Who Is Responsible for a Secure, Mission-Oriented Network?
Information Week
MAY 19, 2022
This seems like a simple question, but it is a complicated one to answer.

Information Week
MAY 19, 2022
This seems like a simple question, but it is a complicated one to answer.

Information Week
MAY 19, 2022
As organizations plow ahead with digital transformation investments, forming a clear framework for measuring the success of digital investments is a critical component to any effort.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Association of Information Technology Professional
MAY 18, 2022
Learn how configuration tools and managers can help you properly configure your network for optimal network health, maintenance and security.
Forrester IT
MAY 17, 2022
Tell us about yourself: I help people seek, solicit, and speak data & information in safe to share environments. I can help data, technology, and business leaders influence culture change and ignite insight-driven decision making at their organizations. I empower those at any point in their development journey to be curious, creative, critical thinkers who […].

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Anoop
MAY 16, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Prevent Users from Download Files in Windows appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Jitesh Kumar.

Social, Agile and Transformation
MAY 19, 2022
“CIOs today are caught in between a rock and a hard place. The rock is maintaining high availability while doing that as cheaply as possible. The hard place is enabling digital transformation and increasing business and developer velocity,” answered Assaf Resnick, CEO and Co-Founder of BigPanda, at the opening session of RESOLVE ’22. Every.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Forrester IT
MAY 19, 2022
On Global Accessibility Awareness Day this year, learn what’s changed in digital accessibility over the past four years. Read more.
Anoop
MAY 16, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Create SCCM Application Deployment using PowerShell appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Dhanraj Barman.

Network World
MAY 18, 2022
The increased deployment of core business applications in the cloud and the shift to remote work brought on by the pandemic have obliterated any notion of the traditional “corporate moat” style of security. Today’s hybrid workplace, where employees are on the road, working from home and maybe visiting the office once or twice a week, has forced network and security teams to adopt a more flexible approach to managing the network, identities, and authentication.

Association of Information Technology Professional
MAY 16, 2022
Learn from an IT recruiter how to apply professional skills when managing your reputation before, during and after the hiring process

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.
Forrester IT
MAY 16, 2022
AIOps builds upon observability and monitoring to develop deep AI driven insights that enhance human judgements. As we move from monitoring to AIOps, we also move from a reactive to active, then proactive footing before establishing the predictive capabilities AIOps promises. Biomedical devices function the same way. They use the body's telemetry and then act on it before harm is done.

Anoop
MAY 17, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post 10 SCCM Proactive Monitoring Tasks appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Anoop C Nair.

Tech Republic Security
MAY 20, 2022
A commercial surveillance company previously exposed for selling a spyware service dubbed "Predator" keeps targeting users and uses 0-day exploits to compromise Android phones. Learn more about how to protect yourself from it. The post Packaged zero-day vulnerabilities on Android used for cyber surveillance attacks appeared first on TechRepublic.

Association of Information Technology Professional
MAY 17, 2022
The uptick in the use of data to solve business problems has revolutionized the MSP market. Learn more about how MSPs can modernize their data management solutions and implement strategies to maximize value.

Advertisement
You’ve read the PMBOK® Guide several times, taken the certification exam for project managers, passed, and you are now a PMP®. So why do you keep making rookie mistakes? This whitepaper shows 20 of the most common mistakes that young or inexperienced project managers make, issues that can cost significant time and money. It's a good starting point for understanding how and why many PMs get themsleves into trouble, and provides guidance on the types of issues that PMs need to understand.

Forrester IT
MAY 20, 2022
Written with Carlos Rivera, Senior Analyst. This week, the US Cybersecurity & Infrastructure Security Agency (CISA) announced an emergency directive to immediately deploy patches for five VMware products vulnerable to remote code execution or escalation of privileges to root exploits. The vulnerabilities impact VMware Workspace ONE Access (Access), Vmware Identity Manager (vIDM), Vmware vRealize Automation […].

Anoop
MAY 20, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Deploy Progressive Web App PWAs Using Intune appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Jitesh Kumar.
Kitaboo
MAY 16, 2022
The coming of age of the Internet, digital technology, and smartphones have changed the world as we know it. While evolution has always been a way of life, technological changes have revolutionized all aspects of human lives like never before and at a pace never witnessed before. And in today’s market reality, the mantra is, to evolve or perish. This also holds true for the publishing industry where several publishers are adopting e-publishing practices. .

Association of Information Technology Professional
MAY 19, 2022
The use of innovative tech solutions such as AI, blockchain, drones and IoT are transforming the way the world uses and collects data. Find out more about how companies are realizing the importance of implementing data strategies.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Forrester IT
MAY 19, 2022
Organizations looking to scale their use of AI-enhanced decision making are facing a dilemma. There is still a large gap between voluntary frameworks for responsible AI, and actionable law and enforceable regulations. I wrote about the Singapore Responsible AI governance framework in an earlier blog post. My colleague Guannan Lu has recently taken a look […].

Anoop
MAY 18, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Protect Security Settings with Tamper Protection in Windows appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Jitesh Kumar.

Network World
MAY 19, 2022
Nmap, short for Network Mapper, is a free and open source tool used for vulnerability checking, port scanning and, of course, network mapping. Despite being created back in 1997, Nmap remains the gold standard against which all other similar tools , either commercial or open source, are judged. Nmap has maintained its preeminence because of the large community of developers and coders who help to maintain and update it.

Tech Republic Security
MAY 17, 2022
NCC Group has found proof of concept that BLE devices can be exploited from anywhere on the planet. The post Vulnerabilities found in Bluetooth Low Energy gives hackers access to numerous devices appeared first on TechRepublic.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Forrester IT
MAY 19, 2022
The war on talent is affecting the tech services industry, including large SIs focused on ERP implementations like those in the SAP and Oracle ecosystems. For enterprises embarking on major DOP programs, if talent strategy isn’t already an elevated criteria in your partner selection, it should be.

Anoop
MAY 17, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Install Microsoft Teams App from Windows 11 Microsoft Store | WPM Using WinGet appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Anoop C Nair.

Information Week
MAY 19, 2022
Only a truly converged platform offers the automation, management, orchestration, and interoperability advantages that today’s -- and tomorrow’s -- hybrid networks require.

Network World
MAY 17, 2022
New Google Cloud security services aim to strengthen open-source security, simplify zero-trust adoption, and improve cloud governance.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.
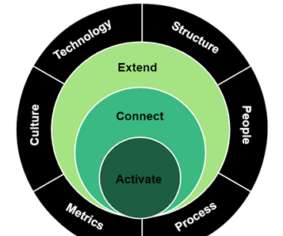
Forrester IT
MAY 19, 2022
Journey-centricity is not something you overlay on your current operating model. You cannot preserve the status quo; it will disrupt your business. It requires a bold vision to use journeys to incorporate products and services in customers’ lives, to adopt a shared journey language that aligns people, process, and technology across touchpoints, channels, and silos. […].

Anoop
MAY 19, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post FIX Microsoft Teams App Issues Repair Options Available on Windows 11 appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Anoop C Nair.

Tech Republic Security
MAY 17, 2022
Security staffers can spend more than five hours addressing security flaws that occurred during the application development cycle, says Invicti. The post Cybersecurity pros spend hours on issues that should have been prevented appeared first on TechRepublic.

Information Week
MAY 20, 2022
Quite often, the Wi-Fi link between a home user's computer and the in-home router is the culprit when hybrid network performance issues arise.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.
Let's personalize your content