Researchers from security firm ZecOps recently developed a trojan proof of concept (PoC) tool that can fake a shutdown on iPhones, allowing malware to secretly continue living on the device.
Typically, malware can be removed from iPhones with a simple restart, but this new technique hooks the shutdown and reboot process, meaning the device never actually gets turned off.
If malware stays on the device, threat actors can utilize microphones and receive sensitive data via a live network connection.
The researchers from ZecOps have dubbed the technique "NoReboot," which does not exploit any flaws on the iOS, meaning it can't be patched by Apple.
'NoReboot' on iPhones
Normally, when an iPhone is completely turned off, the screen is black, camera off, 3D Touch disabled, sounds are muted, notifications off, and vibrations are silent.
However, this tool developed by ZecOps injects code onto three iOS daemons to fake a shut down by disabling these indicators.
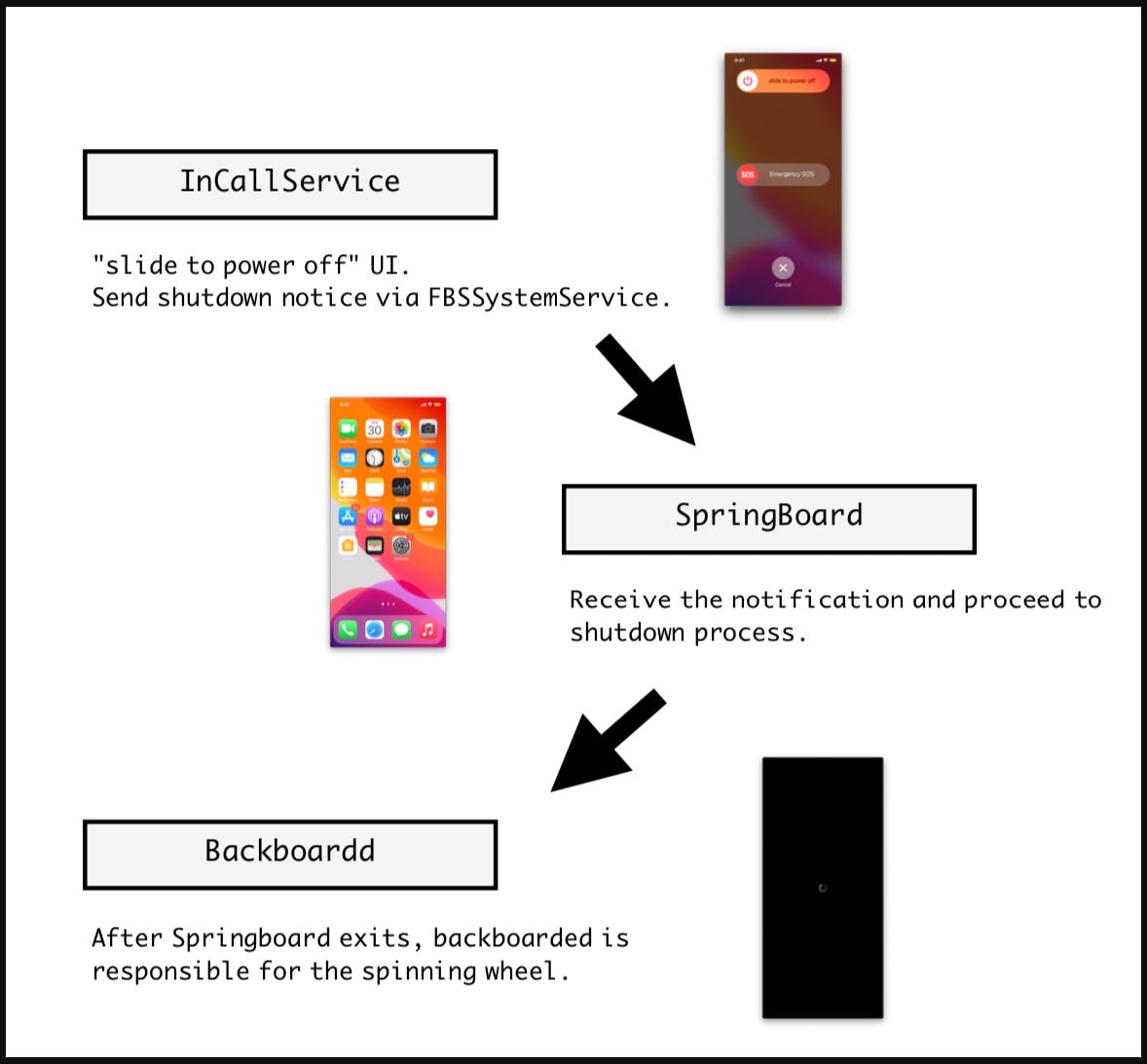
Bleeping Computer describes the process:
"The trojan hijacks the shutdown event by hooking the signal sent to the SpringBoard (user interface interaction daemon).
Instead of the expected signal, the trojan will send a code that will force SpingBoard to exit, making the device non-responsive to user input. This is the perfect disguise in this case because devices that enter a shutdown state naturally no longer accept user inputs."
ZecOps provides a visual representation of the process:
Bleeping Computer continues to describe the process:
"Next, the BackBoardd daemon is commanded to display the spinning wheel that indicates the shutdown process is underway.
BackBoardd is another iOS daemon that logs physical button click and screen touch events with timestamps, so abusing it gives the trojan the power to know when the user attempts to "turn on" the phone.
By monitoring these actions, the user can be deceived to release the button earlier than they were supposed to, avoiding an actual forced restart."
And ZecOps describes the last step of the process:
"The file will unleash the SpringBoard and trigger a special code block in our injected dylib. What it does is to leverage local SSH access to gain root privilege, then we execute /bin/launchctl reboot userspace.
This will exit all processes and restart the system without touching the kernel. The kernel remains patched. Hence malicious code won't have any problem continuing to run after this kind of reboot. The user will see the Apple Logo effect upon restarting.
This is handled by BackBoardd as well. Upon launching the SpringBoard, the BackBoardd lets SpringBoard take over the screen."
The user will have gone through the entire fake shutdown process when the screen comes back on, with no indications that the process was illegitimate.
ZecOps has even shared a video of what the whole process looks like:
Lastly, ZecOps reminds iPhone users that they should never trust a device to be completely turned off.
Apple created a new feature called Find My, with iOS 15, that allows users to track their phone even while it's turned off. So, if malware was installed on your phone, threat actors could be listening even while your phone might appear to be completely turned off.
For more information on this PoC, see the research from ZecOps.





