XDR FAQ – Frequently Asked Questions on Extended Detection and Response
Forrester IT
JULY 22, 2021
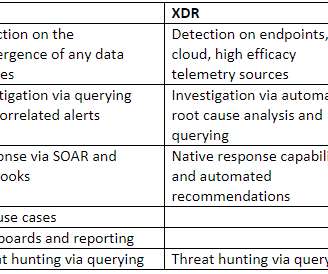
As is expected with any new market segment or capability, questions about Extended Detection & Response (XDR) abound. I wrote this blog to answer a few of the more common questions I’m getting from Forrester clients and from security vendors that are trying to figure this space out. What is XDR? An incredibly simplified way […].








































Let's personalize your content