How COVID is Changing Technology Futures
Information Week
JULY 23, 2020
Accenture released its Technology Vision 2020 report in February, but then COVID hit. Here's how the pandemic is changing technology futures according to the company.

Information Week
JULY 23, 2020
Accenture released its Technology Vision 2020 report in February, but then COVID hit. Here's how the pandemic is changing technology futures according to the company.

CTOvision
JULY 23, 2020
Like so many others in the national security domain I am tracking what I can about the new US Space Force, the newest US military force. I believe their mission […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
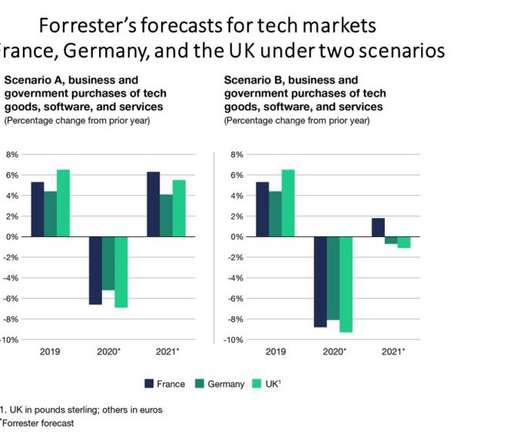
Forrester IT
JULY 22, 2020
We have just published our tech market forecast for the three largest European economies: France, Germany, and the UK (see “Tech Budget Outlooks For France, Germany, And The UK In A COVID-19 Recession“). Due to the coronavirus and resulting recessions, tech spending in Germany, France, and the UK will decline by 5% to 7% in […].

Social, Agile and Transformation
JULY 20, 2020
It's been a very challenging year for everyone and indeed, this has been the case for first responders. Somewhere a couple of rungs further down the ladder, most organizations owe plenty of thanks to CIOs, IT leaders, and especially the IT service desk. It's one compliance requirement to have business continuity plans, but an exponential challenge to quickly enable global.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Anoop
JULY 22, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s find out SCCM Application Deployment Custom Report SQL Query with Collection. I have seen many questions in HTMDForum that we want the application related reports, how to write a SQL query to write a report on app deployment etc… In this post, you will learn how to make a working Configuration Manager SQL query to find […].

CTOvision
JULY 22, 2020
Watching the cyber threat evolve over the last few decades has made it clear: we are all targets. As individuals we need to do what we can to minimize the […].
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.
Tech Republic Security
JULY 23, 2020
Beware - cybercriminals could be spending days rooting around in employee inboxes for information they can sell to other crooks, or use to mount further attacks.

Anoop
JULY 20, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s help to analyze SCCM client InActive Obsolete Status using SQL query. I keep getting questions about ConfigMgr SQL queries in the HTMD forum. The following SQL query helps you identify ConfigMgr client status based on collections. I know these details can be found in the collection.

Information Week
JULY 24, 2020
Glassdoor has ranked data science as one of the top 10 best jobs in the US every year since 2015. Here's how you can stand out in this field.

Tech Republic Cloud
JULY 24, 2020
Since October 2015, the share of Kubernetes jobs per million grew by 2,141%, while the share of Kubernetes job searches increased 2,125%.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.
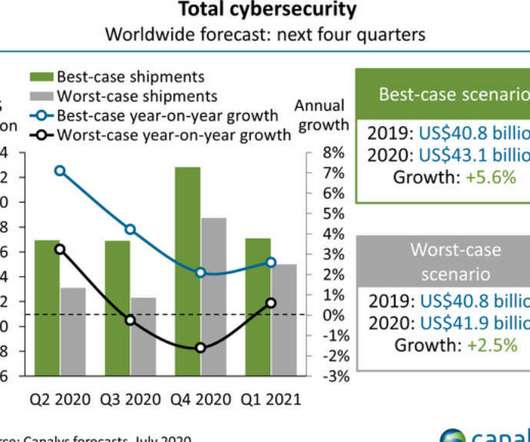
Tech Republic Security
JULY 20, 2020
Spending on security products and services for 2020 could increase as much as 5.6%, or as little as 2.5%, depending on the economic impact of the coronavirus on IT budgets, says Canalys.

Anoop
JULY 21, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Hi, My name is Ankit Shukla. This (Fix SCCM OSD Machine Domain Join Issue) is my first post, I have been Working in SCCM/MECM technology for more than 7 years. I would be sharing my experience and issues which I have faced in my IT career and posting a solution for that.

Information Week
JULY 22, 2020
Extraordinary economic conditions require brand-new analytic models, right? Not if existing predictive models are built with responsible AI. Here's how to tell.

TechSpot
JULY 24, 2020
The traditional Internet, as The Wall Street Journal points out, works by encoding data into photons of light and sending it over long distances along fiber-optic cables or wirelessly via satellites. The issue, as it relates to security, is that these communications can be intercepted along the way, resulting in.

Advertisement
You’ve read the PMBOK® Guide several times, taken the certification exam for project managers, passed, and you are now a PMP®. So why do you keep making rookie mistakes? This whitepaper shows 20 of the most common mistakes that young or inexperienced project managers make, issues that can cost significant time and money. It's a good starting point for understanding how and why many PMs get themsleves into trouble, and provides guidance on the types of issues that PMs need to understand.
Tech Republic Security
JULY 23, 2020
Malicious attacks disguised as Microsoft Office files increased 176%, according to SonicWall's midyear threat report.
Anoop
JULY 23, 2020
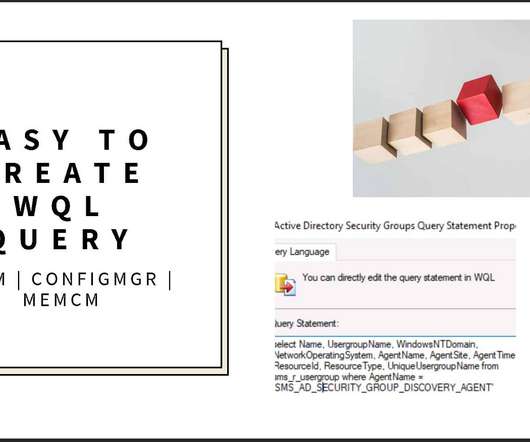
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. In today’s post, let’s find out what is the easiest way to create SCCM query to group users All Active Directory Security Groups discovery. And then you shall see how to use the WQL query to create Dynamic user Collection. ConfigMgr 2002 version has 17 out of box WQL queries available ready to use.

Gizmodo
JULY 23, 2020
Nowhere is safe from light pollution, not even space. On Wednesday, astrophotographer Daniel López shared a photo he captured of Comet NEOWISE the day before at Teide National Park on the Canary Islands. However, SpaceX’s Starlink satellites ruined the image, painting streaks across the otherwise largely pristine sky. Read more.

GeekWire
JULY 23, 2020
Washington Gov. Jay Inslee speaks at a 2018 event in Seattle. (GeekWire Photo / Monica Nickelsburg). Washington is tightening restrictions on gatherings and businesses as coronavirus cases surge across the state. “If we let the virus get even more control, it will have an even more devastating impact over the long-term in our economy and certainly in our health and the lives of our loved ones,” Washington Gov.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Tech Republic Security
JULY 21, 2020
By hosting phishing pages at a legitimate cloud service, cybercriminals try to avoid arousing suspicion, says Check Point Research.
Anoop
JULY 24, 2020
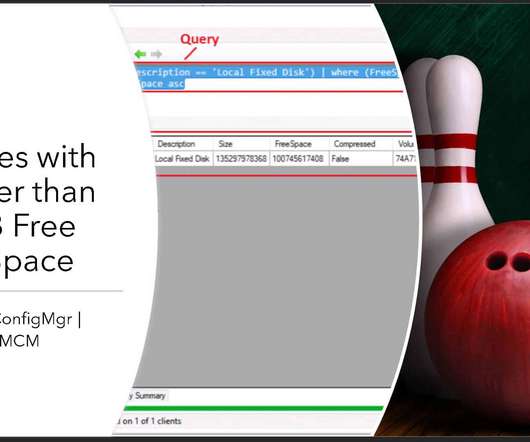
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s find out SCCM CMPivot Query to find out the Devices with Greater than 15 GB Free Disk Space. The ConfigMgr CMPivot is based on fast channel notification architecture. Configuration Manager CMPivot query tool allows us to quickly assess the state of devices.

Gizmodo
JULY 20, 2020
The U.S. is hanging on the precipice of economic collapse, with around 25 million Americans slated to be kicked off extended coronavirus pandemic uninsurance later this week and the White House mulling tax cuts and screw you as a replacement. But every cloud has an obscene silver lining: world’s richest man and … Read more.

The Verge
JULY 18, 2020
Photo by Artur Widak/NurPhoto via Getty Images. KFC is trying to create the world’s first laboratory-produced chicken nuggets, part of its “restaurant of the future” concept, the company announced. The chicken restaurant chain will work with Russian company 3D Bioprinting Solutions to develop bioprinting technology that will “print” chicken meat, using chicken cells and plant material.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Tech Republic Security
JULY 22, 2020
Phishing campaigns, deceptive domains, and malicious apps are just some of the tactics that have taken advantage of the virus and its repercussions, says Check Point Research.

TechSpot
JULY 21, 2020
Researchers at Durham University in England and Germany's Fraunhofer Institute claim that Proteus resists cutting by turning the cutting tools against themselves and dulling them. The material is made up of an aluminum matrix (aluminum foam) embedded with ceramic spheres. It is 15-percent less dense than steel making it ideal.

GeekWire
JULY 18, 2020
Shariq Siddiqui (left) and Umer Sadiq, co-founders of Veeve, with their AI-powered smart grocery cart at the GroceryShop conference in Las Vegas in September 2019. (Veeve Photo). With combined experience of nearly two decades at Amazon, startup founders Shariq Siddiqui and Umer Sadiq remain big believers in the tech giant’s mantra of obsessing about customers, not competitors.

The Verge
JULY 20, 2020
Photo by Brian Stukes / Getty Images. The deal was worth seven figures Logic doesn’t like the internet — specifically social media: the masses who send hateful messages about him, the unmoderated horde of people who feel empowered to say “go kill yourself” to someone they deem big enough to be faceless. And Logic, better known offstage as Sir Robert Bryson Hall II, isn’t a stranger to the churn of comments that power social media; it’s how he made his name, he tells me, reaching people where the

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Tech Republic Security
JULY 23, 2020
The shadow IT genie is out of the bottle and offers benefits and threats. Learn some tips from the experts on how to effectively harness shadow IT in your company.

Gizmodo
JULY 24, 2020
The coronavirus took over the world and cratered the economy, leaving governments to pick up the pieces. In the case of the U.S. government, it awarded billions of dollars to the fossil fuel industry, billions that could’ve instead gone to people in financial trouble across the country. Read more.

GeekWire
JULY 20, 2020
Seattle City Hall. (Flickr Photo / Daniel X. O’Neil). The City of Seattle launched a new program this week designed to provide necessary technology to people of color and other marginalized groups who are looking for jobs. The Digital Bridge program, developed in response to the coronavirus crisis, is designed to provide internet access and other essential tools to Seattle residents looking for work through the Seattle Jobs Initiative (SJI).

The Verge
JULY 24, 2020
Microsoft Teams at NBA arenas. | Microsoft. The National Basketball Association (NBA) is using Microsoft Teams’ new Together Mode to place basketball fans courtside in a virtual experience during live games. Microsoft only just revealed Together Mode for Teams earlier this month , and it uses AI to segment your face and shoulders and place you together with other people in a virtual space.

Advertisement
Outdated or absent analytics won’t cut it in today’s data-driven applications – not for your end users, your development team, or your business. That’s what drove the five companies in this e-book to change their approach to analytics. Download this e-book to learn about the unique problems each company faced and how they achieved huge returns beyond expectation by embedding analytics into applications.
Let's personalize your content