10 IT Trends to Watch for in 2021
Information Week
DECEMBER 22, 2020
Here's how the dramatic events of 2020 are likely to shape enterprise IT teams in the coming year, according to analysts from firms like Gartner, IDC, and Forrester.

Information Week
DECEMBER 22, 2020
Here's how the dramatic events of 2020 are likely to shape enterprise IT teams in the coming year, according to analysts from firms like Gartner, IDC, and Forrester.

The Verge
DECEMBER 21, 2020
Illustration by Alex Castro / The Verge. Apple once again appears to be seriously looking at making a car. Reuters reports that Apple is pursuing production of a passenger vehicle by 2024 as well as the creation of self-driving systems and a “breakthrough battery technology.” The report is vague on how it all comes together — it’s not clear that all of this tech is going into the first passenger vehicle Apple hopes to make — but it indicates that Apple is considering vehicle production, after pr
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
DECEMBER 21, 2020
TechRepublic spoke with dozens of experts who said the influx of companies interested in doing more with their data is only increasing.

Forrester IT
DECEMBER 22, 2020
(Written with Benjamin Corey, senior research associate at Forrester) Telehealth (virtual care) usage has skyrocketed during the pandemic. When you roll back the tape a few months, healthcare providers were able to (very quickly) stand up virtual care capabilities without having to go through the intensive HIPAA compliance protocols required in the healthcare industry.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

CTOvision
DECEMBER 23, 2020
A Matt Devost post on Putin’s OODA Loop has stood the test of time. I was reminded of that when I noticed many friends were emailing and tweeting each other […].

Association of Information Technology Professional
DECEMBER 22, 2020
As the dust settles on the Solar Winds Orion cyberattack, it's clear that the IT industry needs to take the next step and band together, sharing threat intelligence and cyber best practices to avoid similar hacks in the future.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Forrester IT
DECEMBER 21, 2020
What are the best ways to spend your paid media budget in the new year? Here are 10 ideas you can explore, test, or implement depending on your organization’s level of paid media emphasis and sophistication.

Information Week
DECEMBER 22, 2020
Artificial intelligence and automation were key tools in the IT enterprises' pandemic war effort in 2020. Here's how they will continue to change the game in every organization in 2021.

Tech Republic Security
DECEMBER 21, 2020
If you want to improve or expand your current skill set, there are a few options you can focus on. Tom Merritt lists five tech skills to master in the coming year.

Anoop
DECEMBER 23, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s learn to Install ConfigMgr SSRS Reporting Services Point. We can make beautiful reports with the data collected by the Configuration Manager. SCCM has 500+ default reports those are available out of the box and ready to use. Before you can view or manage reports from the admin console, you need a reporting services point.

Advertiser: GEP
The technological landscape is dynamic and changes quickly. And for procurement and supply chain leaders looking to harness the power of technology to navigate complex challenges and an uncertain business environment, keeping up with the latest trends can be its own obstacle. So, what’s on the technological horizon for procurement and supply chain for the year ahead?

Forrester IT
DECEMBER 21, 2020
Back in March, Nick Barber and I teamed up to help B2B marketers assess whether virtual events were a viable alternative to physical, as COVID-19 forced event managers to cancel in–person events wholesale. More than six months later, we now see virtual decisions stretching into 2021 as more B2B marketers evaluate how much of a role digital events will play in their marketing strategy.

Information Week
DECEMBER 22, 2020
Artificial intelligence and automation were key tools in the IT enterprises' pandemic war effort in 2020. Here's how they will continue to change the game in every organization in 2021.

Tech Republic Security
DECEMBER 23, 2020
Jack Wallen takes one more opportunity to remind Android device owners to use those phones with a great deal of caution; otherwise, they could become victims of malware.

Network World
DECEMBER 23, 2020
The SolarWinds Orion security breach is unfolding at a rapid pace, and the number of vendors and victims continues to grow. Each day brings new revelations as to its reach and depth. Of particular concern are the rate of infection and impact on government systems. In case you missed it, a backdoor was found in the SolarWinds Orion IT monitoring and management software.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.
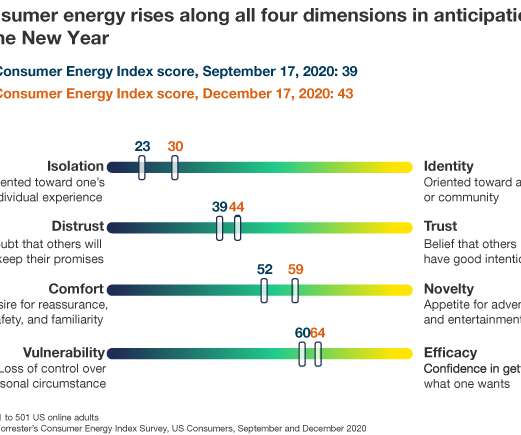
Forrester IT
DECEMBER 22, 2020
Since the onset of the COVID-19 pandemic in the US in March, we’ve been tracking precisely how the pandemic and related crises have taken an emotional toll on consumers by applying Forrester’s Consumer Energy Index, our data-driven framework that captures how ready and willing consumers are to reach out to brands. Conditions during the first […].

Information Week
DECEMBER 23, 2020
CIOs and IT organizations rose to meet tremendous challenges driven by a 100-year pandemic and how it has reshaped the world. Here are the lessons they are taking into 2021.
Anoop
DECEMBER 21, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s see how to fix Report Server cannot Open a Connection to the Report Server Database Error. Configuration Manager has rich capabilities to collect lots of information from endpoints. Once collected this information is stored in the ConfigMgr SQL DB and retrieved through SSRS reports.

Tech Republic Security
DECEMBER 24, 2020
Cybercriminals sometimes use AI to their benefit. In order to defeat these cyber bad guys, security pros and AI should focus on what they do best.

Advertisement
You’ve read the PMBOK® Guide several times, taken the certification exam for project managers, passed, and you are now a PMP®. So why do you keep making rookie mistakes? This whitepaper shows 20 of the most common mistakes that young or inexperienced project managers make, issues that can cost significant time and money. It's a good starting point for understanding how and why many PMs get themsleves into trouble, and provides guidance on the types of issues that PMs need to understand.

Network World
DECEMBER 23, 2020
The SolarWinds Orion security breach is unfolding at a rapid pace and the number of vendors and victims continues to grow. Each day brings new revelations as to its reach and depth. Of particular concern is the rate of infection and impact on government systems. In case you missed it, a backdoor was found in the SolarWinds Orion IT monitoring and management software.

Information Week
DECEMBER 23, 2020
Enterprise IT leaders no longer always need to follow the build-it-yourself path to AI. Here's how the market will shape up in the future.

Anoop
DECEMBER 22, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s have a quick look at New Hotfix Available for ConfigMgr 2010. Microsoft released the new SCCM 2010 Hotfix KB4594176 to Fix nine(9) known issue. This hotfix is applicable to all the environments that are installed during the opt-in version release. This hotfix is needed if you update ConfigMgr 2010 using an opt-in PowerShell script.

Tech Republic Security
DECEMBER 21, 2020
With cybersecurity issues, it's especially important that users understand the information provided by IT and leadership. Here are tips on dealing with the "curse of knowledge.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Network World
DECEMBER 23, 2020
The marriage of networking and security into the secure-access service edge stands to improve application performance, reduce infrastructure complexity, and protect sensitive data, and as such SASE is an attractive architecture for enterprises large and small. Due to the newness of SASE offerings, though, providers are still building and refining the features of their services, so available offerings are complex, often incomplete and require integration with customer organizations’ existing netw

Information Week
DECEMBER 22, 2020
There's considerable value in standing on the shoulders of the giants in industry who have learned from several decades of experiments in manufacturing.

The Verge
DECEMBER 25, 2020
Illustration by Alex Castro / The Verge. Tesla’s new holiday update will finally give people the ability to use a new Boombox mode, which can broadcast custom audio on the outside of the car (hence the name). As is common with new Tesla features, Boombox combines real utility with lowbrow humor: owners can use fart and goat sounds in lieu of normal, boring honking sounds car horns usually make.

Tech Republic Security
DECEMBER 25, 2020
Artificial intelligence will likely help with cybersecurity, though figuring out how to handle ambiguous situations is critical.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

GeekWire
DECEMBER 23, 2020
GeekWire Illustration / Canva Image. [Editor’s Note: Independent security consultant Christopher Budd worked previously in Microsoft’s Security Response Center for 10 years.]. Analysis: To understand where the SolarWinds attackers are going next, and how to defend against them, look to the clouds. The SolarWinds supply chain attacks are unprecedented in many ways.

Information Week
DECEMBER 21, 2020
Whether we are prepared or not, there will be a global shift toward strict data privacy rules in the coming year.
The Verge
DECEMBER 23, 2020
Today I learned that the iPhone’s built-in calculator app has a scientific mode — and all you have to do to access it is turn your phone on its side. If you’re the type of person who keeps your phone permanently in portrait lock (like me), this might come as a surprise to you, as it did to many of us here at The Verge. that glimpse of an alternate universe vibe when you turn your iPhone sideways and all of a sudden it’s a scientific calculator pic.twitter.com/PNxLVpXRAS — J.R.

Tech Republic Security
DECEMBER 22, 2020
Experts offer insights about the legal and financial hits, as well as the devastating loss of reputation, your business might suffer if it is the victim of a data breach.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.
Let's personalize your content