Let’s see how to block or Hide Bitlocker Recovery Key from users. Microsoft recently added support to hide recovery keys from end-users. This helps to improve the security poster of the devices and restricts an attacker from getting Bitlocker encryption keys from Windows laptops.
Let’s learn how to Enable or Disable the Self-Service Bitlocker Recovery key using MS Graph and PowerShell script. This empowers the organizations to customize the end user’s self-service options to view the Bitlocker recovery key.
This new feature provides the ability to choose whether a user can view their BitLocker Recovery Key or not. At this point, many organizations don’t have an option to disable this feature. Microsoft acknowledged the feedback from the enterprises and implemented this feature to hide Bitlocker recovery keys.
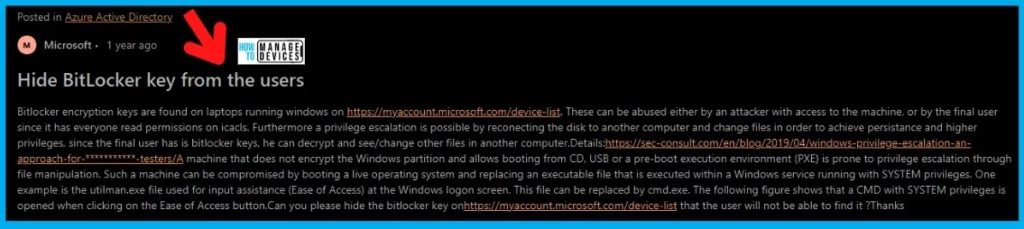
An attacker can abuse these recovery keys with access to the machine or end user since everyone has read permissions on icacls. Furthermore, a privilege escalation is possible by reconnecting the disk to another computer and changing files to achieve persistence and higher privileges.
Video Tutorial – MS Graph PATCH command to Block Bitlocker Recovery Key
Let’s check out the video tutorial on the MS Graph PATCH command to block Bitlocker Recovery Key. Use PATCH Graph API Command – Block Bitlocker Recovery Key Information from Users.
How to View BitLocker Recovery Key with Normal User Permissions
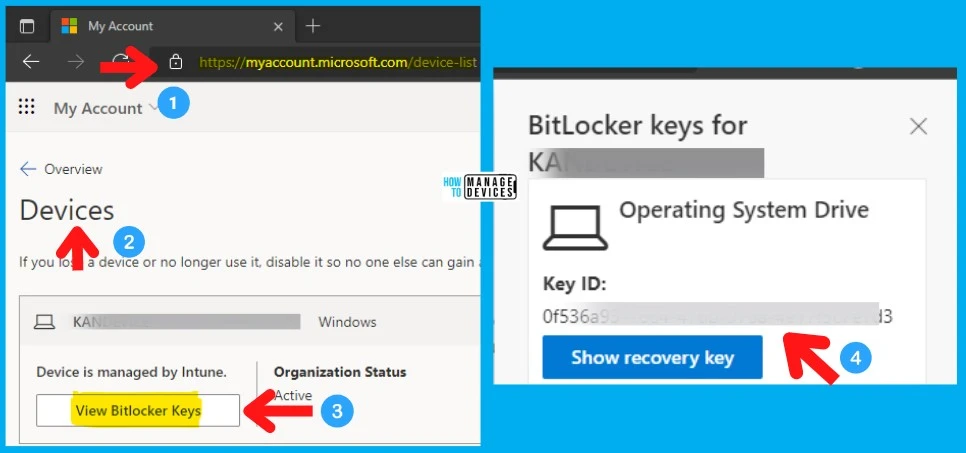
Learn how to view BitLocker Recovery Key with Normal User Permissions. End users can retrieve their recovery key by going to the following site My Apps (microsoft.com). This is the self-service method to recover the Bitlocker Recovery key with a normal user’s permission.
- Login to https://myapplications.microsoft.com/
- Navigate to the user profile.
- Select Devices (or you can click on My Account (microsoft.com)
- Select the device you want to get the BitLocker Recovery keys.
- Click on View Bitlocker Key as shown below.
Block users from viewing their BitLocker keys
Microsoft’s senior PM Quoc Lai recently announced an option to Block users from viewing their BitLocker keys. This feature is not available in the Azure portal UI yet. I’m sure this will be coming soon as a global setting.
I could see some organizations looking for granularity for this setting so that they can hide or block the Bitlocker recovery key from some of the users but not from other users. This decision could be based on a user’s or device’s security posture.
I have also noticed an interesting feature request in the Azure AD feedback forum. The AAD feedback forum thread details the security concerns related to the current implementation of Bitlocker recovery keys.
Check the Status of Permissions to view BitLocker Recovery Key
Let’s check the permissions to view BitLocker Recovery Key with normal user permissions. There is a table that I created below that is going to help you understand the Azure AD permission scenario better.
If you are new to Intune Graph API and Query, refer to MS Graph API Starters Guide. You can also refer to the following post to learn more advanced options in the Graph API world – Create Intune Policy using Graph Explorer API POST HTTP Method.
Let’s follow the steps listed below to log in to Graph Explorer with global Admin permissions (preferably) and run the Azure AD Graph API queries. I recommend using the Microsoft Edge browser to perform the following step, but other supported browsers are also fine.
With the following MS graph API query, you can check the Read permissions of BitLocker Recovery Key for end-users. The following table gives you a clear picture of Bitlocker Key read permissions and status. The
| Graph Properties | Permission on AAD | Status |
|---|---|---|
| allowedToReadBitlockerKeysForOwnedDevice”: true | Read Permission is granted to End-Users | Users can view Bitlocker Key |
| allowedToReadBitlockerKeysForOwnedDevice”: false | Read Permission is NOT granted to End-Users | Bitlocker key is blocked or hidden from End-Users |
- Open the https://developer.microsoft.com/en-us/graph/graph-explorer
- Click on the button called Sign in to Graph Explorer.
- Enter the Global admin user name and password to log in.
- Select the GET method and Beta version from the drop-down.
- Enter the following Azure AD Graph query – Request Query Address Bar
- https://graph.microsoft.com/beta/policies/authorizationPolicy/authorizationPolicy
- Click on the Run Query button
The result of the query shows the end users are allowed to view the BitLocker recovery key of their own devices (company-owned devices but assigned to the end-users)- allowedToReadBitlockerKeysForOwnedDevice”: true.
"defaultUserRolePermissions": {
"allowedToCreateApps": true,
"allowedToCreateSecurityGroups": true,
"allowedToCreateTenants": true,
"allowedToReadBitlockerKeysForOwnedDevice": true,
"allowedToReadOtherUsers": true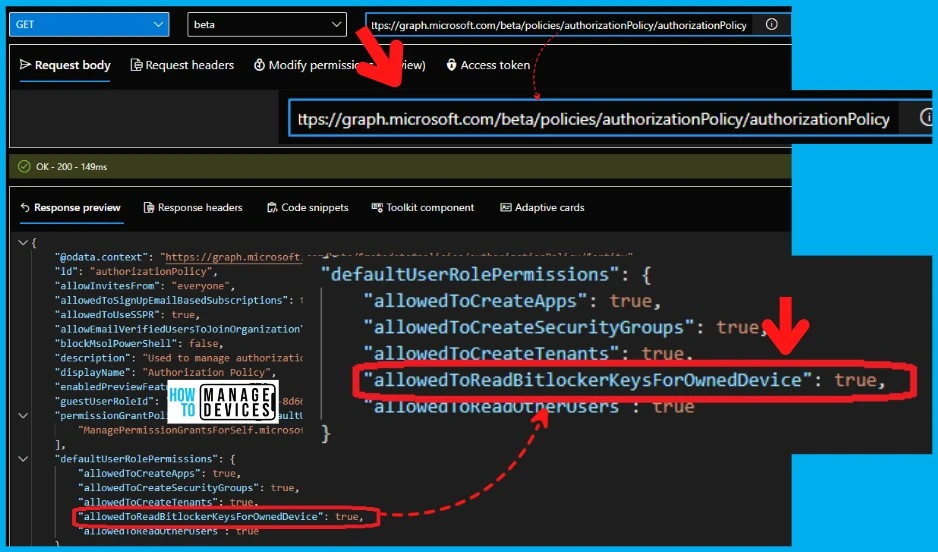
Block Hide BitLocker Recovery Key from Users using MS Graph API
Let’s see how to Block or Hide BitLocker Recovery Key from Users using MS Graph explorer. Graph API can automate many scenarios for different Microsoft 365 cloud products. You must use the PATCH function to update the existing configuration!
The following steps help to block or hide the BitLocker recovery key details from end-users. You must log in to Graph Explorer with global Admin permissions (preferably) and run the Azure AD Graph API queries.
- Open the https://developer.microsoft.com/en-us/graph/graph-explorer
- Click on the button called Sign in to Graph Explorer.
- Enter the Global admin user name and password to log in.
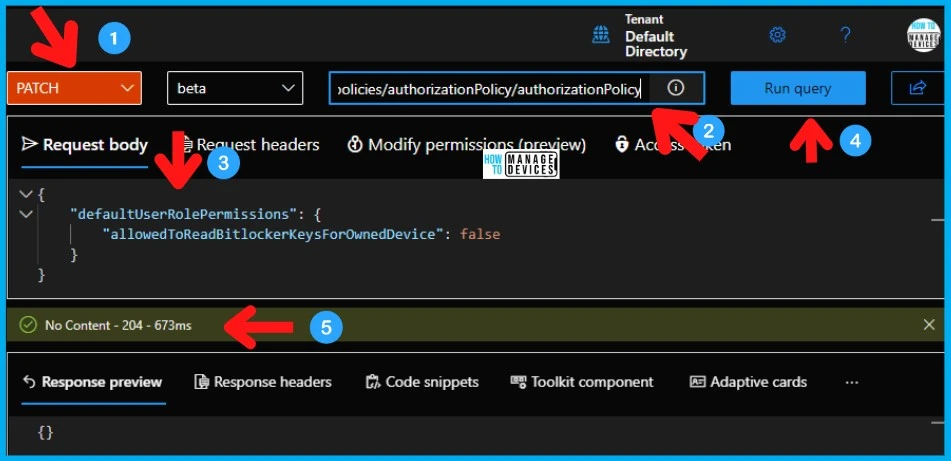
- Select the Patch method and Beta version from the drop-down.
- Enter the following Azure AD Graph query – Request Query Address Bar.
- https://graph.microsoft.com/beta/policies/authorizationPolicy/authorizationPolicy.
- Copy the following code and paste it under the Request Body section of the explorer.
- Click on the Run Query button.
Ensure that you get the “No Content – 204″ message from Graph Explorer after running the query. You can get more details from the following screenshot.
{
"defaultUserRolePermissions": {
"allowedToReadBitlockerKeysForOwnedDevice": false
}
}
Verify – Bitlocker Recovery Key Azure AD Permission
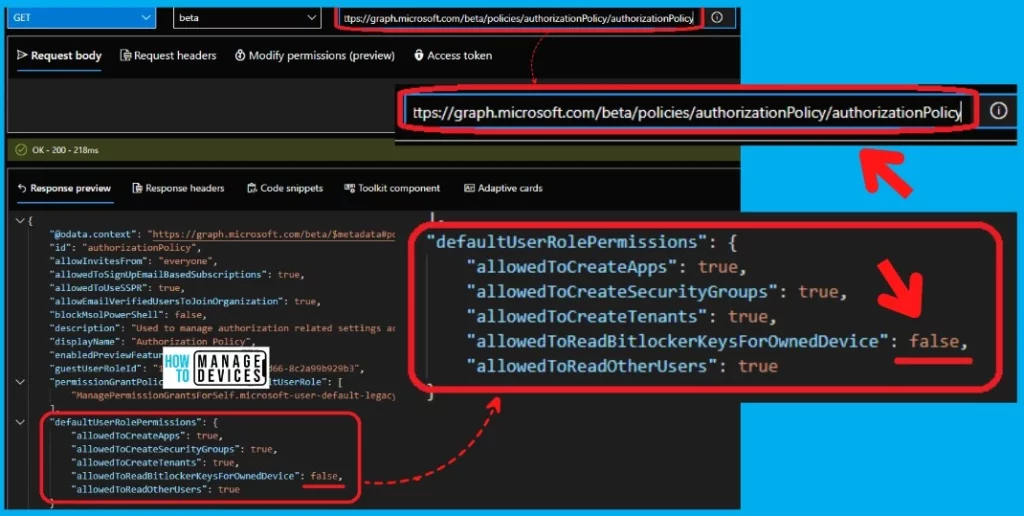
You can confirm whether block or hide Bitlocker Recovery Key permission on Azure AD is correctly applied or not by running the following MS Graph API query. This is the same query that I used in the above section.
- Enter the following Azure AD Graph query – Request Query Address Bar
- https://graph.microsoft.com/beta/policies/authorizationPolicy/authorizationPolicy
As you can see the following property value is FALSE – “allowedToReadBitlockerKeysForOwnedDevice”: false. This means the permission to view the Bitlocker Recovery key for end-users is denied!
PowerShell Script to Hide or Block BitLocker Recovery Key from Users
Let’s see the PowerShell Script to Hide or Block BitLocker Recovery Key from Users. Again the PowerShell script given below uses MS Graph API to perform all the actions.
Ensure that you created an app and give appropriate permissions to run MS Graph API automation tasks before proceeding further. Check for the App-based authentication file where you allowed the Azure AD to access the Intune APIs in Microsoft Graph.
We have a similar PowerShell script-related post, and that PS script also uses Microsoft Graph API to execute the commands – PS Script to Add or Modify Group Tag of Autopilot Devices in Intune.
Connect-MgGraph -Scopes Policy.ReadWrite.Authorization
$authPolicyUri = "https://graph.microsoft.com/beta/policies/authorizationPolicy/authorizationPolicy"
$body = @{
defaultUserRolePermissions = @{
allowedToReadBitlockerKeysForOwnedDevice = $false #Set this to $true to allow BitLocker self-service recovery
}
}| ConvertTo-Json
Invoke-MgGraphRequest -Uri $authPolicyUri -Method PATCH -Body $body
# Show current policy setting
$authPolicy = Invoke-MgGraphRequest -Uri $authPolicyUri
$authPolicy.defaultUserRolePermissions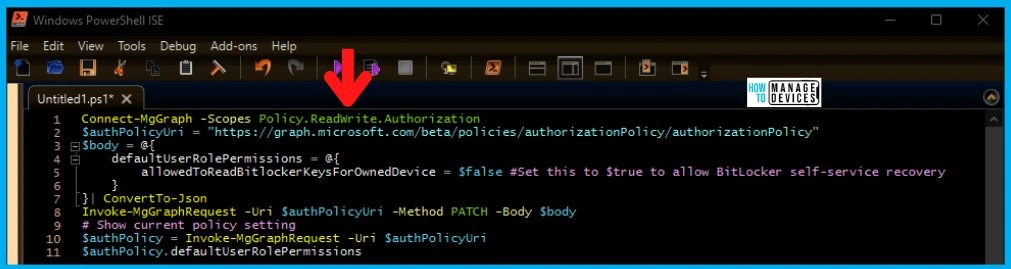
Resource -> Manage devices in Azure AD using the Azure portal – Microsoft Entra | Microsoft Docs
Author
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc.


Thanks Anoop. Does this only work for devices enrolled in Intune? Will this also work for devices simply joined to Azure AD (OOBE) or managed via another MDM but still joined to Azure AD?