Let’s check Intune Security Policy Configuration Options. Intune offers various security policy configuration options to protect your organization’s devices and data. This post will explore how to customize and implement security policies within Intune.
When configuring security policies in Microsoft Intune, several options cater to different device platforms and security standards. The best option for you depends on your specific requirements and the level of complexity you are comfortable with.
The Intune security policy configuration options include the options such as Settings catalog, Endpoint security and custom security policies, and more. These options provide a comprehensive framework to safeguard your organization’s devices, data, and resources from potential threats, ensuring a secure user environment.
Welcome to our post on the Intune Design Decisions Free Training – Version 1 Starter Kit – Basic. This post offers an overview of the extensive training video series that provide individuals with the necessary knowledge and skills for effective device management using Intune.
- Intune Integration Scenarios 1st 2nd 3rd Party Integration Experiences
- New iOS Android macOS Device Management Options with Intune
What are Intune Design Decisions?
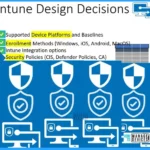
When making architectural decisions for Intune, 3 fundamental pillars form the foundation of the decision-making process. These pillars are Existing Investments, Device Management, and Integration. It supports the Device platform and baseline.
What are the Intune Security Policy Creation Options?
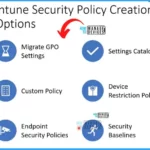
The Intune security policy creation options include Migrate GPO settings, Settings catalog, custom policy, device restriction policy, endpoint security policies, and security baselines.
What are Intune Security Policies?

Intune Security Policies help you to secure managed devices; you need to apply security policies to the devices. Organizations follow various security standards; the CIS benchmark is the most commonly std used. Group Policies settings are the most popular method to implement security policies. More organizations are moving to Intune-based security policies to implement the security baseline.
Intune Security Policy Configuration Options – Video
Our comprehensive video series on Intune design decisions has dedicated a segment specifically to Intune security policies. Intune Security Policy Configuration Options is the Design Decision Part – 5 Video.
If you haven’t had the opportunity to watch the previous 4 videos, we highly recommend taking the time to do so. These videos provide invaluable insights into configuring and optimizing security policies within the Intune platform.
Intune Compliance Policies
You can help protect organizational data with compliance policies by requiring users and devices to meet some requirements such as BitLocker encryption, disk encryption, password pin complexity, etc. Compliance policy supports all device platforms. Intune compliance policies must be part of your design decision, and you must recommend the organization to use them.
How to Manage Intune Compliance Policy Settings
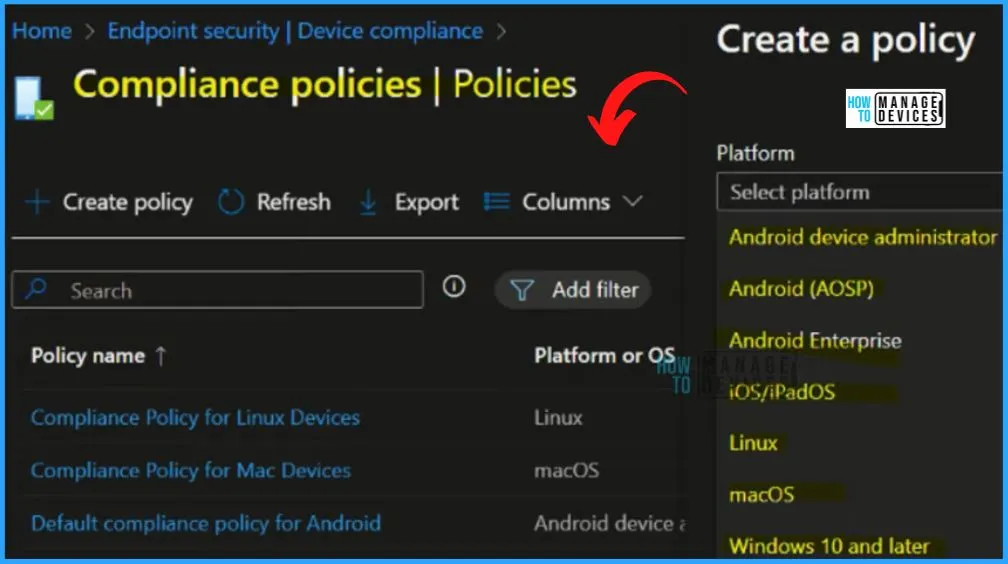
Group Policy Migration Options
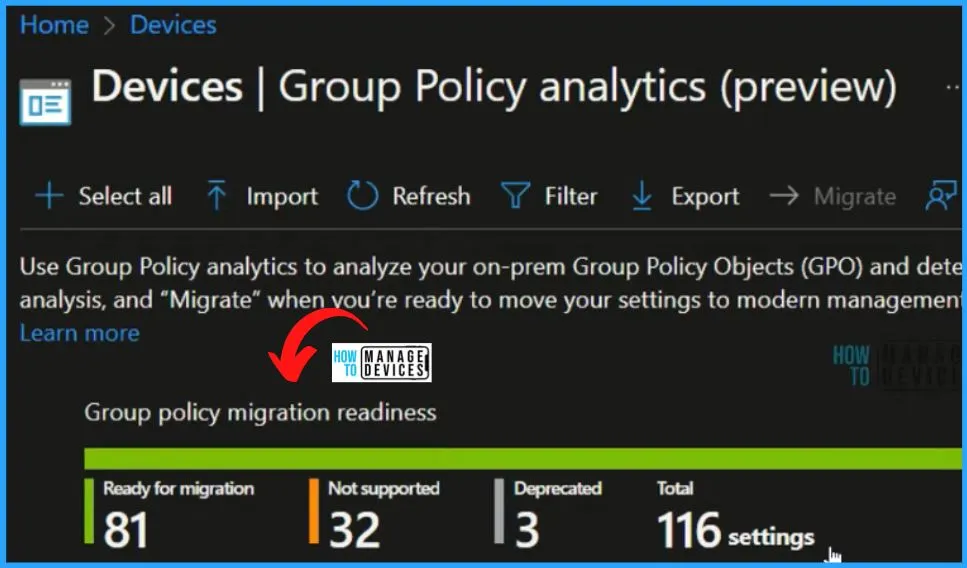
Let’s look into Group policy Migration Options. If you are using group policies with your legacy workplace devices and moving to Modern management, you want to migrate all the group policies to Intune security policies. You have the option to migrate support GPO settings to Intune policies. Migrate Group Policies GPOs to Intune Settings Catalog policy.
- You can use Group Policy analytics to Analyze, Import, and Create Intune Policies.
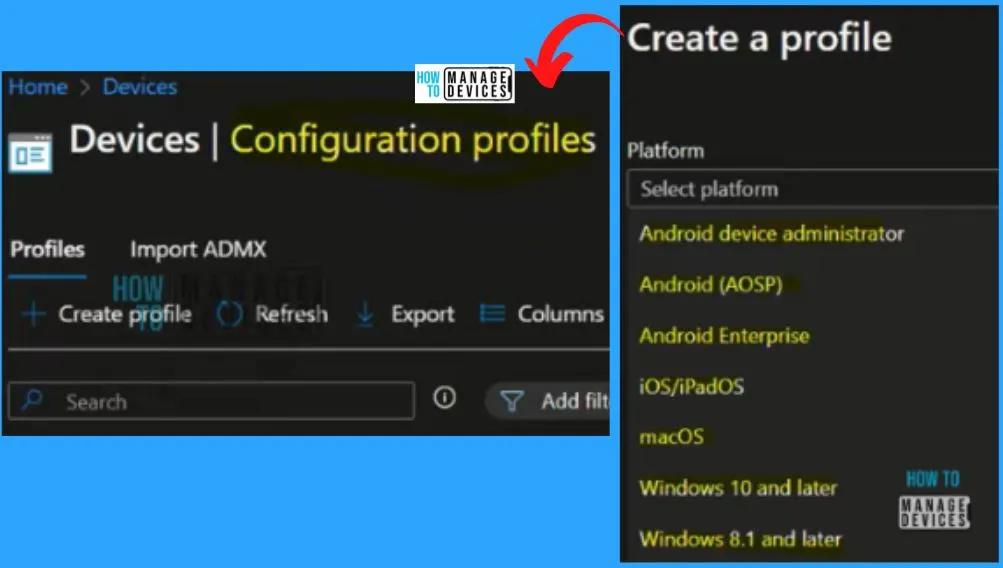
Intune Configuration Profiles
Configuration profiles are a powerful tool in Intune that enables organizations to add and configure settings for devices and seamlessly deploy them across their managed devices. Organizations can tailor the settings to meet their requirements with different configuration profiles.
Let’s explore some of the key types of configuration profiles in Intune. One example of Intune Configuration Profiles – How To Disallow Online Tips Policy Using Intune.
- Administrative templates
- Baselines
- Settings catalog
- Templates
| Configuration Profiles | Android | iOS/iPad | MacOS | Windows | Linux | Chrome |
|---|---|---|---|---|---|---|
| Administrative Templates | No | No | No | Yes | ? | ? |
| Baselines | No | Yes | No | Yes | ? | ? |
| Settings catalog | No | No | Yes | Yes | ? | ? |
| Templates | Yes | Yes | Yes | Yes | ? | ? |
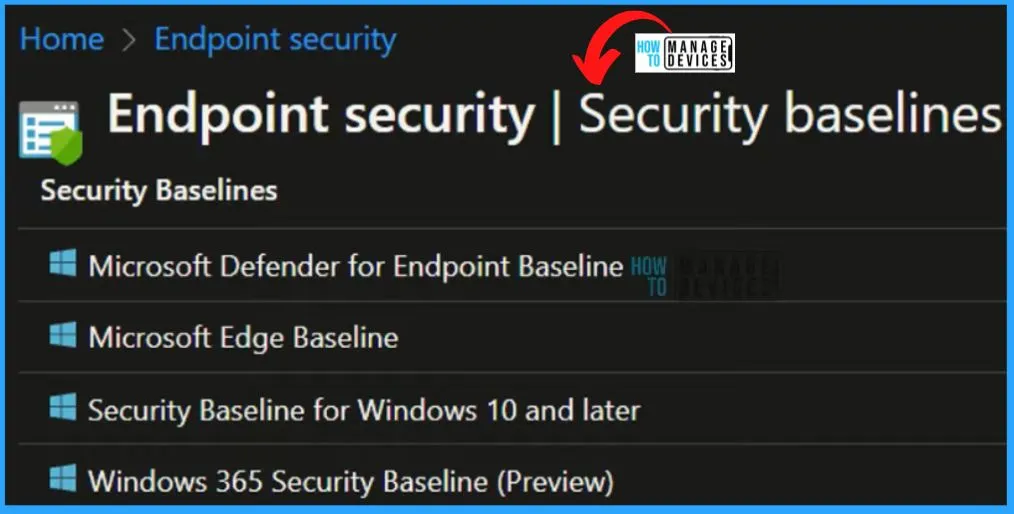
Intune Security Baseline Templates
You can easily use security baselines to apply Microsoft-recommended security configuration settings to your enrolled devices quickly. This is a very easy method to create Intune security policy. You can easily customize these templates and deploy them. Use this template directly to configure it accordingly as per your requirement.
Let’s learn how you can download and configure security baselines – Security Baselines Download Configuration Guide. This applies only to the Windows platform. The following are the baseline templates available in Intune.
- Microsoft Defender for Endpoint Baseline
- Microsoft Edge Baseline
- Security Baseline for Windows 10 and later
- Windows 365 Cloud PC Security Baseline
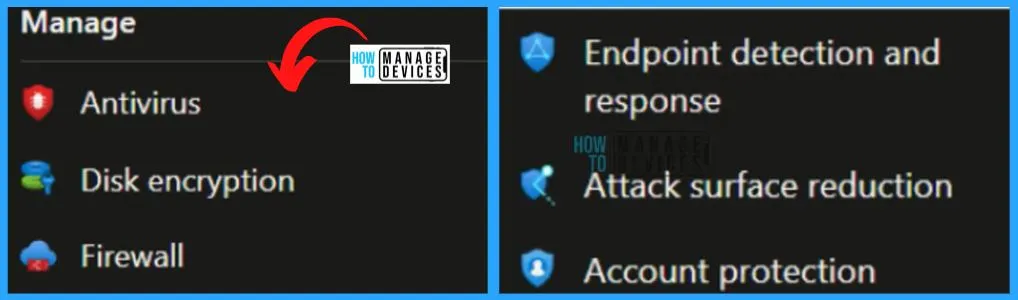
Endpoint Security Policies
This is the best method to create the security policies. This is a simplified security policies creation option for security admins. This is focused on Security admins. So if you have security admins and provided access to security admins in Intune portal, they want to create and manage their security policies such as Antivirus, Disk Encryption, and Firewall.
- Windows platform also supports Attack surface reduction, Endpoint detection and response, and Account protection.
- Intune Endpoint Security Policies Explained
Administrative Templates
Administrative Templates helps to configure 1000’s of security settings that control features for Windows platform and apps. Administrative templates were among the most popular before Microsoft released the settings catalog. The Administrative Templates ADMX policies are very important and useful for Custom ADMX policies.
- There is no need to use administrative templates for out-of-the-box policies such as Microsoft Edge, Google Chrome, Microsoft Office programs, Remote desktop, OneDrive, Passwords, PINs, etc.
- More Details on Import Custom ADMX Administrative Templates in Intune
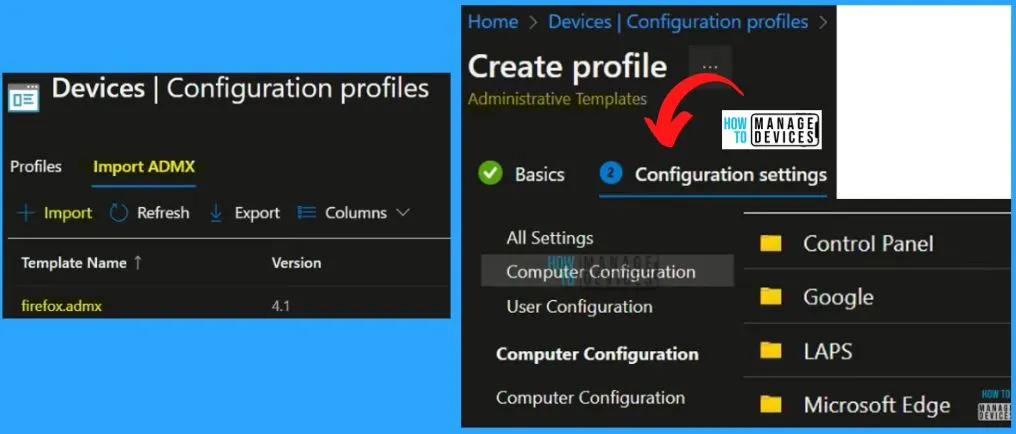
Intune Settings Catalog
Intune Settings Catalog is Intune’s most popular and regularly updated policy catalog. We are recommended to start using or creating Intune security policies using the settings catalog. Settings Catalog is the natural transition from GPO Settings to Intune policies, and it helps you to configure settings at a granular level like GPO settings.
you can learn to create a policy with Intune Settings Catalog – Create Intune Settings Catalog Policy
- Settings Catalog supports MacOS and Windows device platforms.
- No custom policy configuration option, unlike Administrative Templates.
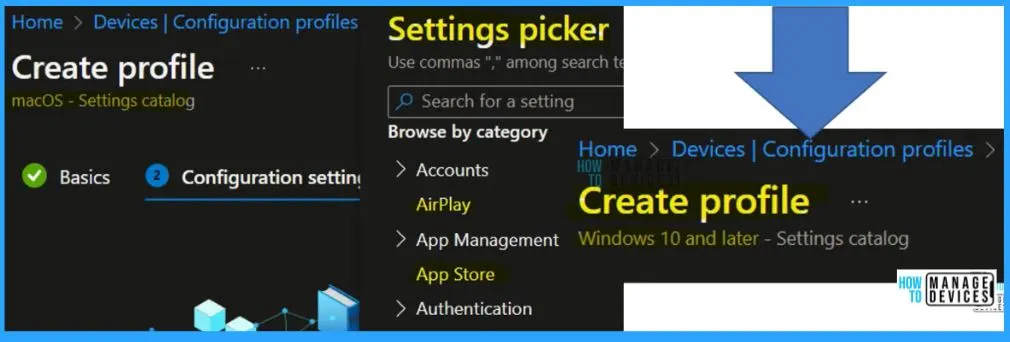
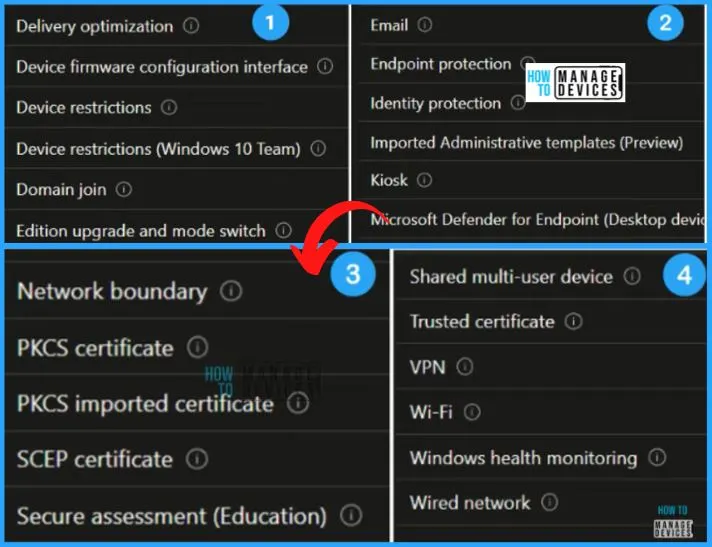
Create Intune Security Policy using Templates
Intune Templates are the logical grouping of settings configuring a feature or concept, such as SCEP/PKCS Cert, Wi-Fi, VPN, Email, kiosk devices, etc. Intune Templates support all platforms, excluding Linux and Chrome.
Intune Endpoint Security Policies Microsoft Endpoint Manager Updates
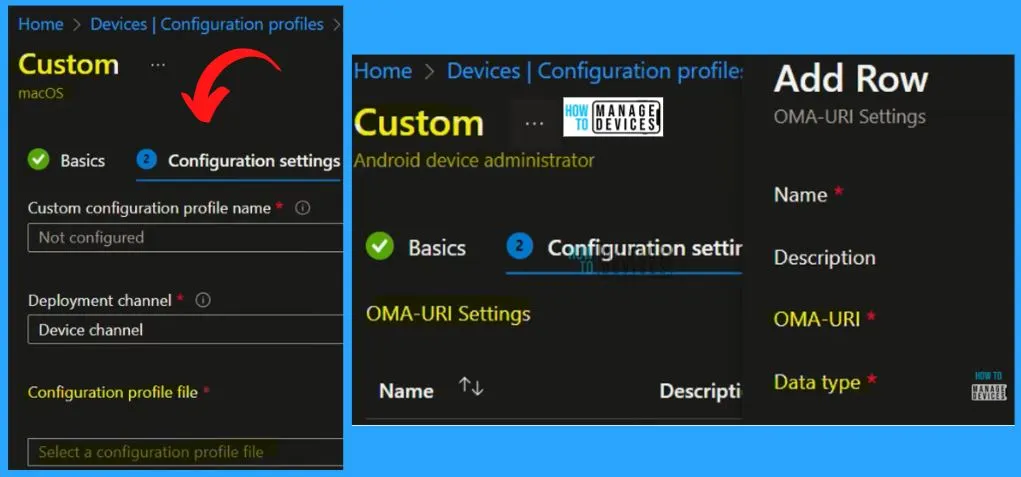
Create Custom Intune Security Policy
You can use custom policies when using device settings and features not built into Intune. Using custom OMA-URI for Windows and Android device platforms, you can create custom Intune security policies. Create Custom Compliance Policies for Linux Devices in Intune.
- Intune security policy Supported Platforms such as MacOS, iOS/iPadOS, Android, and Windows.
High-Level Intune Architecture SaaS View
Various methods and templates are available to streamline the process and ensure effective policy implementation when creating Intune security policies. You got an idea about Intune Security policy creation options, and you might have an idea about the templates you want to use or the methods you want to use to create Intune security policies.
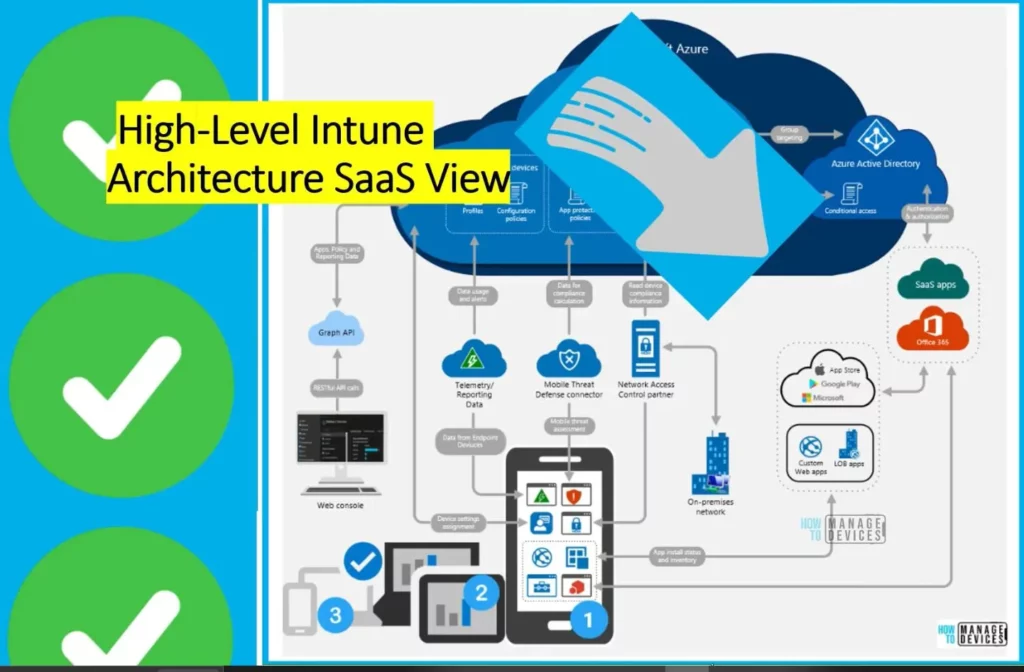
Manage endpoint security policies in Microsoft Intune | Microsoft Learn
Author
About Author – Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She loves writing on Windows 11 and related technologies. She is also keen to find solutions and write about day-to-day tech problems.