The United States Department of Health and Human Services' (HHS) security team (the Health Sector Cybersecurity Coordination Center or HC3) released a report detailing how Royal ransomware has been used to target the healthcare sector.
While Royal ransomware is a relatively new strain, discovered by security researchers in September 2022, cyberattacks on healthcare organizations have become the norm for malicious threat actors. Since the beginning of the pandemic, cyberattacks targeting healthcare have increased dramatically. From 2019 to 2021, the healthcare industry saw an increase in breaches and leaks of more than 50%, according to the Healthcare Cybersecurity Report by the Herjavec Group.
The consequences of these attacks can be severe. In addition to financial losses, healthcare organizations may experience disruptions to their operations, putting patients' lives at risk. In some cases, attackers have stolen sensitive patient information, which can be used to extort additional payments or sold on the Dark Web.
The report from the HC3 says:
"Royal is an operation that appears to consist of experienced actors from other groups, as there have been observed elements from previous ransomware operations. While most of the known ransomware operators have performed Ransomware-as-a-Service, Royal appears to be a private group without any affiliates while maintaining financial motivation as their goal. The group does claim to steal data for double-extortion attacks, where they will also exfiltrate sensitive data."
The cybercriminal group's ransom demands range from $250,000 to over $2 million.
After compromising a network, Royal follows a typical pattern seen from other groups. They deploy Cobalt Strike for persistence, harvest credentials, and move laterally through the network until encrypting the files. The report notes that it originally used BlackCat's encryptor but ultimately switched to Zeon and generated a ransom note identified as similar to Conti's:
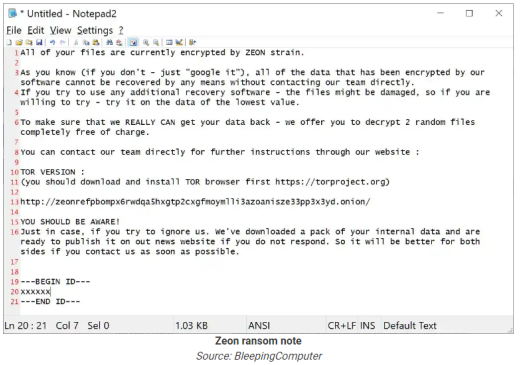
Mike Parkin, Senior Technical Engineer at Vulcan Cyber, discusses Royal ransomware:
"Threat actors have been adopting the same business plans that legitimate organizations use for a while, and this is really another example of that. One some levels, this Royal group superficially feels like a private equity startup, in that it appears closely held and focused on a very specific market.
Though an important takeaway in the HHS-H3C note is that they still consider phishing, credential theft, and abuse of known exploits the highest threats."
How can organizations better defend themselves against these type of attacks? Darren Guccione, CEO and Co-Founder at Keeper Security, shared his thoughts with SecureWorld:
"The first line of defense against ransomware is often strong and unique passwords for all applications, websites and systems—on every device. Password managers can help this effort by creating high-strength, random passwords and enabling strong forms of two-factor authentication to protect against remote data breaches.
We recommend a zero-trust security architecture to prevent unauthorized access to infrastructure and to track permitted access and activity across every user, device and location. Successful cybersecurity plans must also include education for all users on privacy, internal controls and how to spot phishing attacks and malicious links."
For more information on Royal ransomware and the healthcare sector, see the report from the HC3, or the original story from Bleeping Computer.





