What’s Important Today In A Customer Feedback Management Vendor
Forrester IT
FEBRUARY 12, 2020
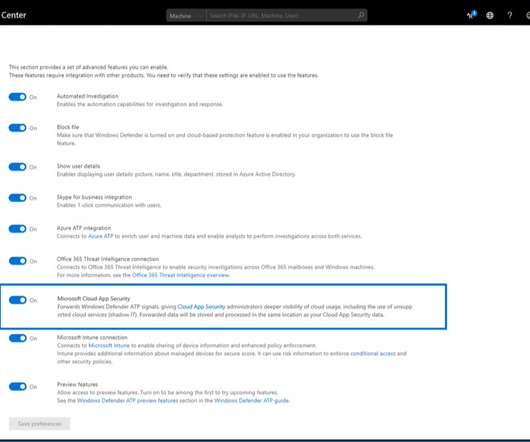
Voice-of-the-customer (VoC) technologies play a critical role in the evolution of enterprise customer experience (CX) programs, helping CX leaders focus on driving improvements that impact both the customer and the business. Unfortunately, CX leaders struggle to achieve state-of-the-art VoC programs that fully integrate data, help prioritize projects, calculate business value, inform the design process, and […].











































Let's personalize your content