United States government agencies recently released a joint Cybersecurity Advisory (CSA) providing information on how North Korean state-sponsored threat actors are actively using Maui ransomware to attack healthcare organizations.
The FBI says that since May 2021, North Korea threat actors have used Maui to encrypt servers responsible for healthcare services, such as electronic health records services, diagnostics services, imaging services, and intranet services.
It adds that these perpetrators are likely targeting the healthcare sector because they assume the organizations would be willing to pay the ransom, as they provide critical services and can ill afford any downtime.
The advisory reminds organizations that the U.S. government "highly discourages" paying ransoms, since it does not guarantee files and records will be recovered and may pose additional risks.
What is Maui ransomware?
While large and active Ransomware-as-a-Service (RaaS) gangs like Conti, LockBit, and BlackCat always make headlines with their operations, it's important to learn about smaller ransomware families, as they can provide insight and help us understand more about cybercrime gangs as a whole.
Silas Cutler, Principal Reverse Engineer at security firm Stairwell, authored a report detailing Maui and what his team uncovered about the lesser-known ransomware variant. The report was published on June 7, 2022.
The Stairwell research team says that Maui "stood out" because it lacked some basic components commonly seen in other ransomware strains. Things such as an embedded ransom note with recovery instructions or an automated way of transmitting encryption keys to attackers were absent in Maui.
It is because of this that researchers think Maui is manually operated, meaning the threat actor(s) is specifically choosing what files to encrypt and then exfiltrating the results.
Silas provides a technical overview of Maui ransomware:
"The earliest identified copy of Maui was first collected by Stairwell's inception platform on 3 April 2022. All identified copies of Maui (as of this report) have shared a compilation timestamp of 15 April 2021 04:36:00 UTC. Based on overlapping compilation timestamps and error messages, it is believed that Maui is configured using an unidentified external builder.
Maui is believed to be designed for manual execution by attackers. When executed at the command line without any arguments, Maui prints usage information, detailing supported command-line parameters. The only required argument is a folder path, which Maui will parse and encrypt identified files."
The figure below shows Maui command line usage details:
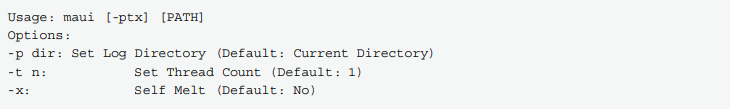
The report continues:
"Embedded usage instructions and the assessed use of a builder is common when there is an operational separation between developers and users of a malware family. The Stairwell research team has not identified any public offerings for Maui and assesses that it is likely privately developed."
For more technical information, please see the report from Stairwell.
Using manually operated ransomware
So, why would a cybercriminal use manually operated ransomware? It would seemingly be easy to fork over the crypto to use a popular RaaS. Tim McGuffin, Director of Adversarial Engineering at LARES Consulting, discusses the benefits to manual ransomware:
"This is still fairly rare, however, it's a good method to bypass modern Endpoint Protection and Canary files that would alert and kill automated, system-wide ransomware.
By targeting specific files, the attackers get to choose what is sensitive and what to exfiltrate in a much more tactical fashion when compared to a 'spray-and-pray' ransomware. This can show "good faith" from the ransomware group by allowing targeting and recovery of just sensitive files and not having to rebuild the entire server if the Operating System files are encrypted as well.
This 100% provides a stealth and surgical approach to ransomware, preventing defenders from alerting on automated ransomware, making it more difficult to use timing or behavior-based approaches to detection or response.
On the plus side, manual execution allows mature defense teams the ability to respond before the entire environment is encrypted, and allows for recovery from backups for specific folders instead of rebuilding the systems or environment from the ground up."
What is North Korea up to?
It is no secret that countries like North Korea and China have relied upon stealing trade secrets from other countries and organizations to develop their technologies in the last few decades. With the way that organizations have adapted to remote work in the last two years, it has become much easier for threat actors to access that sensitive data.
With the benefits McGuffin discussed when it comes to using manually operated ransomware, it's no surprise to see North Korea using it.
Aaron Turner, CTO at Vectra, shares his thoughts on Maui:
"This Maui campaign is interesting in that a ransomware campaign is being selective, however, if North Korea is really involved, then it is conceivable that the ransomware activities are only an after-thought for when attackers have exfiltrated the selected data that they want before initiating the encryption of files to block access.
In my opinion, this use of operator-driven selective encryption is most likely an indicator that the Maui campaign is not just a ransomware activity, but most likely a combination of intellectual property theft / industrial espionage combined with opportunistic monetization activities through ransomware."
Mitigations for Maui ransomware
If you work for a healthcare organization, or really any organization in critical infrastructure, it's important to take these warnings from the government seriously. It can be tiresome to continually hear about a new threat from North Korea, or China, or Russia, and it's easy to say "Oh, this probably won't happen to me." But in some cases, ransomware attacks can become life threatening under the right circumstances.
Nobody wants to be part of the organization that got hacked because they simply forgot to update their software.
For Maui ransomware specifically, the CSA provides a list of mitigations:
- "Limit access to data by deploying public key infrastructure and digital certificates to authenticate connections with the network, Internet of Things (IoT) medical devices, and the electronic health record system, as well as to ensure data packages are not manipulated while in transit from man-in-the-middle attacks."
- "Use standard user accounts on internal systems instead of administrative accounts, which allow for overarching administrative system privileges and do not ensure least privilege."
- "Turn off network device management interfaces such as Telnet, SSH, Winbox, and HTTP for wide area networks (WANs) and secure with strong passwords and encryption when enabled."
- "Secure personal identifiable information (PII)/patient health information (PHI) at collection points and encrypt the data at rest and in transit by using technologies such as Transport Layer Security (TPS). Only store personal patient data on internal systems that are protected by firewalls, and ensure extensive backups are available if data is ever compromised."
- "Protect stored data by masking the permanent account number (PAN) when it is displayed and rendering it unreadable when it is stored—through cryptography, for example."
- "Secure the collection, storage, and processing practices for PII and PHI, per regulations such as the Health Insurance Portability and Accountability Act of 1996 (HIPAA). Implementing HIPAA security measures can prevent the introduction of malware on the system."
- "Implement and enforce multi-layer network segmentation with the most critical communications and data resting on the most secure and reliable layer."
- "Use monitoring tools to observe whether IoT devices are behaving erratically due to a compromise."
- "Create and regularly review internal policies that regulate the collection, storage, access, and monitoring of PII/PHI."
Follow SecureWorld News for the latest stories involving cybersecurity.





