From the Help Desk to Systems Engineer and Still Using CompTIA A+
Association of Information Technology Professional
JANUARY 12, 2022
As a systems engineer, Girard Kavelines still goes back to the skills he learned when he got CompTIA A+.

Association of Information Technology Professional
JANUARY 12, 2022
As a systems engineer, Girard Kavelines still goes back to the skills he learned when he got CompTIA A+.
Anoop
JANUARY 13, 2022
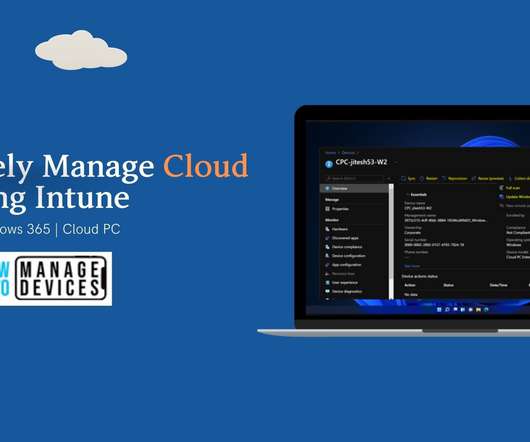
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Remotely Run Windows 365 Cloud PC Device Actions Using Intune appeared first on HTMD Blog #1 by Jitesh Kumar.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
JANUARY 11, 2022
Google took over the top spot for malicious downloads from Microsoft OneDrive as attackers created free accounts, uploaded malware and shared documents with unsuspecting users, says Netskope.

Information Week
JANUARY 12, 2022
Three technology jobs rank in the top 10 of U.S. News and World Report list of 2022 Best Jobs, evaluated on the basis of salary, work-life balance, and job outlook. Did your job make the list, and how does your salary compare to the median?

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Tech Republic Cloud
JANUARY 12, 2022
Microsoft Cloud for Retail and new features in Microsoft Teams are aimed at the 80% of workers who are usually left behind by technology.

Anoop
JANUARY 10, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Enable Audit Mode for PUA Detection in SCCM appeared first on HTMD Blog #1 by Jitesh Kumar.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Information Week
JANUARY 10, 2022
Vail Ski Resort in Colorado has created a digital twin of the mountain, complete with snowmaking infrastructure, to optimize conditions for skiers and riders, even in low-snow years.

Gizmodo
JANUARY 14, 2022
It seems we can add sexual dysfunction to the long list of unexpected and unpleasant effects of the coronavirus. Thankfully, this doesn’t appear to be a common occurrence, and there are some potential remedies that those afflicted can try. Read more.

Anoop
JANUARY 13, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post List of SCCM 2111 Known Issues and Fixes appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Security
JANUARY 10, 2022
The modern world would grind to a halt without URLs, but years of inconsistent parsing specifications have created an environment ripe for exploitation that puts countless businesses at risk.

Advertiser: GEP
The technological landscape is dynamic and changes quickly. And for procurement and supply chain leaders looking to harness the power of technology to navigate complex challenges and an uncertain business environment, keeping up with the latest trends can be its own obstacle. So, what’s on the technological horizon for procurement and supply chain for the year ahead?

Information Week
JANUARY 11, 2022
As enterprises continue to respond to the changing conditions created by the pandemic, IT will need to embrace new approaches and new technologies.

TechSpot
JANUARY 12, 2022
Nineteen-year-old IT security specialist David Columbo reported in a Twitter thread Monday and Tuesday that he gained complete control of over 25 Teslas in 13 countries without their owners knowing. He doesn’t want to disclose exactly how he did it until he reports the vulnerability to the non-profit Mitre.

Anoop
JANUARY 12, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Learn How to Share Application from SCCM Software Center appeared first on HTMD Blog #1 by Jitesh Kumar.

Tech Republic Security
JANUARY 10, 2022
As the digital landscape has grown, the organizational need for cybersecurity and data protection has risen. A new study takes a look at where CISOs stand in businesses.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Information Week
JANUARY 14, 2022
Networks are evolving from manual monitoring to automated monitoring to observability. What’s the best way to orchestrate this evolution, and what are the critical issues that IT needs to address?

The Verge
JANUARY 14, 2022
Photo by FREDERIC J. BROWN/AFP via Getty Images. Tesla has never been fantastic at meeting deadlines, so it’s not too surprising that the company’s ambitious electric pickup — the Cybertruck — is running a little late. Recently, reference to a 2022 production schedule was scrubbed from its website, and Reuters is now reporting that production of the vehicle won’t begin until the first quarter of 2023.

Anoop
JANUARY 14, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Turn Off Online Speech Recognition Using Intune MEM appeared first on HTMD Blog #1 by Jitesh Kumar.

Tech Republic Security
JANUARY 12, 2022
Though the feds don't cite any specific threat, a joint advisory from CISA, the FBI and the NSA offers advice on how to detect and mitigate cyberattacks sponsored by Russia.

Advertisement
You’ve read the PMBOK® Guide several times, taken the certification exam for project managers, passed, and you are now a PMP®. So why do you keep making rookie mistakes? This whitepaper shows 20 of the most common mistakes that young or inexperienced project managers make, issues that can cost significant time and money. It's a good starting point for understanding how and why many PMs get themsleves into trouble, and provides guidance on the types of issues that PMs need to understand.

Information Week
JANUARY 13, 2022
Business units are hiring more technology workers than IT departments are hiring. How will this impact IT budgets, CIO influence, and the future of the IT department?

Gizmodo
JANUARY 13, 2022
Deep-sea biologists were stunned to find the largest known fish breeding ground, a discovery made last year near Antarctica. Details of the incredible find were published today, with researchers describing a sprawling colony of millions of icefish on seafloor of the Southern Ocean. Read more.

Anoop
JANUARY 11, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Easily Export SCCM Application from Configuration Manager Console appeared first on HTMD Blog #1 by Jitesh Kumar.

Tech Republic Security
JANUARY 14, 2022
Some of the major obstacles center on concerns about compliance, fears about security and infrastructure and uncertainty about budget requirements, says Archive360.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Information Week
JANUARY 11, 2022
One of the greatest threats is not only the risk of losing good talent and productivity, but also the valuable knowledge that departing employees take with them.

TechSpot
JANUARY 11, 2022
Despite all the progress that has been made in the realm of technology, AI, and machine learning, weather companies have not yet handed over the keys to their computer counterparts. While AI models, with the help of weather satellites like GOES-16 and 17, are capable of predicting minor weather changes.

GeekWire
JANUARY 10, 2022
Ciara speaks at the 2021 GeekWire Summit in Seattle. (GeekWire Photo / Kevin Lisota). The news: The House of LR&C , a Seattle-based fashion house co-founded by music superstar Ciara and Seattle Seahawks quarterback Russell Wilson, plans to raise up to $50 million this year as part of a Series A investment round. Axios first reported the news. The background: The husband-wife duo helped launch the company in 2020 as a way to house their fashion brands — Good Man Brand; Human Nation; LITA by C

Tech Republic Security
JANUARY 12, 2022
The campaign was first detected in October and is using services like AWS and Azure to hide its tracks and evade detection.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Information Week
JANUARY 10, 2022
Now delivering mission-critical outcomes, these advanced capabilities have become indispensable.

The Verge
JANUARY 9, 2022
Illustration by Alex Castro / The Verge. A developer appears to have purposefully corrupted a pair of open-source libraries on GitHub and software registry npm — “ faker.js ” and “ colors.js ” — that thousands of users depend on, rendering any project that contains these libraries useless, as reported by Bleeping Computer. While it looks like color.js has been updated to a working version, faker.js still appears to be affected, but the issue can be worked around by downgrading to a previous vers

GeekWire
JANUARY 10, 2022
An artist’s rendition of an Alaska Airlines aircraft outfitted with ZeroAvia’s hydrogen electric powertrain. (Alaska Airlines and ZeroAvia Image). ZeroAvia , a green aviation company with backing from tech giants and major airlines, is building a research-and-development space north of Seattle at Everett’s Paine Field. The location is notable as the home of century-old aerospace heavyweight Boeing, as well as to fellow electric plane upstart MagniX , which moved into a new manu

Tech Republic Security
JANUARY 10, 2022
Working with clients on finding vulnerabilities within their cybersecurity frameworks. is the key part of a security manager's job. Here's how one security auditing manager gets it done.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.
Let's personalize your content