Exciting Update from Microsoft! Confidential Virtual Machine Support for Azure Virtual Desktop. AVD Host Pool Provisioning now offers confidential VM and trusted launch security features.
Azure Virtual Desktop now offers Confidential Virtual Machine Support, ensuring heightened data security and privacy for your Cloud-based desktop experiences. Azure’s DCasv5 and ECasv5 Confidential VM Series Introduce Hardware-Based Trusted Execution Environment (TEE) with AMD SEV-SNP Security Capabilities.
This Fortifies Guest Protections, Denies Hypervisor and Host Management Code Access to VM Memory and State, and Safeguards Against Unauthorized Operator Access through Data Encryption in use.
Azure confidential VMs (CVMs) enhance security by providing VM memory encryption with integrity protection, ensuring that guest protections are fortified, and preventing unauthorized access to the VM memory and state by the hypervisor and other host management components.
- Enable Watermarking for Secure Windows 365 and AVD Experience
- New Azure Virtual Desktop App in the Microsoft Store Winget and Intune
What is Azure Confidential Computing?

Azure Confidential computing helps you protect your data while it’s being processed in the Cloud using a hardware-based trusted execution environment or TEE. This encrypts your data in memory and verifies the Cloud environment before processing anything. This way, no one can see, access, or tamper, Including Users, Administrators, and Azure Itself.
Why would anyone Need Azure Confidential Computing?
Azure Confidential Computing is essential for organizations and individuals prioritizing cloud data security, privacy, and compliance. It also helps with the following.
1. Protecting Sensitive Data
2. Compliance Requirements
3. Securing Critical Workloads
4. Intellectual Property Protection
What are Confidential VMs?
Confidential VMs (CVMs) are specialized virtual machines offered by Microsoft Azure that prioritize data security and privacy. They provide an additional layer of protection for sensitive workloads by leveraging hardware-based security features.
The key distinguishing feature of CVMs is the use of a Trusted Execution Environment (TEE) provided by the underlying hardware, such as AMD SEV-SNP or Intel SGX.
What is Trusted Launch?
TL stands for Trusted Launch, is the new default option when building your AVD session host, and it helps you to protect against advanced and persistent attack techniques. It provides a secure framework for deploying VMs with authenticated boot loaders, OS kernels, and drivers.
Moreover, TL ensures the utmost protection for critical components, safeguarding keys, certificates, and secrets within the VMs. This comprehensive security approach offers peace of mind and confidence in the integrity of your virtualized environment.
1. Trusted Launch is now Enabled by default for all Windows images
Confidential Virtual Machine Support for Azure Virtual Desktop (AVD)
You can easily use Confidential computing on your AVD session host. Windows 11’s requirement for a TPM (Trusted Platform Module) chip is a positive development, especially for leveraging Confidential Computing capabilities alongside the added security layer called Trusted Launch.
- Trusted Launch goes the extra mile in enhancing VM security by utilizing the TPM chip and combining it with secure boot features specific to your VM generation.
- It achieves this by digitally signing the VM’s bootloader, OS Kernel, and drivers, thus establishing a robust shield against bootkit and rootkit attacks during the VM’s startup process.
- With this powerful security measure in place, users can rest assured that their virtual machines are safeguarded against potential threats from the moment they are initialized.
To Deploy Confidential Virtual Machines (CVMs) with AVD Host Pool Provisioning
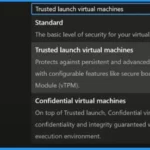
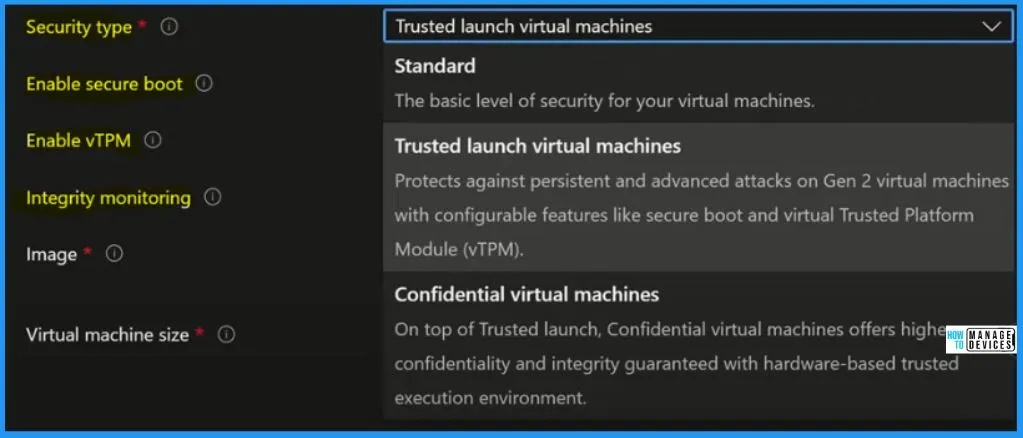
For building your host, you select all of your basic options. From Virtual machines to a host pool shows the Security Type settings. Trusted launch virtual machines are the default security type. Clicking the dropdown arrow from Security types shows other options such as Standard and Confidential Virtual machine.
Integrity monitoring is a new feature that utilizes Microsoft Azure attestation to validate the platform state. By enabling cryptographic attestation and VM boot integrity verification, this powerful tool actively monitors VM booting, promptly issuing alerts if attestation falls short of the defined baseline.
| Security Type | Used to |
|---|---|
| Standard | The basic level of security for your virtual machines. |
| Trusted launch virtual machines | Protects against persistent and advanced attacks on Gen 2 virtual machines with configurable features like secure boot and virtual Trusted platform module(vTPM) |
| Confidential virtual machines | On top of the Trusted launch, Confidential virtual machines offer higher confidentiality and integrity guaranteed with a hardware-based trusted execution environment. |
Create New AVD Host Pool with Confidential Virtual Machine
Let’s create a new AVD Host Pool with Confidential Virtual Machine. You need to follow the steps to create a new hostpool, as explained below.
- Login to portal.azure.com
- Search with “Azure Virtual Desktop“.
- Click on the Azure Virtual Desktop icon, as shown in the below screenshot.
- Click on Create a host pool to continue.
- From Project details, Select Subscription from the drop-down menu.
- Create a new Resource Group – Click on Create New – MEMCM.
- Host pool name – Enter the name of the Host Pool Name – ConfidHTMD.
- Location – Select the Azure region to store Metadata – East US.
- Select Host pool type – Personal or Pooled.
- Select Automatic assignment – The service will select an available host and assign it to a user direct assignment – Admin selects a specific host to assign to a user.
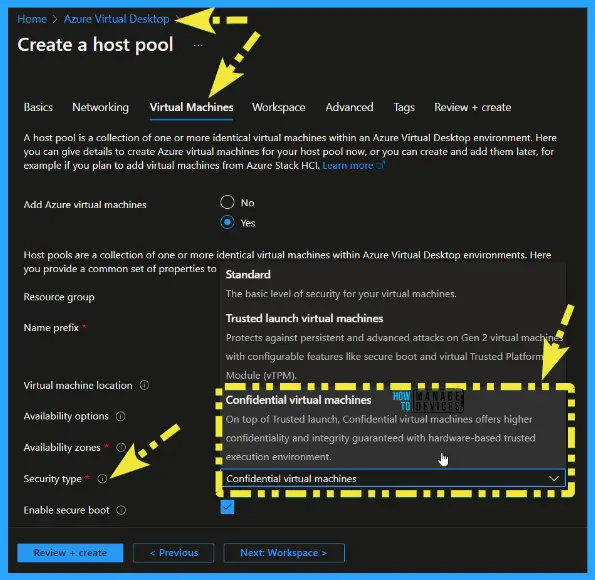
Here you give details to add an AVD virtual machine for the hostpool in an Azure subscription.
- Add virtual machines 👉 Yes.
- Select Resource Group 👉 MEMCM.
- Select Virtual Machine Location 👉 East US
- You can choose a different region for virtual machines than the host pool, especially if you want metadata to be stored in a particular geography. Still, you want the virtual machines closer to the user.
Select the Security Type = Confident Virtual Machines – On top of the Trusted launch, Confidential virtual machines offer higher confidentiality and integrity guaranteed with a hardware-based trusted execution environment.
- More details on the Host Pool creation process are explained – AVD Admin Experience Create New Host Pool | Workspace | Session Host
Benefits of AVD Confidential VMs
A Confidential VM is reffered to as a Compute Engine; your data and applications stay private and encrypted even while in use. The below Table shows the benefits of confidential VMs.
| Benefits of Confidential VMs | Description |
|---|---|
| Robust Hardware-Based Isolation | Confidential VMs offer strong hardware-based isolation between virtual machines, hypervisors, and host management code, ensuring enhanced security. |
| Customizable Attestation Policies | Users can set customizable attestation policies to verify the host’s compliance before deploying Confidential VMs. |
| Cloud-Based Confidential OS Disk Encryption | Before the first boot, Confidential VMs benefit from cloud-based Confidential OS disk encryption, bolstering data security. |
| Flexible Ownership of VM Encryption Keys | Users can own and manage the VM encryption keys, providing greater control and ownership over data security. |
| Secure Key Release with Cryptographic Binding | The release of encryption keys is securely tied to the platform’s successful attestation, strengthening overall VM security. |
| Dedicated Virtual TPM for Attestation and Key Protection | Confidential VMs come with a dedicated virtual Trusted Platform Module (TPM) instance, ensuring robust attestation and protection of keys and secrets. |
| Similar to Trusted Launch for Azure VMs | Confidential VMs share similarities with Trusted Launch for Azure VMs, adding an extra layer of trust and security to the virtualization environment. |
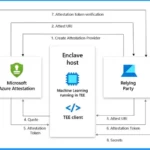
Microsft Azure Attestation
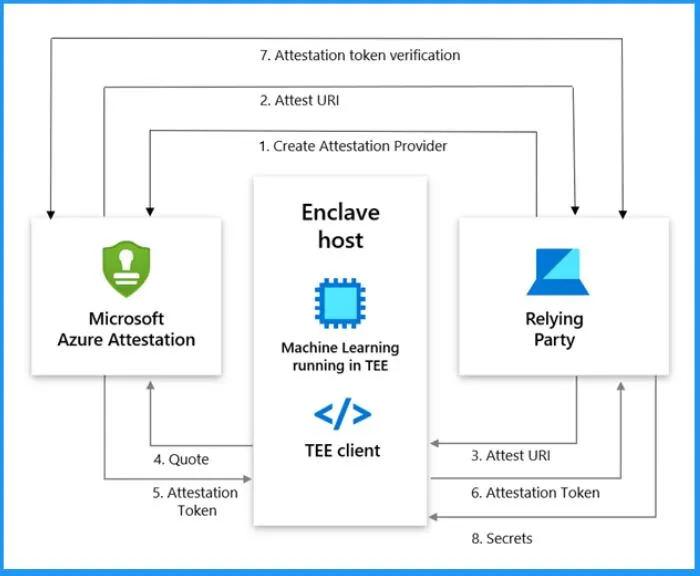
The latest addition to the platform, integrity monitoring, utilizes Microsoft Azure attestation to ensure the validation of your platform state. Microsoft Azure Attestation provides a comprehensive and unified solution for remote verification, enabling the assessment of a platform’s trustworthiness and the integrity of its binaries.
- 1. Create Attestation Provider
- 2. Attest URI
- 3. Attest URI
- 4. Quote
- 5. Attestation Token
- 6. Attestation Token
- 7. attestation token verification
- 8. Secrets
Confidential OS Disk Encryption
Azure confidential VMs provide a new and enhanced disk encryption scheme, which helps to protect all critical partitions of the disk. It also binds disk encryption keys to the virtual machine’s TPM, making the protected disk content accessible only to the VM.
- The encryption keys can securely bypass Azure components such as the hypervisor and host operating system.
- To reduce the attack potential, a dedicated and separate Cloud service also encrypts the disk during the initial creation of the VM.
Differences in Encryption Pricing
Azure confidential VMs employ both the OS disk and a compact, encrypted virtual machine guest state (VMGS) disk, which stores the security state of essential VM components, such as the vTPM and UEFI bootloader. Users should be aware that the VMGS disk might incur a monthly storage cost. As of July 2022, there will be increased costs associated with encrypted OS disks for confidential VMs.
Attestation and TPM Trusted Platform Module
Attestation and TPM (Trusted Platform Module) are two integral components of Azure Confidential Computing, contributing significantly to the overall security and trustworthiness of the platform. It ensures a secure boot process by allowing the VM to start only after successfully attesting the platform’s critical components and security settings. The attestation report includes the following.
- A signed attestation report issued by AMD SEV-SNP
- Platform boot settings
- Platform firmware measurements
- OS measurements
Confidential VM size and Confidential VMs OS Support
Confidential VMs support the VM sizes such as DCasv5-series, DCadsv5-series, ECasv5-series, and ECadsv5-series. The Confidential VMs support the following OS options.
- Ubuntu 20.04 LTS
- Ubuntu 22.04 LTS
- RHEL 9.2 Tech Preview
- Windows Server 2019 Datacenter – x64 Gen 2
- Windows Server 2019 Datacenter Server Core – x64 Gen 2
- Windows Server 2022 Datacenter – x64 Gen 2
- Windows Server 2022 Datacenter: Azure Edition Core – x64 Gen 2
- Windows Server 2022 Datacenter: Azure Edition – x64 Gen 2
- Windows Server 2022 Datacenter Server Core – x64 Gen 2
- Windows 11 Enterprise N, version 22H2 -x64 Gen 2
- Windows 11 Pro, version 22H2 ZH-CN -x64 Gen 2
- Windows 11 Pro, version 22H2 -x64 Gen 2
- Windows 11 Pro N, version 22H2 -x64 Gen 2
- Windows 11 Enterprise, version 22H2 -x64 Gen 2
- Windows 11 Enterprise multi-session, version 22H2 -x64 Gen 2
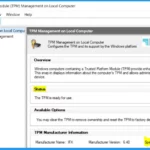
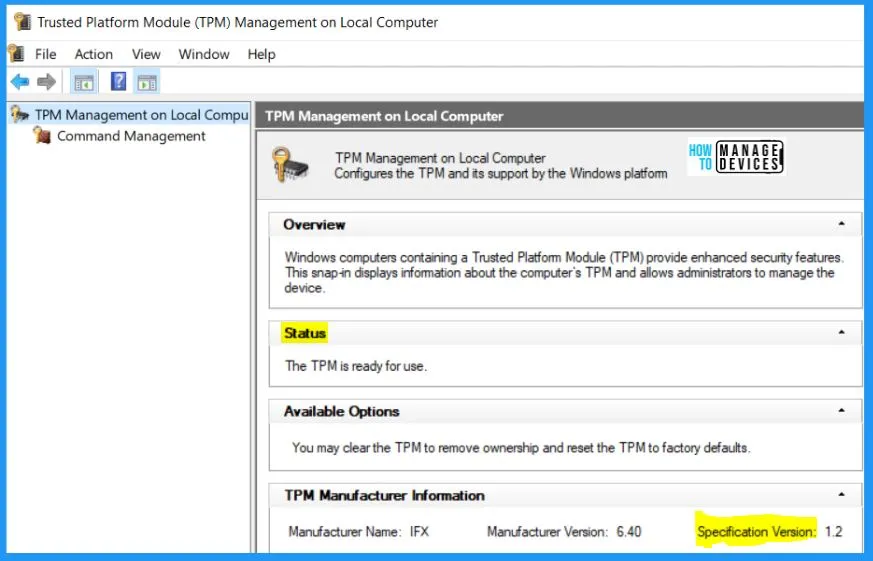
TPM Management on Local Computer
To verify if TPM 2.0 is enabled on your Windows system, you can open the “tpm.msc” application from within the Windows environment and confirm the presence of TPM 2.0.
Secure Boot and TPM
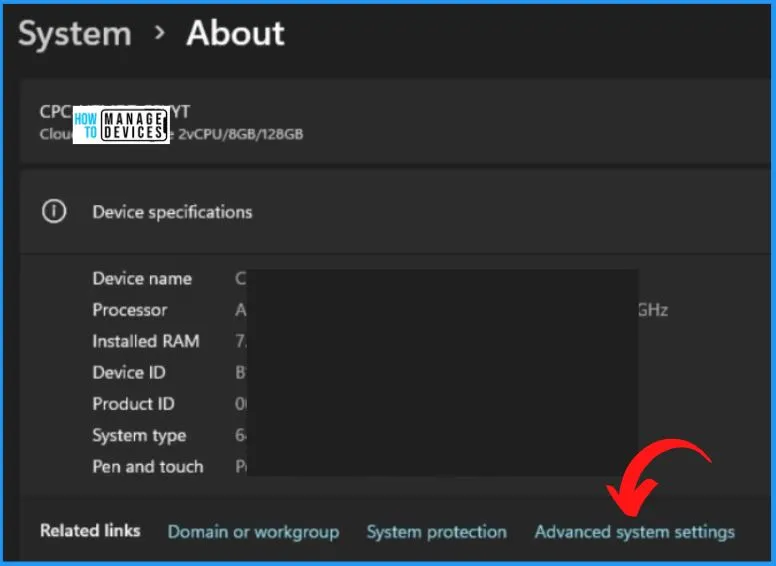
To ensure Secure Boot and TPM are on AVD VM, navigate to the Settings app, and select “Advanced system settings” under the System section. Access the system properties and click the “Settings” button. Once the performance options appear, proceed to the Advanced tab and click the “Change” button.
- Confirm that the C drive is set to “System managed” for virtual memory while all other disks are configured with “None” to optimize performance and security.
Announcing General Availability of Confidential VMs in Azure Virtual Desktop – Microsoft Community Hub
Author
About Author – Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She loves writing on Windows 11 and related technologies. She is also keen to find solutions and write about day-to-day tech problems.

