10 Actionable Tips for Managing/Governing Data
Information Week
OCTOBER 17, 2022
Here is a quick look at things you can do to help govern and manage your data in the most practical sense.

Information Week
OCTOBER 17, 2022
Here is a quick look at things you can do to help govern and manage your data in the most practical sense.
IT Toolbox
OCTOBER 20, 2022
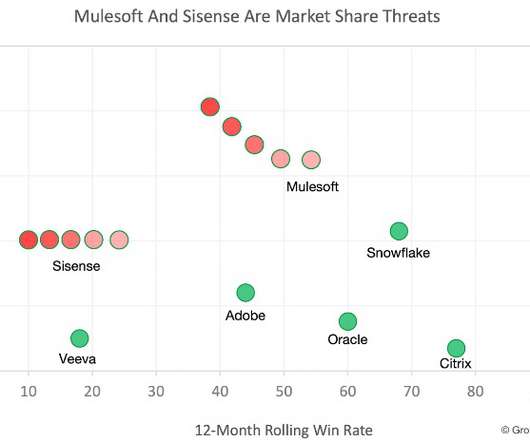
Learn from Willem Maas how poor data quality leaves you blind to competitive threats and how to develop an early warning capability against competitive attacks. The post Bad Data Is Leaving You Blind To Competitive Threats: Here’s What To Do appeared first on Spiceworks.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Association of Information Technology Professional
OCTOBER 19, 2022
Do you have a certificate or a certification? The two are quite different. Read on to learn how you (and others) can differentiate between the two.

Tech Republic Cloud
OCTOBER 19, 2022
The Oracle CloudWorld conference this week brings together developers and customers to showcase new cloud services, database services and more. The post Oracle pushes Cloud as a Service, AI/ML for data analysis appeared first on TechRepublic.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Forrester IT
OCTOBER 17, 2022
This past summer, I participated in my first century cycling ride – 110 miles through eastern Massachusetts. My goal was simple…to not be the last person across the finish line. I met my goal, almost crawling across the finish line dragging my bike behind me. As expected, my overall time was high. So, I’ve already […].

IT Toolbox
OCTOBER 19, 2022
How AI and VSaaS are combined to improve safety within the construction sector. The post How AI and VSaaS are Improving Safety in the Construction Sector appeared first on Spiceworks.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Network World
OCTOBER 18, 2022
As Cisco celebrates the 25 th anniversary of Cisco Networking Academy, the company on Tuesday announced two new certifications and a plan to provide networking, cybersecurity and general IT training to 25 million people over the next 10 years. The training will be done through the company's networking academy, an IT skills-to-jobs program that provides IT courses, learning simulators, and hands-on learning opportunities, supporting instructors and learners in 190 countries.
Forrester IT
OCTOBER 18, 2022
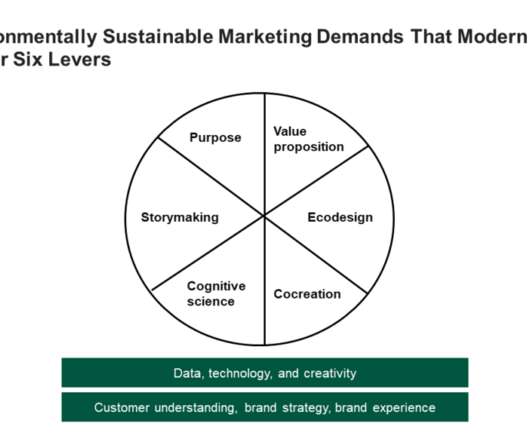
Despite the massive opportunity in today’s green market, many B2C CMOs don’t know where to start. Learn the six keys to activating sustainability in your B2C marketing and communications.

IT Toolbox
OCTOBER 20, 2022
Here’s how enterprises can evolve to implement a unified decision-making strategy. The post Leveraging AI to Embed Actionable Decision Intelligence appeared first on Spiceworks.

Information Week
OCTOBER 20, 2022
Chief financial officers need to focus on several key areas, including where the business risks and opportunities lie, prioritizing talent recruitment and retention, and digitizing operations. They’re investing in RPA, AI, and other technologies to help.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Tech Republic Cloud
OCTOBER 19, 2022
From edge expansion to green initiatives, get insight on five trends likely to shape the cloud computing industry in the next year. The post Top 5 trends to watch in cloud computing appeared first on TechRepublic.

Forrester IT
OCTOBER 18, 2022
The green market revolution gives businesses an historic opportunity for new environmentally sustainable products and services for everything. Learn more in this blog post.

IT Toolbox
OCTOBER 21, 2022
The competition regulator concluded after a three-and-a-half-year-long investigation that Google abused its dominant position in “multiple markets.”. The post Google Receives $161.9M Antitrust Fine in India, Its Largest Online Search Market appeared first on Spiceworks.

Information Week
OCTOBER 17, 2022
The metaverse does not yet fully exist but it is beginning to emerge, creating an opportunity for CIOs to prepare the enterprise now through exploring immersive experiences in the workplace.

Advertisement
You’ve read the PMBOK® Guide several times, taken the certification exam for project managers, passed, and you are now a PMP®. So why do you keep making rookie mistakes? This whitepaper shows 20 of the most common mistakes that young or inexperienced project managers make, issues that can cost significant time and money. It's a good starting point for understanding how and why many PMs get themsleves into trouble, and provides guidance on the types of issues that PMs need to understand.

Network World
OCTOBER 21, 2022
Freeman Health System has around 8,000 connected medical devices in its 30 facilities in Missouri, Oklahoma, and Kansas. Many of these devices have the potential to turn deadly at any moment. "That’s the doomsday scenario that everyone is afraid of," says Skip Rollins, the hospital chain's CIO and CISO. Rollins would love to be able to scan the devices for vulnerabilities and install security software on them to ensure that they aren't being hacked.

Forrester IT
OCTOBER 19, 2022
Create an insight-driven B2B content strategy development that aligns to the campaign implementation process. Find out more.

IT Toolbox
OCTOBER 21, 2022
AI text generation is one of those technologies that might actually prove to be disruptive, especially in the PR industry. The post The Advancement Of Disruptive PR Technology Like AI and Text Gen appeared first on Spiceworks.

Information Week
OCTOBER 21, 2022
Digital enablement introduces some important considerations, namely the need for a strategy around data interpretation. But it also unlocks untold possibilities, among them an answer to healthcare’s impending labor shortage.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Tech Republic Cloud
OCTOBER 17, 2022
Virtualization helps to make IT more flexible, agile and scalable while also making IT easier to manage and less expensive to own. The post Virtualization: Benefits, drawbacks and defining features appeared first on TechRepublic.

Tech Republic Security
OCTOBER 20, 2022
A new report from Zerto finds that only half of the companies surveyed focus on both recovery and prevention. The post Incomplete ransomware strategies still dog organizations appeared first on TechRepublic.

IT Toolbox
OCTOBER 21, 2022
The Twitter workforce could shrink to 2,000 employees, a reduction of three-quarters from its present headcount of about 7,500 people. The post Elon Musk is Reportedly Planning to Offload About 75% of Twitter Staff appeared first on Spiceworks.

Information Week
OCTOBER 19, 2022
Cyber insurance is a novel service -- and clients still don’t know what they should expect. Experts tell us what premium cyber insurance firms are offering and what you should plan on securing for yourself.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Tech Republic Cloud
OCTOBER 18, 2022
Here’s how to easily and efficiently migrate only the data you want so that you can be ready for your new iPhone 14 upgrade. The post 4 tips for preparing to migrate to a new iPhone appeared first on TechRepublic.

Tech Republic Data Center
OCTOBER 17, 2022
Hybrid cloud has become a popular computing model in recent times. Find out all you need to know, including its features, pros and cons. The post What is hybrid cloud? appeared first on TechRepublic.

IT Toolbox
OCTOBER 20, 2022
According to SOCRadar, “the amount and scale of the leaked data make it the most significant B2B data leak in the recent history of cybersecurity.”. The post Misconfigured Azure Blob Storage Exposed the Data of 65K Companies and 548K Users appeared first on Spiceworks.

Information Week
OCTOBER 19, 2022
One reason skills-based hiring has been slow to take hold is that employers, particularly in tech, don’t always understand how to put it into practice. Here are three ways to get started.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Tech Republic Cloud
OCTOBER 20, 2022
Cloud virtualization can support organizations' digital operations, but it has drawbacks. Here are some of its disadvantages and use cases. The post Disadvantages of virtualization in cloud computing appeared first on TechRepublic.

Tech Republic Data Center
OCTOBER 18, 2022
During Lenovo Tech World 2022, the company presented its new portfolio, metaverse solutions, and plans for edge, cloud and data centers. The post Lenovo Tech World 2022: Into the next phase of digital transformation appeared first on TechRepublic.

IT Toolbox
OCTOBER 20, 2022
Cybersecurity professional Bruce Schneier: “Everyone visiting Qatar for the World Cup needs to install spyware on their phone.”. The post Experts Cite Privacy Risks From Two Qatari Apps Required for FIFA World Cup Visitors appeared first on Spiceworks.

Information Week
OCTOBER 18, 2022
Here are four key dimensions that need to be addressed to build organizational digital capabilities, providing a solid foundation for long-term readiness and innovation.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.
Let's personalize your content