Dashboard and Endpoint security policies.
- Select Endpoint security policies from the Configuration management
- In this node, you can see all the MDE-related policies from Intune
- All these policies are created in Intune
- In the below window, you can see the policy name, policy type, policy category etc.
- Select Windows 365 BitLocker policy from the below window
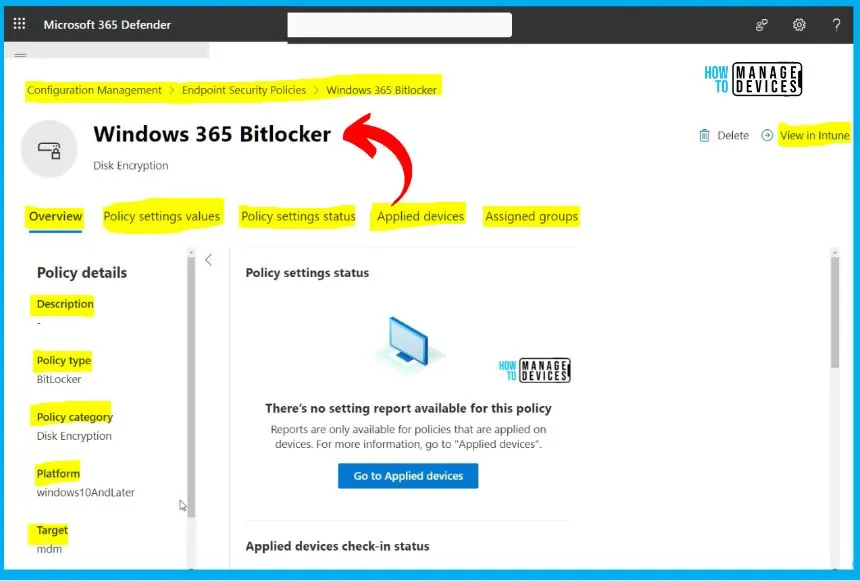
Windows 365 Bitlocker Policy
Let’s take a look at the BitLocker policy. In the BitLocker policy window below, you will find several tabs: Overview, Policy Settings Values, Policy Settings Status, Applied Devices, and Assigned Groups. The experience of the Endpoint security policies node is aligned with Microsoft 365 Defender portal experience, so it is different from Intune experience. If you are familiar with Intune, this would be a bit different.
- On the top right corner, you will be able to see a link to Intune portal
- Configuration management > Endpoint security > Windows 365 Bitlocker
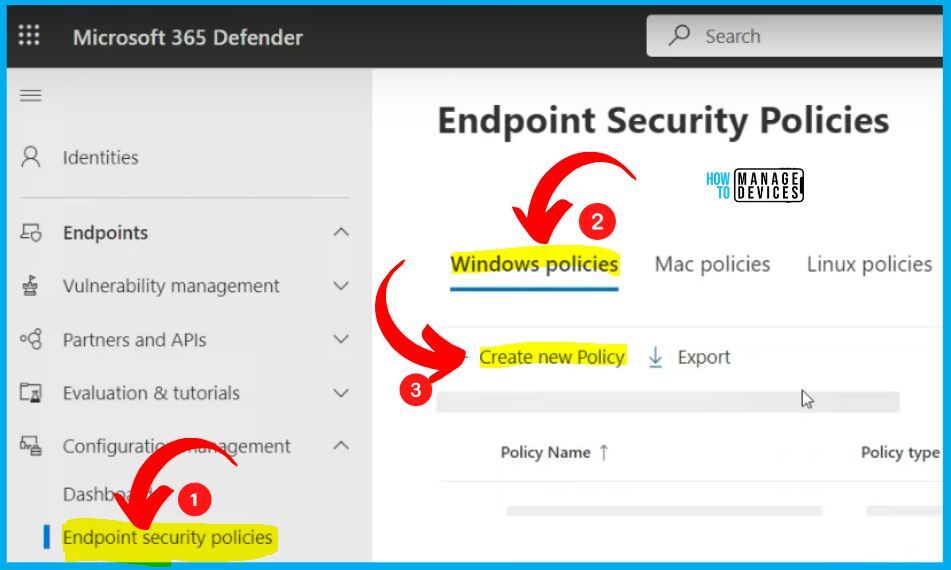
Create a Windows Policy from Endpoint Security Policy
Let’s going to create a Windows policy from the Endpoint security policy. Click on the Create new policy button from the below window. A Windows policy in Microsoft Defender for Endpoint (MDE) is a structured set of security configurations and rules specifically tailored for Windows devices.
Create a New Policy
Select the Platform as Windows 10, Windows 11, and Windows Server in the Create a new policy window. Select the Templates as Microsoft Defender Antivirus. Windows Defender Antivirus is the next-generation protection component of Microsoft Defender for Endpoint.
Next-generation protection brings together machine learning,big-data analysis, in-depth threat resistance research, and cloud infrastructure to protect devices in your enterprise organization. Click the Create Policy button.
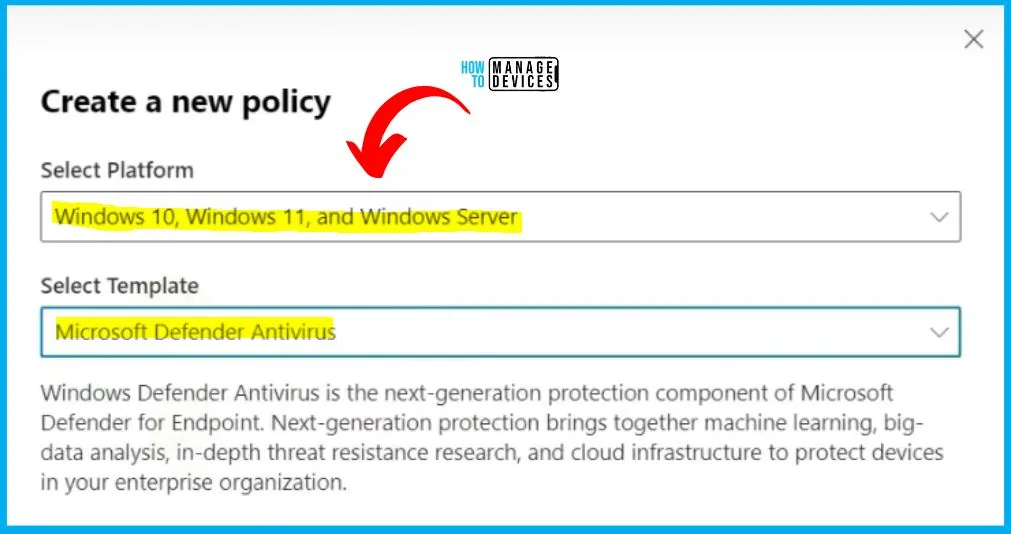
Basic Tab in Policy Creation
This policy creation step in MDE is different from Intune portal. In the Basics tab, enter the Name and Description. In the Basics tab, provide the required information. Fill in the Name field with “MDE Antivirus Policies” and input the corresponding description as “Policies for MDE Antivirus Protection.”
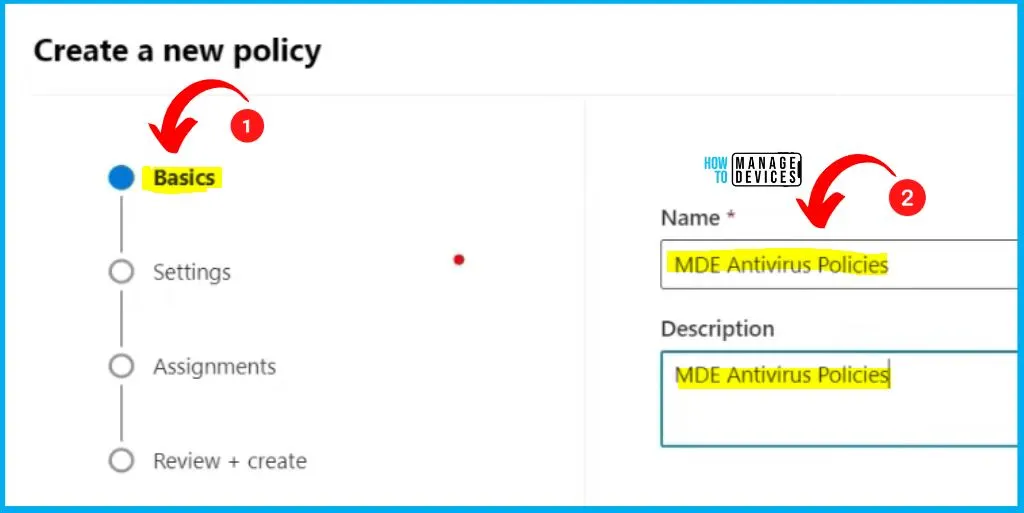
Settings Tab in Policy Creation
The Settings tab is the 2nd step in policy creation. The “Settings” tab in Microsoft Defender for Endpoint (MDE) is a dedicated section where you can define and customize various configurations related to your security policies. Within this tab, you can specify specific rules, preferences etc.
| Defender Policy | Configured / Not Configured |
|---|---|
| Allow Archive Scanning | Not Configured |
| Allow Behavior Monitoring | Configured |
| Allow Cloud Protection | Configured |
| Allow Email Scanning | Not Configured |
| Allow Full Scan On Mapped Network Drives | Configured |
| Allow Full Scan Removable Drive Scanning | Not Configured |
| [Deprecated] Allow Instruction Prevention System | Not Configured |
| Allow Scanning of all downloaded files and attachments | Enabled |
| Allow Realtime Monitoring | Disabled |
| Allow Scanning Network Files | Not Configured |
| Allow Script Scanning | Disabled |
| Allow User UL Access | Not Configured |
| Avg CPU Load Factor | Disabled |
| Check For Signature Before Running Scan | Not Configured |
| Cloud Block Level | Not Configured |
| Cloud Extended Timeout | Enabled |
| Day To Retain Cleaned Malware | Not Configured |
| Disable Catchup Full Scan | Enabled |
| Disable Catchup Quick Scan | Not Configured |
| Enable Low CPU Priority | Enabled |
| Enable Network Protection | Not Configured |
| Excluded Extensions | Enabled |
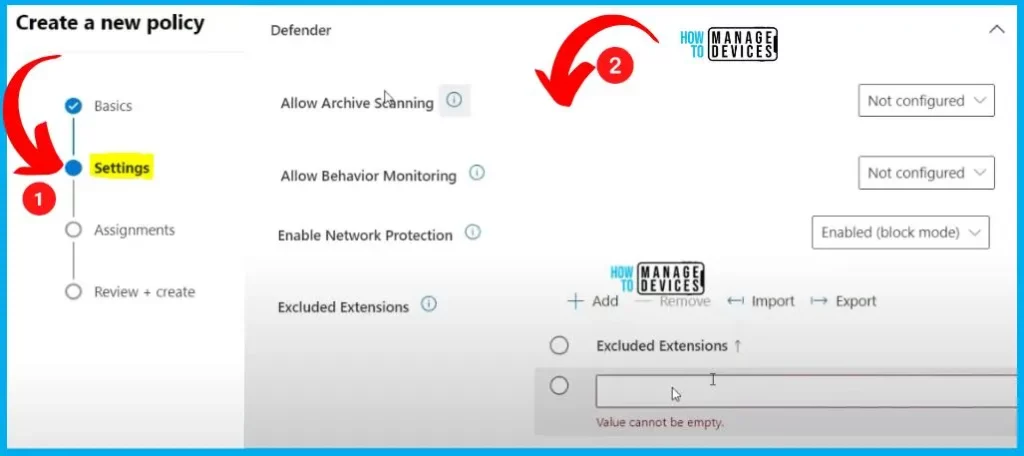
Assignments Tab in the Policy Creation
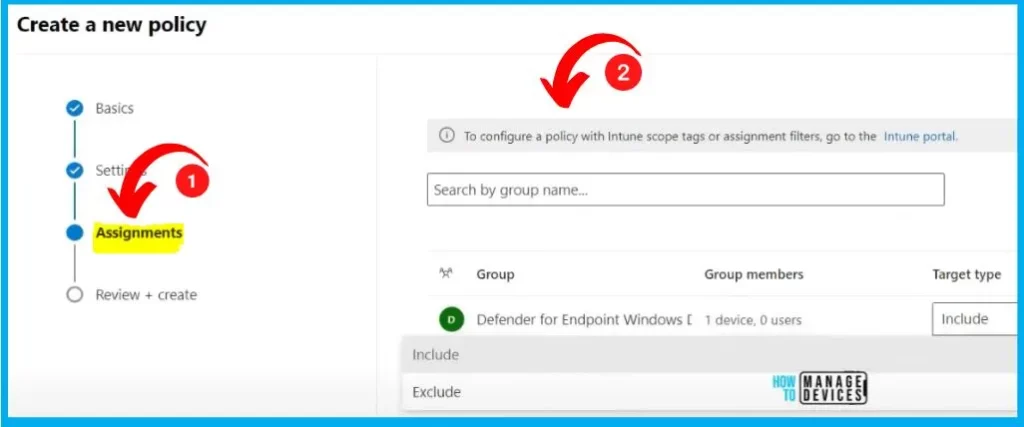
Go to the Intune portal to configure a policy with Intune scope tags or assignment filters. The assignment is the 3rd step in Policy creation. The assignment tab helps you to include and exclude groups.
The “Review + Create” tab offers a comprehensive overview, allowing you to verify and confirm all the specified information before finalizing the creation. It summarises the item’s attributes, ensuring everything aligns with your intended configuration.
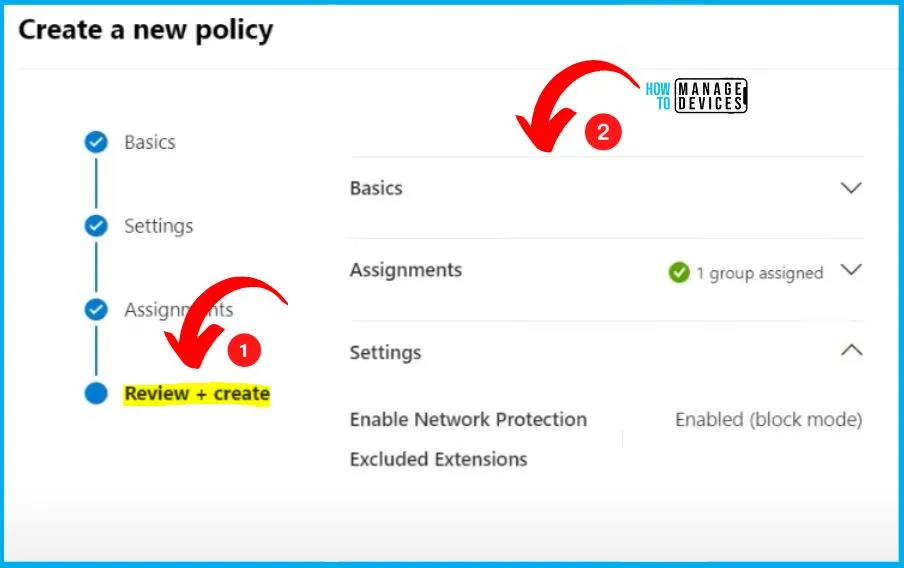
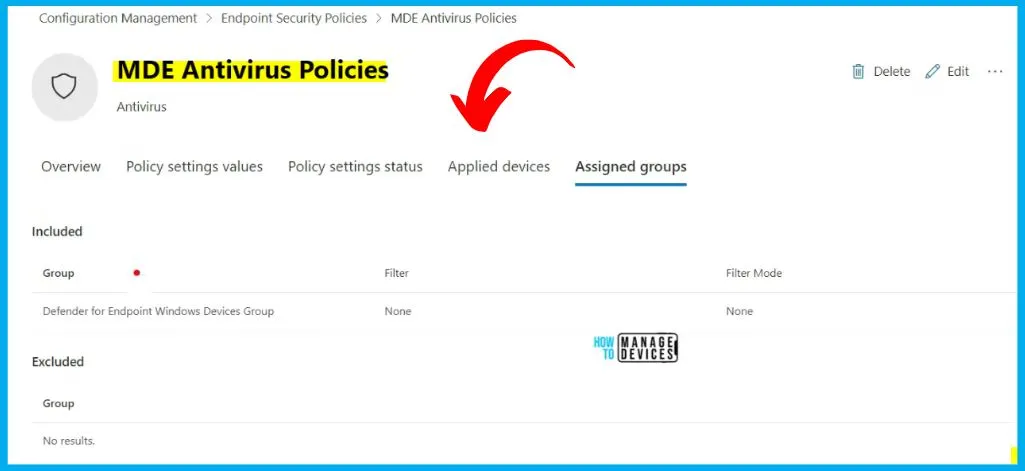
The below window helps you to show that the MDE Antivirus policies are created successfully. The MDE Antivirus policies show the tabs such as Overview, Policy settings values, Policy settings status, applied devices, Assigned groups etc. And the policy also shows the Description, Policy type, Policy category, Platform Target etc.
- Navigate to the “Devices” section from MS 365 Defender portal and pick out “mdetestvm.”
- Access the “Security Policies” menu.
- Currently, no policies have been applied to this particular device.
- To proceed, click on the three dots (…) in the window’s top right corner, and then select the option for “Policy Sync” from the available choices.

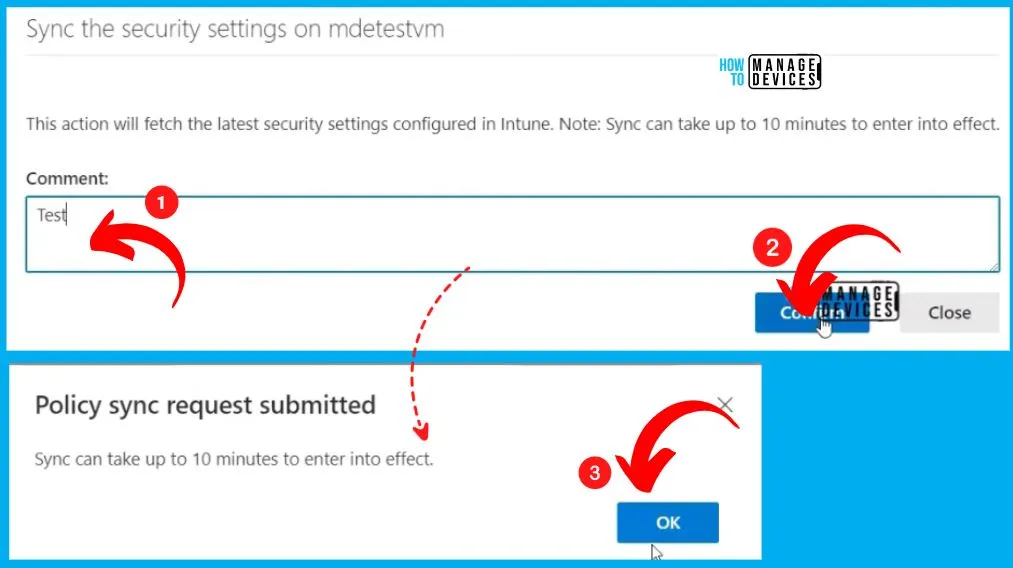
Sync the Security Settings on mdetestvm
This action will fetch the latest security settings configured in Intune. Sync can take up to 10 minutes to enter into effect. Enter a comment in the first window as Test and click the Confirm button. The 2nd window shows the policy sync request submitted. Click the Ok button.
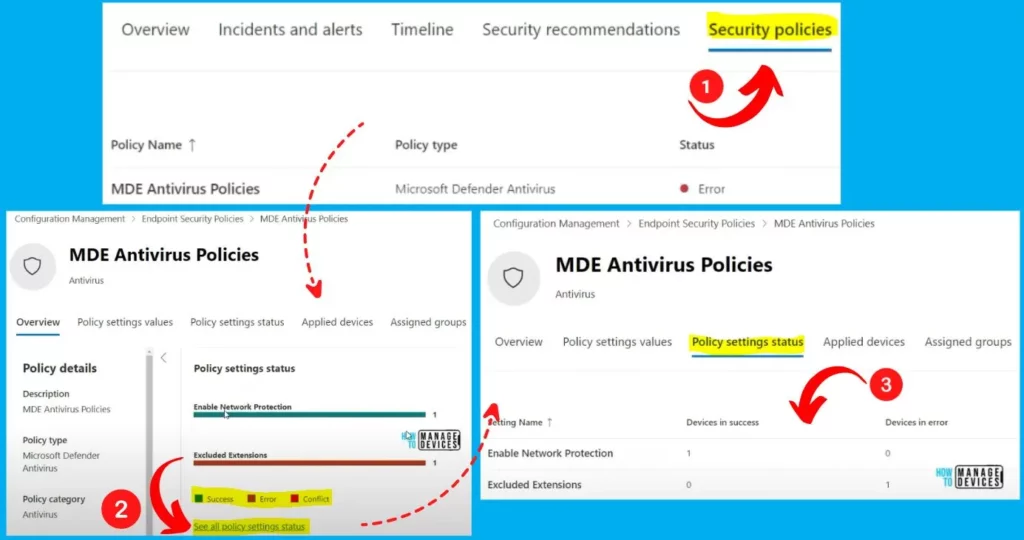
The sync request is initiated. The MDE Antivirus Policies are now successfully initiated and appear under the security policies menu. The policy settings status shows the Enable network protection is successful, but the Excluded extensions are in error.
Click the “See all policy settings status” button from the 2nd window. It shows 2 settings: Enable network protection and the 2nd one is Excluded Extensions. Enable network protection is a success, but the Excluded Extensions that got failed.
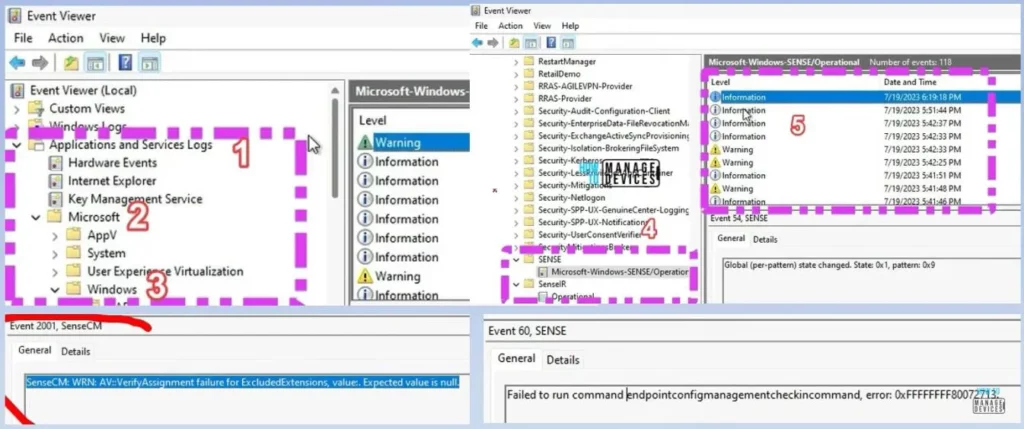
Event Log
Let’s go to the device and check the event log. There is a new event log called SENSE. This is part of Microsoft Windows SENSE. It is part of Application and Services Logs > Microsoft Windows > SENSE. While clicking the Microsoft Windows SENSE/operational shows, the network detection and response execution has started.
So Network protection is Enabled now. You can see different sources such as SENSE, SenseCM etc. We can also see the error that “ Windows Defender Advanced Threat Protection Network Detection and Response Execution has Endeed.” in the MDE portal. No value is provided, so there is an error in the deployment.
- MDE Security Settings Event Logs – Microsoft Sense Event Logs
- Event ID 60 Failed to run command endpointconfigmanagementcheckincommand, error: 0xFFFFFFFF80072713.
- Event ID 2001 – SenseCM: WRN: Import/Setup error on WindowsSecurityExperience.psm1, HResult: -2147024894. This warning is only relevant for private preview customers. Error message: The specified module ‘C:\ProgramData\Microsoft\Windows Defender Advanced Threat Protection\SenseCM\WindowsSecurityExperience.psm1’ was not loaded because no valid module file was found in any module directory.
- Event ID 2001 – SenseCM: WRN: AV::VerifyAssignment failure for ExcludedExtensions, value:. The expected value is null. SenseCM: WRN: AV::VerifyAssignment failure for ExcludedExtensions, value:. Expected value is null.
Author
About Author – Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She loves writing on Windows 11 and related technologies. She is also keen to find solutions and write about day-to-day tech problems.