CrowdStrike 2024 Global Threat Report: 6 Key Takeaways
Tech Republic Security
FEBRUARY 26, 2024
Identity-based and social engineering attacks still take center stage, according to the CrowdStrike 2024 Global Threat Report.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Tech Republic Security
FEBRUARY 26, 2024
Identity-based and social engineering attacks still take center stage, according to the CrowdStrike 2024 Global Threat Report.

SecureWorld News
JULY 27, 2023
A new study from Uptycs has uncovered an increase in the distribution of information stealing malware. The 17-page report has a wealth of information, including the impact of stealers, the lifecycle of a stealer, the workflow of a stealer, and statistics around the stealers trending in 2023.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

SecureWorld News
JUNE 15, 2023
Verizon has released its 2023 Data Breach Investigations Report (DBIR), the 16th annual publication providing an analysis of real-world data breaches and security incidents. The report often includes recommendations and best practices to mitigate the risks identified in the data. So what did they find?

CIO Business Intelligence
DECEMBER 19, 2023
When making decisions about network access, businesses need to be aware of and assess the security implications associated with network technology to help keep their digital assets protected. Cyber hygiene best practices include device security , cyber security education , and secure networking strategies.

The Verge
JANUARY 26, 2021
Government-backed hackers based in North Korea are targeting individual security researchers through a number of means including a “novel social engineering method,” Google’s Threat Analysis Group is reporting. Hackers set up a network of Twitter accounts and a cybersecurity blog.

Forrester IT
MAY 18, 2016
New social media scams and marketing #fails are common fodder for water cooler banter today - even a recent episode of HBO's Veep ran a joke where the President blames a Chinese cyberattack for sending an ill-advised tweet. But social media cybersecurity issues are far from a laughing matter, and it's time we all take notice.

SecureWorld News
OCTOBER 3, 2023
And one of the most successful and increasingly prevalent ways of attack has come from social engineering, which is when criminals manipulate humans directly to gain access to confidential information. Social engineering is more sophisticated than ever, and its most advanced iteration is the topic of today's discussion: deepfakes.

SecureWorld News
JULY 16, 2021
Now you can add this one: nation-state cyber actors using the platform to distribute malware and conduct espionage operations. This group used various malicious tactics to identify its targets and infect their devices with malware to enable espionage.". They are as follows: Social engineering. "In Privacy violations?

The Verge
NOVEMBER 3, 2021
“Sideloading is a cyber criminal’s best friend and requiring that on iPhone would be a gold rush for the malware industry,” according to Apple senior vice president Craig Federighi, who delivered a dramatic speech at Web Summit 2021 declaiming the security risks if Apple were required to let users sideload apps.

Network World
JULY 10, 2016
Omni Hotels & Resorts has reported that point-of-sale systems at some of its properties were hit by malware targeting payment card information. The malware was designed to collect certain payment card information, including cardholder name, credit/debit card number, security code and expiration date,” Omni said. “The

SecureWorld News
MAY 20, 2020
The 2020 Verizon Data Breach Investigations Report (DBIR) has the answers. 2020 DBIR cybercrime report and key statistics. Verizon says it sifted through more than 150,000 security events from the last year and that 3,950 of the confirmed data breaches met the quality standards necessary for the report. Why is this?

CTOvision
DECEMBER 19, 2014
As for me, the most important thing the FBI report tells us all is that organizations should take steps now to enhance their defense. Here is what the FBI had to report : Update on Sony Investigation. After discovering the intrusion into its network, SPE requested the FBI’s assistance. But the DPRK was involved. Washington, D.C.

SecureWorld News
OCTOBER 20, 2021
For an increasing number of companies, part of that conversation is happening in quarterly and annual reports. This includes the 2021 annual report at Accenture. Accenture annual report: risks we face from cyberattacks. The report from the consulting giant details the most exciting news upfront.

Network World
MARCH 20, 2017
Social engineering is the strongest method of attack against the enterprise’s weakest vulnerability, its people. In 2015, social engineering became the No. 1 method of attack, according to Proofpoint’s 2016 Human Factor Report. These successful social engineering methods often use phishing and malware.

CIO Business Intelligence
OCTOBER 20, 2022
In fact, CIO has reported that it takes only a few minutes for experienced hackers to set up a social engineering attack against enterprises (and their managed service providers) that consider themselves to be secure and protected. Don’t log in to WiFi networks you don’t trust. Double check.

Dataconomy
FEBRUARY 22, 2024
IBM’s 2023 Cost of Data Breach report shows customers bear damages as companies pass costs through increased prices. Types of Cyber Attacks Ransomware A potent malware, Ransomware is now the preferred tool for cybercriminals. In 2023, Cloudflare reported a 117% spike in these attacks.

SecureWorld News
JULY 16, 2021
Now you can add this one: nation-state cyber actors using the platform to distribute malware and conduct espionage operations. This group used various malicious tactics to identify its targets and infect their devices with malware to enable espionage.". They are as follows: Social engineering. "In Privacy violations?

SecureWorld News
JUNE 6, 2023
Malware and attackers can "break in" in various ways. These attacks can come from malicious instructions, social engineering, or authentication attacks, as well as heavy network traffic. Social engineering has its tells, though. If you detect a phishing email, make sure to avoid all links, and report them!

SecureWorld News
NOVEMBER 12, 2020
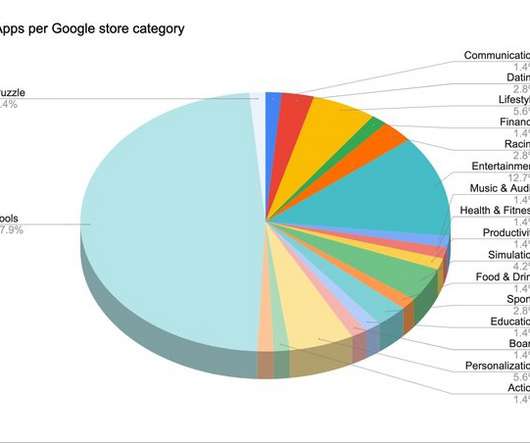
The European Union Agency for Cybersecurity (ENISA) just published its Threat Landscape 2020 report. First, however, let's look at the top 15 cyber threats organizations face right now, according to the report: Malware. Trends in Malware attacks. 46,5%_of all malware in e-mail messages found in ‘.docx’
SecureWorld News
OCTOBER 1, 2021
Winning a prize is one of life’s sweetest rewards—unless that prize is malware in disguise. This social engineering trick is exceptionally successful, considering users might feel more comfortable sharing information to a website in their local language,” reads the report. More than 200 apps were infected.

SecureWorld News
OCTOBER 27, 2021
But according to a report by a Florida-based news station, PAX transactions could come along with more diabolical intentions than a simple digital payment. Federal law enforcement are investigating suspicious activity of malware and data transfers connected to PAX's payment system. FBI raids PAX warehouses. Why was U.S.

SecureWorld News
APRIL 11, 2023
No charging station is safe, apparently, as the FBI is warning travelers looking to charge their devices in airports, hotels, and coffee shops that "juice jacking" is a thing—as bad actors are using public chargers and even free cables and charging plugs to infect phones and other devices with malware.

SecureWorld News
JUNE 18, 2023
According to a recent report , bots accounted for a staggering 47.4% Out of the 13 countries examined in the report, seven exhibited levels of bad bot traffic, surpassing the global average of 30.2%. Spreading malware: Bots play a role in distributing malware, such as viruses, trojans, and ransomware. Stats on bots 1.

Cloud Musings
DECEMBER 14, 2014
A mid-year breach report from Risk Based Security and the OSF [4] cited that 59% of reported attacks were in the business sector, followed by 16.1% The majority of these attacks are due to hacking, fraud and social engineering. Malware is malicious software created for egregious objectives. Most Active Malware Today.
SecureWorld News
MARCH 1, 2023
According to the latest report by the international Anti-Phishing Working Group (APWG), Q3 2022 was the worst quarter for phishing attacks the consortium had ever observed, with the number of recorded attacks exceeding 1.2 Urgency is a scammer's best ally, too. Yet another step in prepping for the attack is to proofread the email.

SecureWorld News
MAY 7, 2023
They're typically carried out via email, messaging apps, and social media, and are masked as sent from trustworthy sources like banks and governmental organizations. In the recruitment world, phishing attacks trick recruiters as well as candidates into revealing sensitive information, such as their Social Security numbers and passwords.

Dataconomy
JUNE 27, 2023
Protecting against external threats Cyber hygiene acts as a shield against external threats that aim to compromise the security of your devices and networks. Avoid infected devices Be cautious when connecting to unknown or potentially compromised devices, such as public computers or untrusted networks.

SecureWorld News
OCTOBER 29, 2021
TrickBot operation leaves millions of systems infected with malware. Collaborating with a network of knowledgeable cybercriminals, TrickBot's design led to millions of computers all over the world becoming infected with this Trojan malware—and no industry was safe. Attorney Bridget M. RELATED] Why Did the U.S.

CIO Business Intelligence
JULY 17, 2023
According to the 2023 Verizon Data Breach Investigations Report (DBIR), the majority of cyber attacks are led by organized criminals looking to disrupt business and steal data to sell. Malware Distribution: Cloud exploitation can involve hosting or distributing malware through cloud-based platforms or services.

ForAllSecure
APRIL 26, 2023
of polled executives report that their organizations' accounting and financial data were targeted by cyber adversaries.” Common Types of Cyber Attacks Common techniques that criminal hackers use to penetrate systems include social engineering, password attacks, malware, and exploitation of software vulnerabilities.

SecureWorld News
SEPTEMBER 12, 2023
On June 14, 2019, Taylor Swift posted a seemingly random string of text to her social media accounts: gxgjxkhdkdkydkhdkhfjvjfj!!! into YouTube pulls up another Taylor Swift music video, " The Man ," which came out nearly a year after the initial social post. But Swifties knew better. Like most hard things, security is a team effort.

SecureWorld News
MAY 1, 2022
They may also provide a hacker with confidential information or access to the enterprise network. They should account for training and tracking travelers and reporting security incidents. Various common scams used to steal valuables can help hackers deliver a malware payload or access an employee's device.

CTOvision
DECEMBER 19, 2014
See the interview here: Tactics Not Malware Are the Story. Most corporate hacks we see are focused on either customer data (credit cards, medical records, social security numbers, passwords, bank account information, email addresses) or company proprietary documents. It is different because the networks were torched.

Galido
DECEMBER 28, 2018
Today, more than any other time in the past, people are committed to using laptops, tablets and phones to facilitate everything in their daily lives, from business to school to social needs. Computer networks give numerous opportunities for cyber attack. Stop Malware Attacks and Online Identity Theft. Why Should You Care?

Galido
FEBRUARY 25, 2020
As a matter of fact, it was reported that each cyber attack costs small business owners $200,000 on average, which is more than enough to put many out of business. Not only are companies installing external firewalls to safeguard their networks, but they are adding an internal firewall as well to reduce the chances of insider attacks.

TM Forum
NOVEMBER 9, 2021
Simultaneously, households became more dependent on networks for entertainment, to remain connected with loved ones, and for vital services such as shopping, healthcare and education. Network-based gaming is highly QoS sensitive, but even for downloaded games run on consoles, gamers increasingly want to interact with others while gaming.

Dataconomy
OCTOBER 18, 2023
F-Secure, a renowned cybersecurity firm, has delved into the depths of SpyNote and released a report shedding light on its workings. When this Android package (APK) is installed, it discreetly places the SpyNote malware on the device, gaining access to Accessibility services. SpyNote, however, does not end there.

SecureWorld News
OCTOBER 30, 2023
It serves as a vessel for various strains of malware, including ransomware, and underlies data-stealing campaigns that target large organizations and individuals alike. According to Verizon's 2023 Data Breach Investigations Report (DBIR), a whopping 74% of breaches involve a human element, which is exactly what phishing aims to exploit.

Dataconomy
OCTOBER 11, 2023
If you think that your servers that are not connected to any network in a local environment are safe, you are wrong because tailgating attacks, an old but effective way threat actors use to access data or information of a company, can still target your sensitive data. The process of a tailgating attack typically involves several steps.

Dataconomy
JUNE 12, 2023
Use encryption and VPNs Avoid phishing and malware Be careful with social media and public Wi-Fi. Virtual private networks, or VPNs, are services that establish a safe connection between your device and a distant server while concealing your IP address and location from prying eyes. Educate yourself and others.

Vox
SEPTEMBER 28, 2023
While many people might think of Russian state-sponsored hacking groups when it comes to infiltrating social media platforms, there’s actually a global network of hackers participating in an underground economy where things like Facebook and Instagram accounts are commodities.

Galido
MARCH 19, 2019
These areas of IT include general IT and technology, security, IT feeds, cloud computing, data center, mobile, social media, tips and tricks, virtualization, and operating system and software blogs. Slashdot is a social news website that originally billed itself as “News for Nerds. Malwarebytes. Help Net Security.

CTOvision
MARCH 18, 2016
Thanks to the professional, virtuous work of security researchers Chris Valasek and Charlie Miller and some fantastic reporting on this research by Andy Greenberg of Wired Magazine , we have long known that theoretical hacks against cars are no longer theoretical. Bob Gourley. They are real.

Galido
MAY 1, 2019
These areas of tech include general IT and technology, security, IT feeds, cloud computing, data center, mobile, social media, tips and tricks, virtualization, and operating system and software blogs. Slashdot is a social news website that originally billed itself as “News for Nerds. Malwarebytes. Help Net Security.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content