Data-wiping cyberattacks have grown in popularity in recent years, as some threat actors have found motivations for attacks outside of financial incentives.
Security researchers from Kaspersky have discovered a previously unidentified data wiper, which they have named CryWiper, that was used to attack Russian government agencies, including mayors' offices and courts.
A report from Kaspersky says that CryWiper disguises itself as ransomware so that it can extort money from the victim for decrypting the data, but in reality, it intentionally destroys data in the affected systems. Analysis of the wiper's code shows that this was not a mistake but the developer's original intent.
Kaspersky provides some technical details of CryWiper:
"The CryWiper sample that came to us is a 64-bit executable file for Windows OS. The malware was developed in C++ and compiled using the MinGW-w64 toolkit and the GCC compiler. This is not the most common approach among C/C++ malware developers for Windows - the Microsoft Visual Studio development environment is more often used for such purposes.
Building with MinGW is advisable either when developing a cross-platform application for different operating systems (for example, under Windows, Linux and / or FreeBSD), or if the developer himself uses something other than Windows as the main OS. Note that in the case of CryWiper, the first option is unlikely, since the Trojan uses many calls to WinAPI functions."
After starting the wiper, it creates scheduled tasks to run every five minutes:
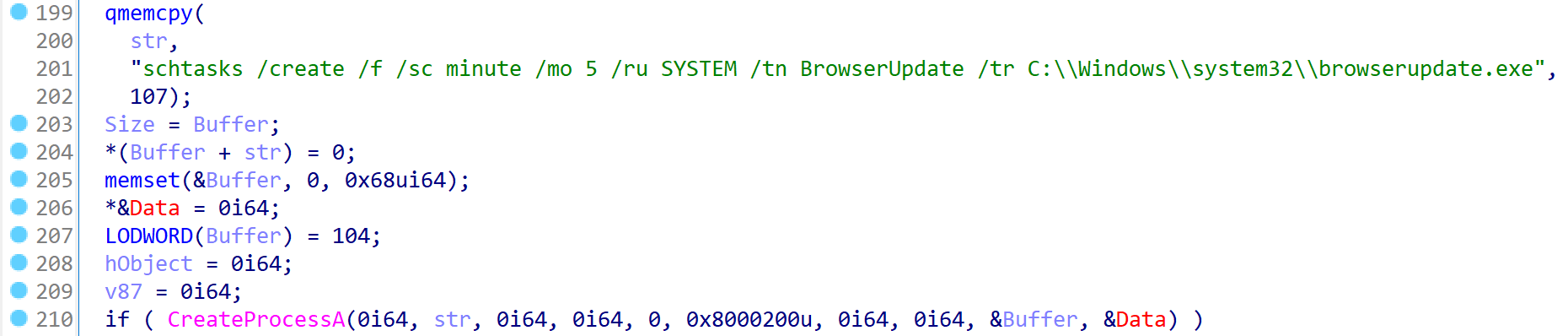
It then contacts the command and control (C2) server with the name of the compromised device as a parameter. The C2 then responds with a "run" or "do not run," determining if the wiper will activate.
Researchers note that the execution is delayed by four days (345,600 seconds), though the code "is written in such a way that the malware will under no circumstances wait for the specified time and will simply terminate execution if it has not received the run command."
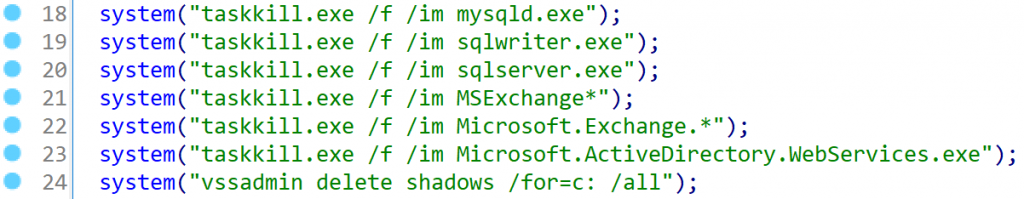
Once it does receive a "run" response, CryWiper will stop processes related to the operation of MySQL and MS SQL database servers, MS Exchange mail server, and MS Active Directory web services. Doing so ensures the wiper will have access to files that would be occupied by these processes if they were normal.
Here is the code that shows the stopping process and then deleting shadow copies:
The report also says that CryWiper modifies the Windows Registry to prevent remote desktop protocol (RDP) connections in an effort to make it difficult for security and IT specialists responding to the incident.
When actually destroying the data, the wiper "generates a sequence of data using the well-known pseudo-random number generator 'Mersenne Vortex' and writes this data instead of the original file content."
CryWiper will destroy all files, except for those with extensions ".exe", ".dll", "lnk", ".sys", ".msi", and ".CRY", which is its own extension. It will also ignore Windows, System, and Boot directories so that the victim's computer still works to an extent.
It then generates this ransom note, which asks for payment of 0.5 Bitcoin, (approximately $8,400 USD):
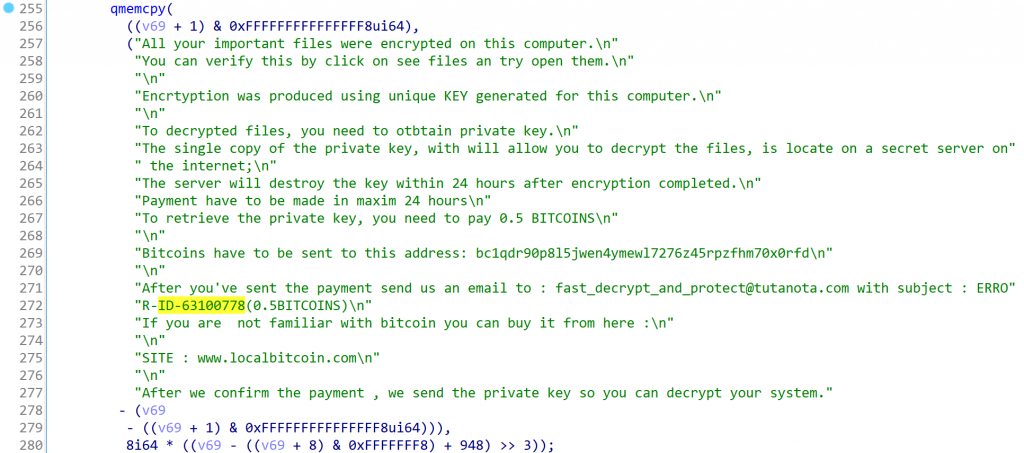
Kaspersky researchers make it clear that CryWiper is a new malware not related to existing families of wipers.
Read the original report, New Trojan CryWiper pretends to be a ransomware, for more information.
And follow SecureWorld News for more stories related to cybersecurity.





