Several hacktivist groups are utilizing resources such as Telegram, Signal, and the Dark Web to help protestors in Iran who are fighting back against the government's violent response to protests across the country.
A few weeks ago, 22-year-old Mahsa Amini was arrested for "unsuitable attire" by police who enforce the Islamic Republic's strict dress code for women. She later died in police custody, sparking outrage across Iran.
Reuters reports that 83 people have died since the protests began.
Naturally, people around the world sympathize with those suffering under the regime's brutality, and hacktivists have come to help. Check Point Research reports that key activities include leaking and selling government officials' phone numbers and emails, as well as maps of "sensitive locations."
Check Point has also observed the sharing of open VPN servers for the purpose of bypassing censorship, as Iran has limited the use of internet and social media.
Telegram has been one of the most useful tools for the citizens of Iran. Researchers say users have been using the site to share lists of proxy servers. The screenshot below is from the Official Atlas Intelligence Group channel, which has approximately 900 members:
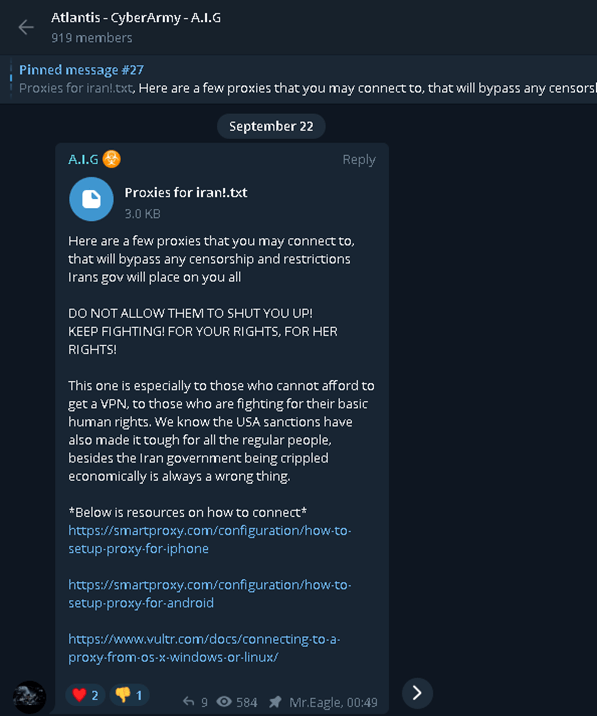
Another Telegram channel, Arvin, which has roughly 5,000 members, is sharing useful news related to the protests and internet status across Iran.
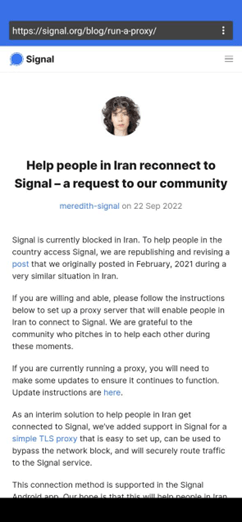
The other tool that the research highlights is Signal, which is a messaging app used to send one-on-one group messages, which can include things like files, voice notes, images, and videos.
Check Point says:
"Signal decided to also join the effort and support the protests in Iran, helping other people to setup proxy servers that can be used to bypass the censorship in Iran. https://signal.org/blog/run-a-proxy"
It shared this screenshot, as well:
Two cybersecurity experts shared their thoughts with SecureWorld News regarding the situation in Iran. Chris Vaughan, VP of Technical Account Management at Tanium, said this:
"The telecommunications sector in Iran is almost entirely state-owned, so it's not surprising that anti-government groups like this are trying to use tools such as Telegram to avoid state censorship. These apps help people get unbiased information in and out of the country so I expect that app stores may also be targeted in a bid to control communications. It's likely that the Iranian government will also be blocking VPNs in order to restrict this information flow and disrupt protestors trying to communicate with each other."
Michael DeBolt, Chief Intelligence Officer at Intel 471, discussed some trends he found interesting:
"One notable trend was uploading videos of protests and trying to collectively reveal the identity of soldiers and officers who were taking part in violent crackdowns against protestors. We observed the actor 3ackd0or and others posting such information. Many of the notable hacker group chats changed their name to 'OpIran' and were used to share information on the protests. The most common cyberattacks observed were denial of service attacks.
What's also interesting to note is how the more 'traditional' or older hacker groups in Iran, such as Bax 026 and Ashiyane, were always taking the regime's side and aligned with the regime's agenda while we see more and more groups that are actively targeting the regime and helping opposition and anti-regime protestors."
Cyber leaders warn of Iranian threat actors
Cyber authorities from the United States, Australia, Canada, and the United Kingdom released a joint cybersecurity advisory detailing how threat actors of the Iranian government's Islamic Revolutionary Guard Corps (IRGC) are exploiting vulnerabilities for data extortion and ransomware operations.
The advisory says that "Iranian government-sponsored APT actors [are] exploiting known Fortinet and Microsoft Exchange vulnerabilities to gain initial access to a broad range of targeted entities in furtherance of malicious activities, including ransom operations."
The authoring agencies shared a list of observed activity of IRGC actors:
- "In December 2021, the actors exploited ProxyShell vulnerabilities (likely CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207) on a Microsoft Exchange server to gain access to the network of a U.S. police department. The actors used their access to move laterally within the network, encrypt network devices with BitLocker, and hold the decryption keys for ransom."
- "In December 2021, the actors exploited ProxyShell vulnerabilities (likely CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207), on a Microsoft Exchange server to gain access to the network of a U.S. regional transportation company. The actors used their access to move laterally within the network, encrypt network devices with BitLocker, and hold the decryption keys for ransom. This activity disrupted the transportation company’s operations for an extended period."
- "In February 2022, the actors exploited a Log4j vulnerability (likely CVE-2021-44228, CVE2021-45046, and/or CVE-2021-45105) in a VMware Horizon application to gain access to the network of a U.S. municipal government, move laterally within the network, establish persistent access, initiate crypto-mining operations, and conduct additional malicious activity."
- "In February 2022, the actors may have exploited a Log4j vulnerability (likely CVE-2021-44228, CVE-2021-45046, and/or CVE-2021) to gain access to the network of a U.S. aerospace company. The actors leveraged a server that the authoring agencies assess is associated with the IRGC-affiliated actors to exfiltrate data from the company's network."
Read the joint cybersecurity advisory for more technical information.





