When It Comes To Zero Trust, Nobody Puts Appsec In A Corner
Zero Trust has seen an increase in adoption over the past few years — Forrester’s Security Survey, 2022, shows that 83% of global large enterprises are reporting that senior leadership has committed their organizations to the adoption of Zero Trust. Aspects of the Zero Trust model continue to be misunderstood, however.
The industry is still “dirty dancing” with this framework and struggling to find the right steps to complete a well-crafted, choreographed performance of all the key components of Zero Trust. Recall that Zero Trust is operationalized to incorporate these domains: networks, devices, people, data, workloads (applications), visibility and analytics, and automation and orchestration.
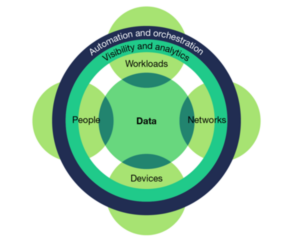
Key among these is workloads — this includes application security (appsec). It has been proselytized that appsec and Zero Trust are mutually exclusive, a concept which cannot be further from the truth.
“Workloads” is a high-level term that some security pros are unfamiliar with but that is standard for counterparts in infrastructure and operations. It refers to the entire application stack from the app layer through the hypervisor or self-contained components of processing, such as containers and virtual machines within the stack — elements that allow the workload to “do.”
A Zero Trust approach to protecting workloads in production means protecting all those application stack layers and managing the interactions between components … and the microservices and APIs that the components rely on. A robust application security architecture incorporates Zero Trust’s core principles of least privilege access and comprehensive security monitoring. Any discussion about protecting applications in production through API security, container security, or workload security will naturally include Zero Trust requirements.
While Zero Trust is about how you architect your application and surrounding environment when presuming that all entities are untrusted by default, it’s hard to ignore the fact that attackers often exploit application, dependency, and ecosystem flaws to move between components. Applications are a top cause of breaches — security leaders in enterprises breached via external attacks most often cited software supply chain breaches and software vulnerability exploits as the ways that attackers got in the door. Therefore, any robust discussion of Zero Trust must include approaches for finding and remediating those application security flaws and preventing new flaws from being introduced … and secure DevOps (DevSecOps) is the way we do it.
Application security’s role in Zero Trust isn’t new, but it hasn’t gotten as much attention in recent years as some of the other parts of the framework. If you’re considering the intersection of Zero Trust and application security, start by reviewing Forrester’s research into API security, container security, and serverless security.
Later this year, look out for new research into DevSecOps and Kubernetes security and for some deep dives into best practices around Zero Trust and application security.
