How To Incentivize Open Source Maintainers for More Security
IT Toolbox
JUNE 19, 2023
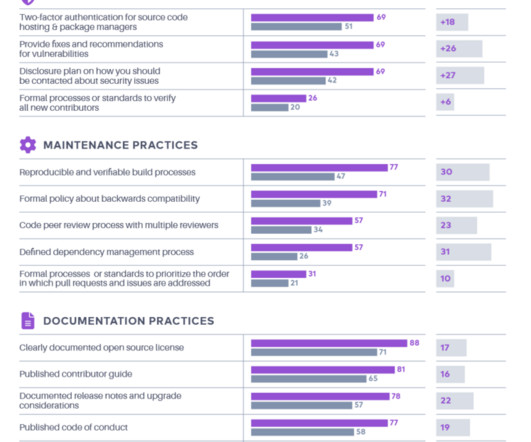
How can incentivizing maintainers improve your open source software security? The post How To Incentivize Open Source Maintainers for More Security appeared first on Spiceworks.


















































Let's personalize your content