The Benefits of Proper Network Configuration
Association of Information Technology Professional
MAY 18, 2022
Learn how configuration tools and managers can help you properly configure your network for optimal network health, maintenance and security.






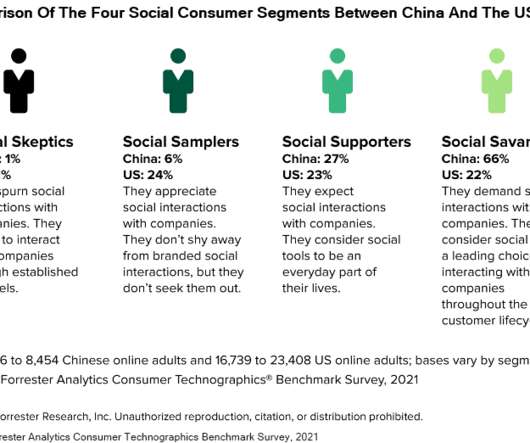






































Let's personalize your content