Hi, let’s discuss about Data Flow Architecture for Intune and Security Copilot. Microsoft has shared detailed information on the security copilot architecture. The details are given in the latest Technical Takeoff session by Lavanya Lakshman.
Security Copilot is a cloud-based tool that helps security professionals in different situations. If you use Microsoft Intune and Security Copilot together, you can use Security Copilot to see information about your devices, apps, and policies.
It is a powerful tool that can help you with security. Security Copilot uses Generative AI to understand what you are looking for, and it will give you the information you need. You can use prompts to get more information and understand your security mode.
Microsoft 365 Copilot comes with additional licensing costs, and many organizations are already onboarded with the preview version of Copilot. You can download it from the following post – Microsoft 365 Copilot Architecture Visio.
- Intune Device Assistance Features with Copilot
- Download Microsoft 365 Copilot Architecture Visio
- Intune EPM Support Approve Scenario Explained
Microsoft Security Copilot
Security Copilot is built for those individuals working in areas such as IT admins or help desk support. The aim is to empower them with more diverse roles within their organization by leveraging the gathered data.
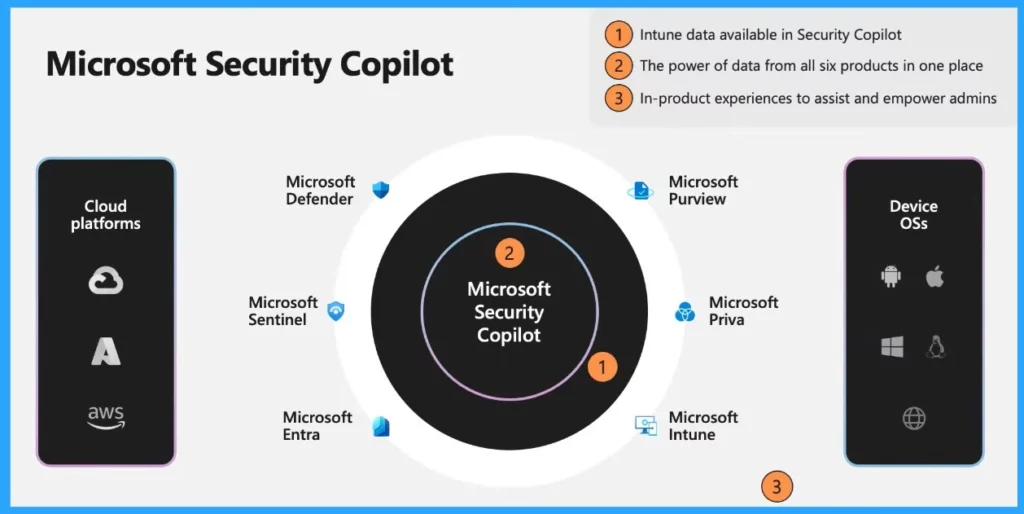
Intune data is integrated with Security Copilot, which combines data from 6 Microsoft products for device management and security.
| Data Products for Device management and Security |
|---|
| Microsoft Defender |
| Microsoft Sentinel |
| Microsoft Entra |
| Microsoft Pruview |
| Microsoft Priva |
| Microsoft Intune |
These are the 3 key principles of Security Copilot with Microsoft Intune.
- Intune data available in Security Copilot
- The power of data from all six products in one place
- In-product experiences to assist and empower admins
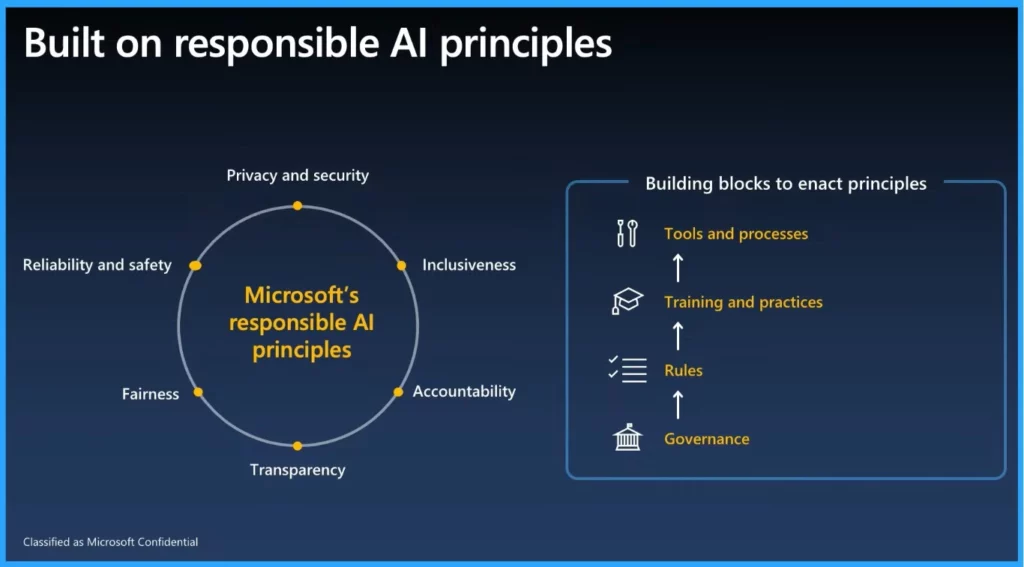
Built on Responsible AI Principles
Microsoft has a framework that puts principles, privacy and security at the core of AI development and deployment. There are 6 essential pivots around privacy and security being front and centre.
To act on the principle, we need these steps: First, follow the governance process. Second, set the rules for AI needs. Third, learn and use best practices. Last, pick the right tools for AI work. This will make our customers safe.
- First, follow the Governance process
- 2nd, set the rules for AI
- In 3rd step, Training and practices
- In the last Tools and process
| 6 Important Pivots |
|---|
| Privacy and security |
| Reliability and safety |
| Inclusiveness |
| Fairness |
| Accountability |
| Transparency |
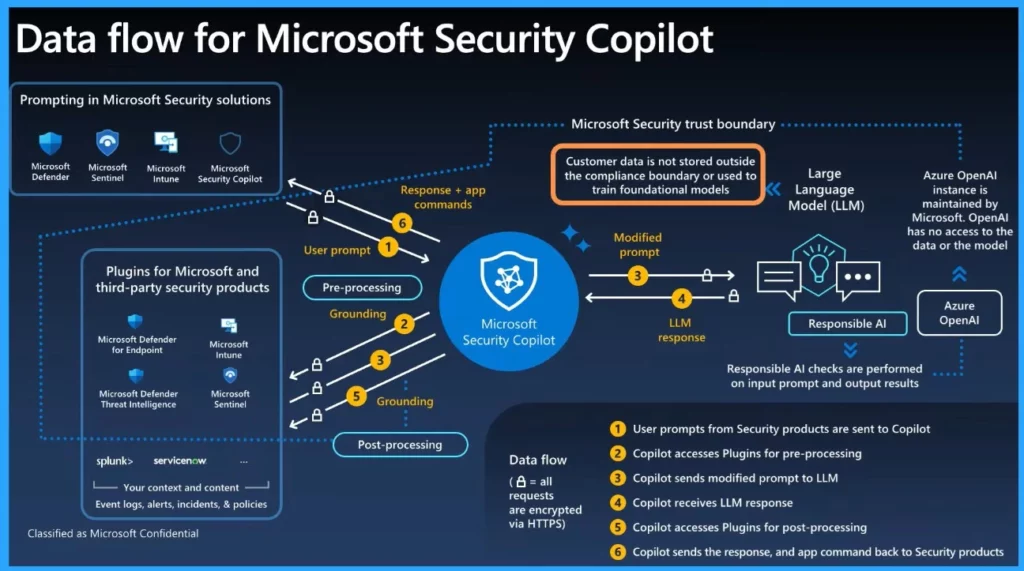
Data Flow Architecture for Intune and Security Copilot
Security Copilot integrates various solutions, such as Intune, Defender, and Sentinel. Once prompts are triggered, they will go through a pre-processing stage where the proper selection of skill behind the scenes happens and the various available Microsoft plugins based on the terms and conditions.
These user prompts undergo a pre-processing stage where appropriate skills and Microsoft plugins are selected. If there’s a link with a third-party security product, it’s established before the response preparation begins. AI checks are done during processing.
The response is returned to the user only after final validation with the necessary plugins. These behind-the-scenes enhancements are there to support and empower you. Microsoft ensures that the customer data is not stored outside of the compliance boundary.
| Flow | Details |
|---|---|
| 1 | User prompts from Security products are sent to Copilot |
| 2 | Copilot sends the response and app command back to Security products |
| 3 | Copilot accesses Plugins for pre-processing |
| 4 | Copilot sends a modified prompt to LLM |
| 5 | Copilot receives LLM response |
| 6 | Copilot accesses Plugins for post-processing |
All these Microsoft Security Copilot data flows are encrypted via HTTPS communication. Also, Customer data is not stored outside the compliance boundary or used for foundational models.
Video – Generative AI and the next generation of Intune features
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here – HTMD WhatsApp.
Author
Krishna. R is a computer enthusiast. She loves writing on Windows 11 and Intune-related technologies. She likes to share her knowledge, quick tips, and tricks with Windows 11 or Windows 10 with the community.

