New cybersecurity research is revealing interesting details about how organizations and ransomware operators interact with each other following a successful attack.
And there is a lot at stake, especially for the organization.
Spencer Fane cyber attorney Shawn Tuma painted a clear picture of this during a SecureWorld Remote Sessions webcast:
"I cannot think of any other risk that businesses regularly face where the CEO can go to sleep tonight and lay their head on their plush, beautiful pillows, with the company running well, production operations going—and then wake up tomorrow morning to find they're completely out of business because of an event that happened overnight, which is possible in a ransomware attack."
Many organizations are forced to pay the ransom to stay in business. Tuma's clients often use Coveware to do so, a company that is essentially a middle-man to negotiate between victims and ransomware operators.
Coveware collects and shared tremendous data on ransomware trends, and here are three of them happening now.
Ransomware trend #1: ransom demands are getting cheaper
The chart below shows that the average and median ransom payment decreased by 34% and 55%, respectively, in Q4 of 2020, finally coming off their peak which occurred in Q3 2020.
Ransom demands remain significantly higher, however, than in previous years.
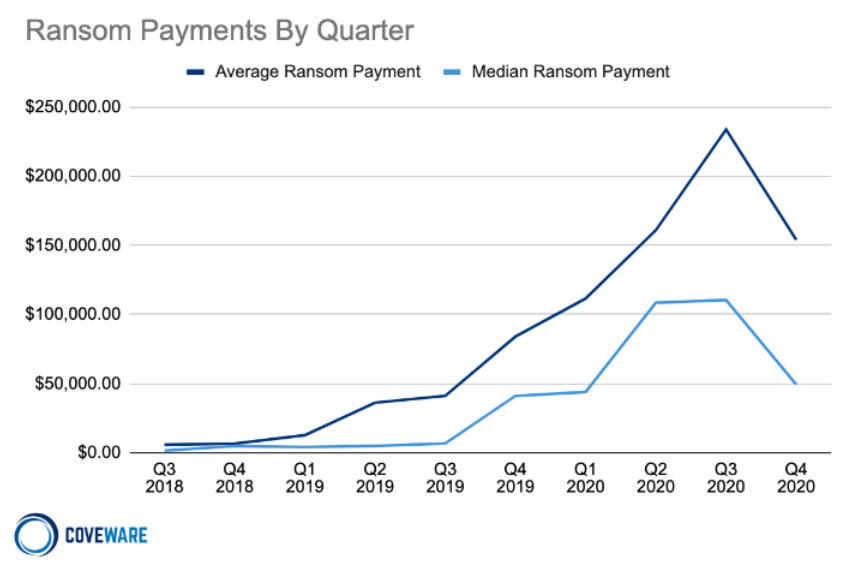
Coveware says there could be a few reasons for the sudden decline at the end of 2020, with the main reason being that more victims of ransomware attacks are finally saying "ENOUGH" and making the decision to not pay cybercriminals' extortion demands.
Researchers say that ransomware operators are still focused on exfiltrating data from organizations and threatening to publish it if the organization refuses to pay the ransom.
However, with experience comes knowledge:
"With more companies falling victim, more are having the opportunity to constructively consider the trade offs, and are increasingly choosing not to pay. Attacking the raw economics of the cyber extortion economy from multiple angles is the best way to retract the volume of attacks. When fewer companies pay, regardless of the reason, it causes a long term impact, that compounded over time can make a material difference in the volume of attacks."
Despite this, Coveware notes the risk/reward characteristics for the cybercriminals remains in their favor, with high profit margins and a low chance of being arrested.
Ransomware trend #2: ransomware gangs having trust issues
Another trend highlighted in Coveware's recent report is that ransomware groups are losing the trust of an increasing number of organizations.
Word is getting out that some ransomware operators will publish your proprietary data, instead of destroying it, even if you pay the ransom.
And during Q4 2020 and Q1 2021, there has been a noticeable uptick in cases where ransomware victims face "irreversible data destruction," including reports of entire servers or data shares that are being permanently deleted with no way of retrieving the data.
"Ransomware actors are typically attentive when it comes to deleting data, as they know victims are only incentivized to pay for a tool if the data is still there, and merely encrypted. The uptick in haphazard data destruction has led some victims to suffer significant data loss and extended business interruption as they struggle to rebuild systems from scratch. It remains unclear whether these events have been outliers or a symptom of less experienced bad actors handling the attack execution."
Ransomware trend #3: phishing becomes top attack vector
The third trend to highlight is that phishing attacks have recently overtaken RDP (remote desktop protocol) as the top attack vector for ransomware.
Coveware reports this is the first time since tracking RDP incidents that it has not been the top attack vector.
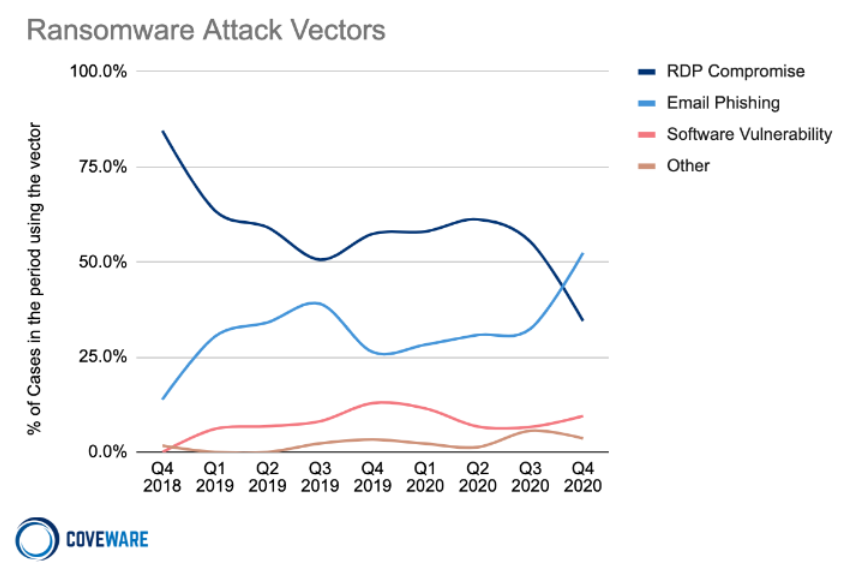
RDP, a secure network communications tool from Microsoft designed for remote management and problem solving for individual users, has constantly been under fire from cybercriminals because it gives access to an organization's network. But it is no longer the top ransomware attack method organizations face.
"Precursor malware, like Trickbot / Emotet, favor widespread phishing campaigns as their primary delivery mechanism. Unlike ransomware malware, these threats possess worming capabilities that allow them to stealthily proliferate through a high volume of enterprise networks. There they lay down secure footholds that are sold further down the supply chain to ransomware actors."
Also, the company notes there will likely be a "reshuffling" of attack vectors due to the Emotet takedown.
Organizations still paying ransomware
Despite the trend showing the decrease in average and median ransomware payments, a lot of organizations are still making the ransom payment; approximately 60% of organizations are doing so.
Cyber attorney Shawn Tuma says he knows why, based on what he sees after successful attacks:
"There was this old excuse from companies that, 'Our data is not that important, nobody knows who we are, or nobody wants what we have.' But modern ransomware changed that. You want your data, you want access to your networks. And if you don't have it, you're willing to pay money to get it back. The hackers figured that out."
This falls right in line with Coveware's research, which shows that the majority of ransomware targets are small businesses.
These small businesses are less likely to have a dedicated IT or security staff or access control policies. And they often believe they are not a prime ransomware target.
[RELATED: Shawn Tuma on the ransomware lifecycle at SecureWorld New England conference, Feb. 18, 2021]




