Cybercriminals have been busy lately trying to exploit the coronavirus for their own malicious purposes. As such, the spread of COVID-19 has led to an increase in phishing emails and other malware designed to entrap people looking for information about the virus. A new type of ransomware known as CovidLock encrypts key data on an Android device and denies access to the victims unless they pay up, according to the threat intelligence firm DomainTools.
SEE: Ransomware: What IT pros need to know (free PDF) (TechRepublic)
After the first cases of the coronavirus came to light, researchers at DomainTools discovered a small rise in the number of domain names associated with Coronavirus and COVID-19. That number has since shot up the past few weeks, however, many of those domains are malicious. Monitoring the suspicious ones, DomainTools said it found one site that promises a real-time coronavirus outbreak tracker available as an Android app.
Though the app claims to offer heat map visuals and other statistical data about COVID-19, in actuality it’s a purveyor of ransomware. During installation, the app tries to convince the user to grant it administrative access by promising certain types of information. That access then gives it the opportunity to lock up all contacts, pictures, videos, and social media accounts unless the user agrees to pay the ransom in Bitcoin. If the ransom is not paid, the attacker threatens to release all private information publicly and erase the phone’s memory.
The scheme denies the user access to personal data by forcing a change in the password or PIN used to unlock the phone. Known as a screen-lock attack, this method has been found in other Android ransomware, says DomainTools.
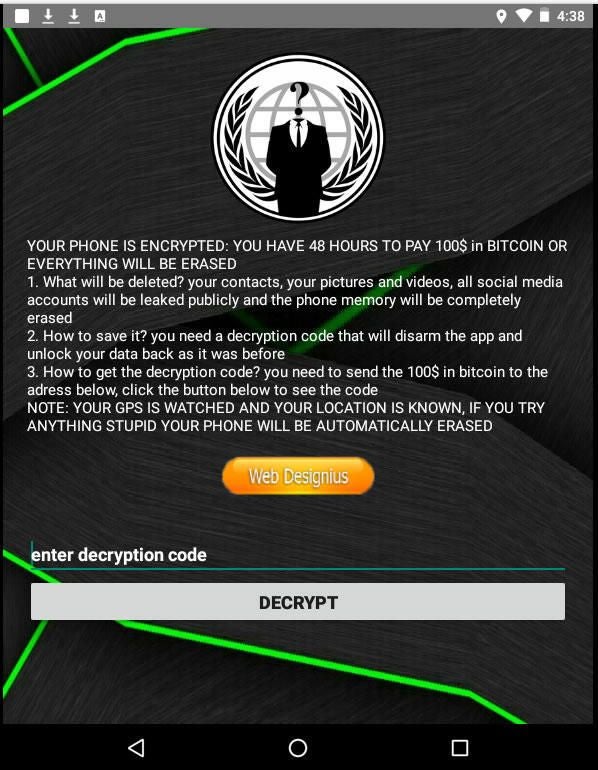
Image: DomainTools
Android 7.0 Nougat and higher do offer certain protections against this type of attack. But they work only if you’ve already set up a password to lock and unlock your device. If not, you’re still susceptible to the CovidLock ransomware, cautions DomainTools.
To protect yourself against ransomware that capitalizes on the coronavirus, DomainTools offers the following two tips:
- Be sure to only use trusted information sources from government and research institution’s websites. Don’t click on anything in your email that’s health related. In general, be sure to follow all of the basic phishing recommendations—be aware that people are trying to capitalize on fear here.
- Ensure that you download Android applications only from the Google Play store. There is a much higher risk of downloading malware from untrusted third-party stores.

Artyom Medvediev, Getty Images/iStockphoto