No matter how different your business is, you are in CX
Forrester IT
FEBRUARY 10, 2020
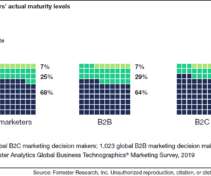
GetWhen I describe what customer experience management requires to be able to transform a CX vision into reality, I often hear from my audience: “this is interesting, but we are different“ The nature of that difference is then often stated as: we are operating in B2B, not B2C; or we operate in a heavily regulated […].








































Let's personalize your content