TL;DR: A powerful malware capable of infecting multiple systems and CPU architectures is making strides in Europe and elsewhere. The Chaos menace spreads through Windows and Linux, and is designed to execute remotely-issued commands by cyber-criminals.
Chaos is a novel malware written in the Go programming language with pretty unique capabilities. Discovered and analyzed by Black Lotus Labs, the research arm of security company Lumen, the new threat can infect a plethora of computing platforms both on the software and hardware front. There are more than a hundred infected machines as of now, a malicious network that could be leveraged to spread other threats and malware strains as well.
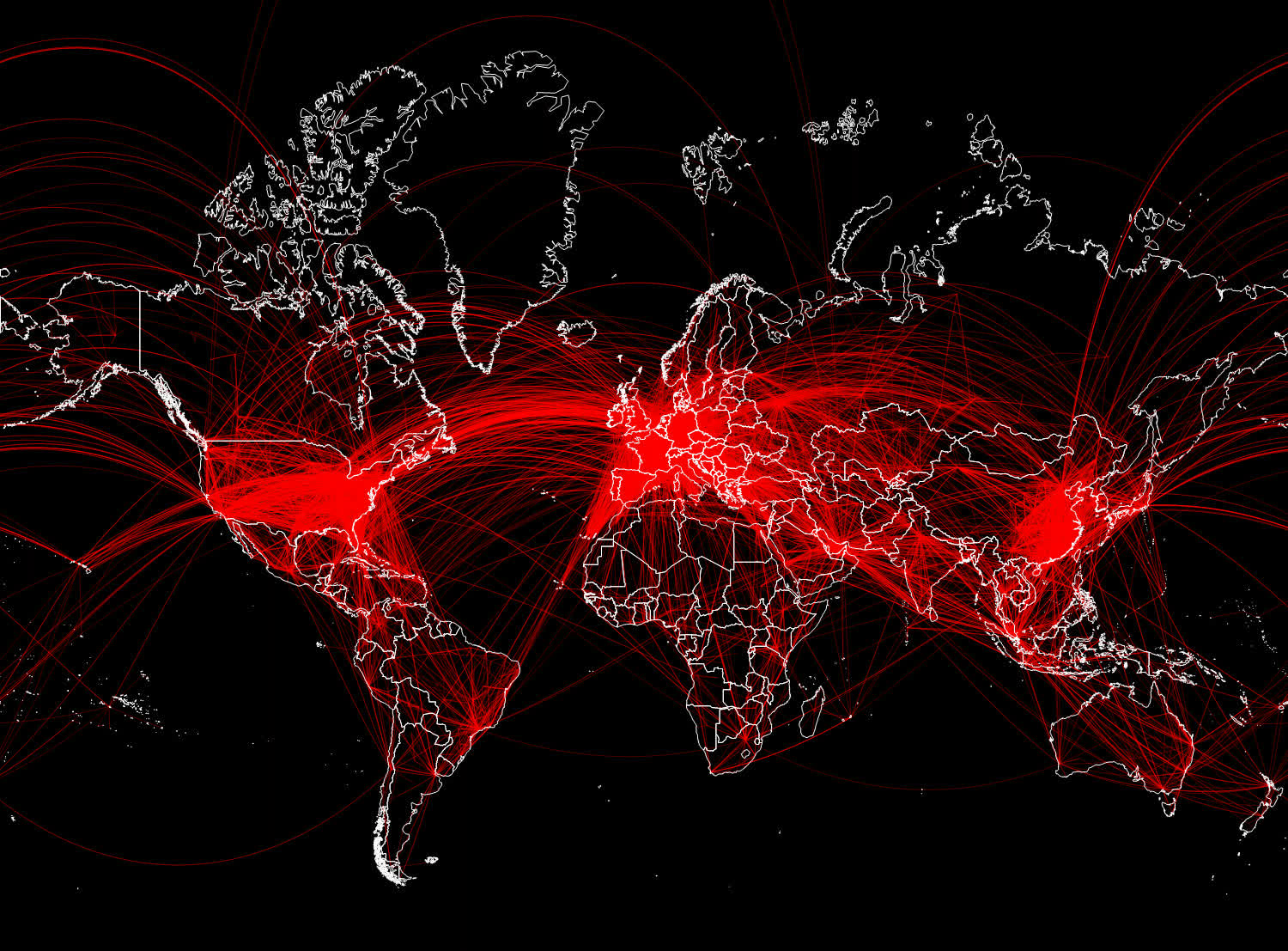
Black Lotus researchers named the new malware "Chaos" as the word has been repeatedly used in the code for function names, certificates and file names. Chaos started to emerge in April, the researchers say, and now there are more than 111 unique IPs belonging to infected devices. Chaos is a pretty flexible threat, as the aforementioned devices include standard PC units, small office routers and large enterprise boxes.
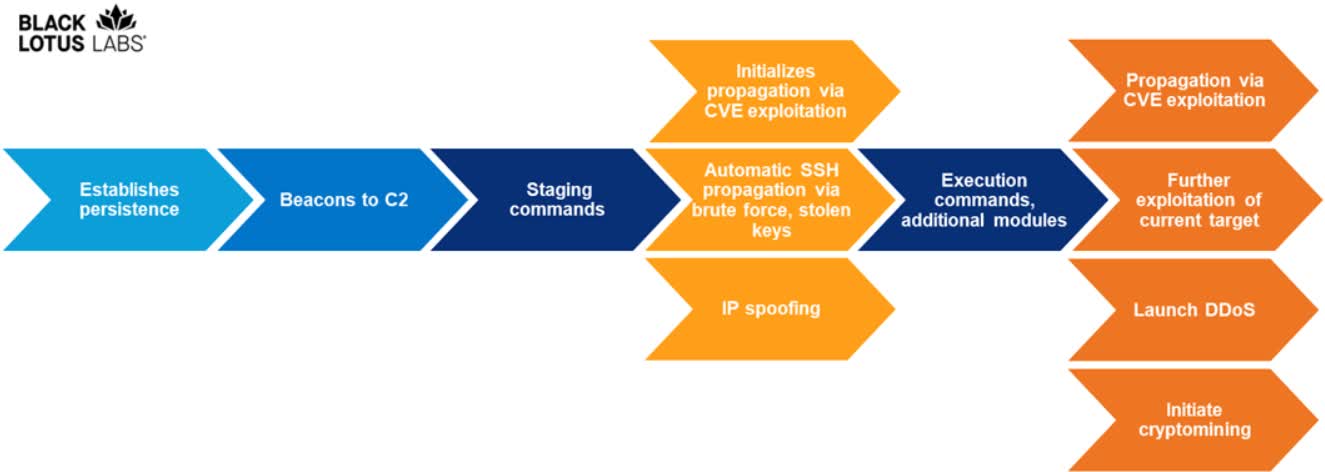
Chaos is indeed designed to run on several computing architectures, including traditional PC processors (i386), ARM, MIPS and PowerPC CPUs. On the software side, Chaos can run on Windows, Linux and FreeBSD as well. Unlike ransomware threats and botnets that employ spam campaigns to spread the infection, Chaos can spread by exploiting known CVE vulnerabilities and compromised SSH keys.
The samples analyzed by Black Lotus contained flaws affecting Huawei (CVE-2017-17215) and Zyxel (CVE-2022-30525) personal firewalls besides other, well-known CVEs. After infecting a machine, Chaos can use its various capabilities like enumerating all devices connected to a network, running remote shells to execute malicious commands and loading additional modules. According to researchers, the malware's complexity is proof that Chaos was made by a "cybercriminal actor that is cultivating a network of infected devices to leverage for initial access, DDoS attacks and crypto mining."
Black Lotus says Chaos is likely an offspring of Kaiji, a previously identified botnet targeting Linux (i386) servers for performing DDoS attacks. The malware is much more evolved now, considering its new powerful features and the ability to run on Windows and FreeBSD devices in addition to Linux. The compromised IPs identified by the security company are mostly located in Europe, with smaller infection spots in North and South America and in the Asia-Pacific region.
In concluding their analysis, the researchers suggest a few best practices to avoid being infected by a complex and dangerous threat like Chaos. Patch management for newly discovered vulnerabilities should be "effective," the authors say, while SOHO routers need regular reboot cycles (other than installing the latest firmware upgrades) as most router malware cannot survive a reboot. Furthermore, remote workers should change the default passwords and disable remote root access on machines that don't require it.