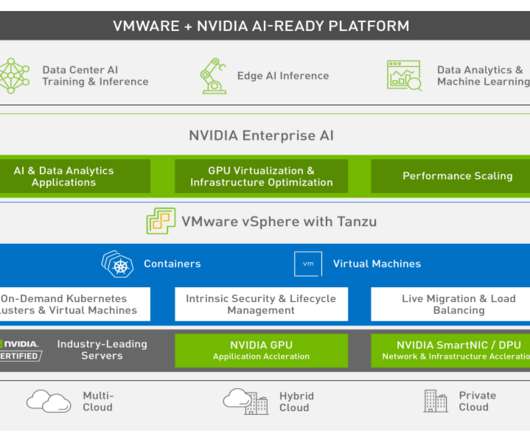
What Is Network Function Virtualization (NFV)? Meaning, Working, and Importance
IT Toolbox
DECEMBER 5, 2022
In network function virtualization, network functions powered by hardware are replaced with software. The post What Is Network Function Virtualization (NFV)? Meaning, Working, and Importance appeared first on.














































Let's personalize your content